Millions Targeted by 'Invisible' Malware: How to Protect Yourself
Millions of people may have been infected by malicious code bundled into images in online ads.
You and millions of other web users may have fallen victim to a malvertising threat you didn't even know was there — and that you don't need to click to become infected.

Security researchers at ESET yesterday (Dec. 6) disclosed a newly found malvertising campaign they're calling "Stegano." The malicious ads have been flowing around the web since 2014, although they were mostly placed on small sites with little to no traffic. The ads use steganography, the art of hiding information in images, in order to sneak malware past online-ad safeguards.
In October, the Stegano creators were able to place their ads on popular news sites with millions of monthly readers, according to ESET. The alterations to displayed ads made by the malware is nearly impossible to see with the human eye. Users can protect themselves by not using Microsoft Internet Explorer, by running antivirus software, by updating or limiting Adobe Flash Player and by running an ad blocker or browser-script blocker.
MORE: Malvertising Is Here: How to Protect Yourself
According to ESET researchers, the malvertising creators placed malicious JavaScript in the part of the ad coding that determines the transparency of pixels in the banner ad. While that will change the image's look, ESET says the modification is minimal and can be easily missed by humans looking at the ads. That has allowed the malvertising to live on unencumbered for so long.
It also helps that Stegano will first use a known (and patched) flaw in Microsoft Internet Explorer to analyze a user's computer before deciding whether to load. Computers that have certain security tools installed or are running the browser on a virtual machine — two signs that the target computer might belong to security researchers — will not fall victim to the attack, according to ESET.
"If the script does not detect any signs of monitoring, it redirects to the Stegano exploit kit's landing page, via the TinyURL service," the ESET researchers said in a blog posting. "The landing page loads [an Adobe Flash Player] file that is able to exploit three different vulnerabilities (CVE-2015-8651, CVE-2016-1019, CVE-2016-4117), depending on the version of Flash found on the victim’s system."
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Stegano will then install itself on a machine and do another check, this time for antivirus software commonly used by consumers and businesses. If any is found, the installation process stops. But if not, then Stegano will install spyware, backdoors and "various trojan downloaders" on the machine.
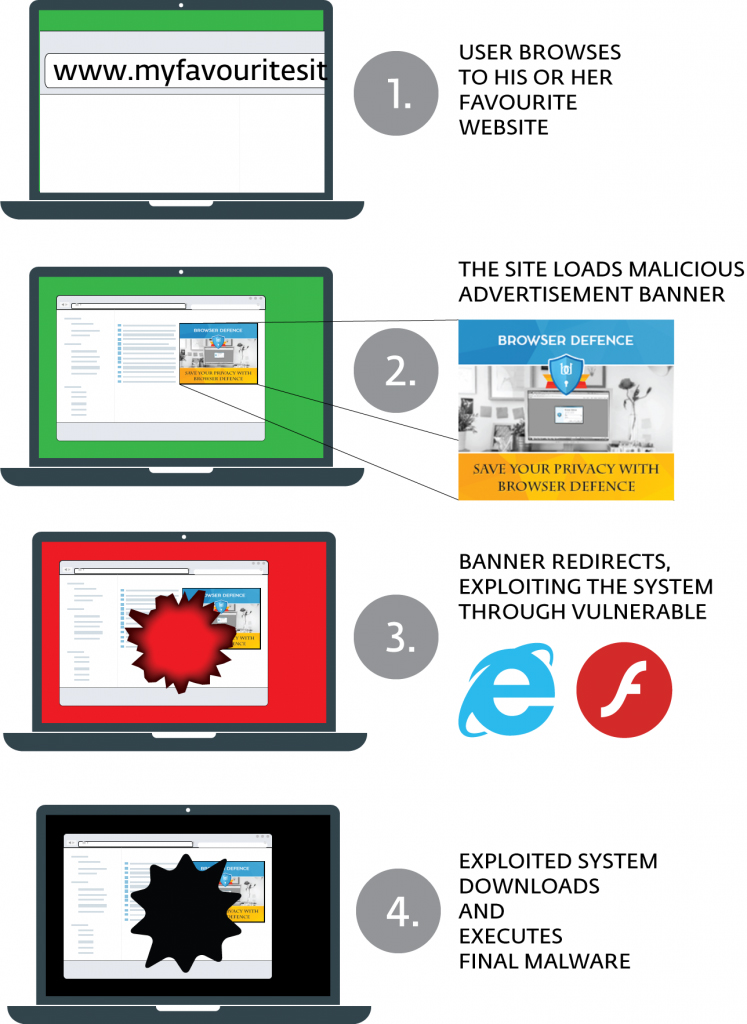
Malvertising used to be limited to malicious websites or sites that had been compromised by criminals. In the past year or so, malicious ads have exploited online ad networks so that they are now often placed on reputable, high-trafficked sites with no other security issues. Online ad networks have deployed countermeasures to catch malvertising before it spreads, but Stegano stands out for its abilities to avoid these new detection methods by hiding in plain sight.
According to the researchers, Stegano ads promote a product known as "Browser Defence" and software called "Broxu." Either way, ESET says, the campaigns are "practically identical." You don't need to click on them to become infected.
ESET didn't say which sites were hosting the ads, but noted that many of them were "news websites visited by millions of people every day."
Regardless, now is probably a good time to brush up on your security chops to protect yourself against the threat. To give yourself the best chance of sidestepping Stegano, install antivirus software, don't use Internet Explorer (Edge is much better), patch or disable Adobe Flash Player, and consider running an ad blocker.
Don Reisinger is CEO and founder of D2 Tech Agency. A communications strategist, consultant, and copywriter, Don has also written for many leading technology and business publications including CNET, Fortune Magazine, The New York Times, Forbes, Computerworld, Digital Trends, TechCrunch and Slashgear. He has also written for Tom's Guide for many years, contributing hundreds of articles on everything from phones to games to streaming and smart home.
-
Guillaume-RepairItAll Wow, and I really want to turn off adblocker on legitimate sites, but this kind of attack really blows.Reply
