10 Easy-to-Use Security and Privacy Tools
These 10 security and privacy tools are both effective and user-friendly.


For a long time, people thought that technologies couldn't be both secure and easy to use.
But that's changing: These 10 tools are not only intuitive and simple; they also maintain your security and privacy. Whether you're an activist, a businessperson, a traveler in a foreign country, or you simply want to feel a bit more secure in your Internet use and communications, these tools are for you.
TextSecure
Why you can trust Tom's Guide
Many companies claim that their instant-messaging mobile apps are secure, but a good number of them fail to deliver on that promise. (We're looking at you, Snapchat.) Even the more secure ones won't work unless the people you want to talk to are using the same app.
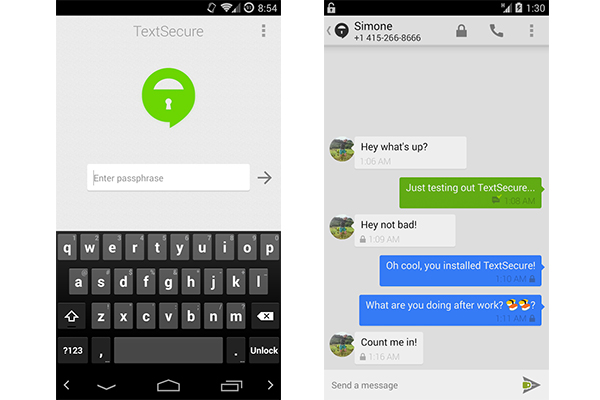
That's why we like free Android app TextSecure. With TextSecure installed, when you send SMS and MMS messages to other TextSecure users, your messages will have end-to-end encryption. The app doesn't work when you text non-TextSecure users, however; in that case your messages transmit as usual, without the encryption. Either way, you can keep texting the way you're used to doing.
MORE: How to Use TextSecure to Send Encrypted Text Messages
Wickr
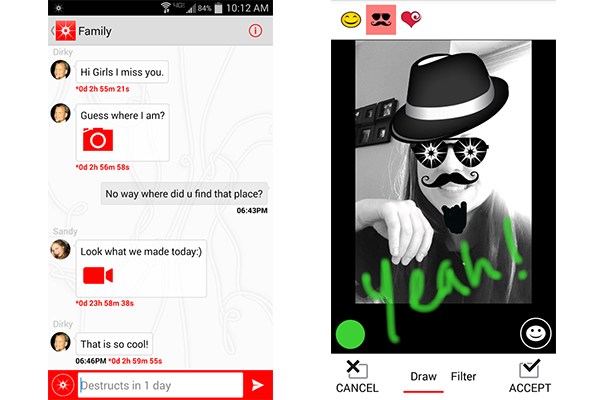
If you're really serious about secure mobile messaging, you'll want to check out Wickr, a free messaging app for Android and iOS that encrypts your messages right on your mobile device. People you communicate with also need to have Wickr installed, but all the data that passes through Wickr's servers is encrypted with a temporary key so that even Wickr can't read your messages.
MORE: How to Use Wickr Privacy App
Aviator
To paraphrase Melisandre from Game of Thrones, the Internet is dark and full of perils. To make your Internet browsing a little safer, we recommend the free Aviator browser from WhiteHat Security.
Aviator looks similar to Google Chrome (it's based on the same open-source Chromium browser), but it comes with tough security settings enabled by default. For example, it blocks cookie tracking, ads and JavaScript (you'll have to manually start each YouTube video) and doesn't store search history or passwords.
MORE: Aviator: Hands-On with the Most Secure Web Browser
Antivirus programs
This one's a no-brainer. If you haven't installed one of the best antivirus software programs on your computer, you're missing out on the easiest way to keep your computer safe.
Most paid antivirus programs for PCs have very intuitive interfaces and easy setups, and can be set to automatically scan for and remove malicious programs from your computer.
When it comes to free PC programs, the usability isn't quite as good. You probably won't be getting the same caliber of protection, but they're still relatively easy to set up.
MORE: Best Free Antivirus Software
Antivirus programs for Macs vary wildly in quality, but for the best Mac antivirus software, offering a balance of usability and interface, you may want to look at offerings from Avast, Sophos or Intego.
And don't forget to get protection for your Android device -- check out our list of the best Android antivirus apps. (But please read our explainer on why iPhones don't need antivirus software.)
Cryptocat
Cryptocat is an option for people who need to communicate securely from a variety of devices. This open-source encrypted chat service works in the Chrome, Firefox, Safari and Opera Web browsers, as well as natively on OS X and iPhone. (There's currently no Android version.)
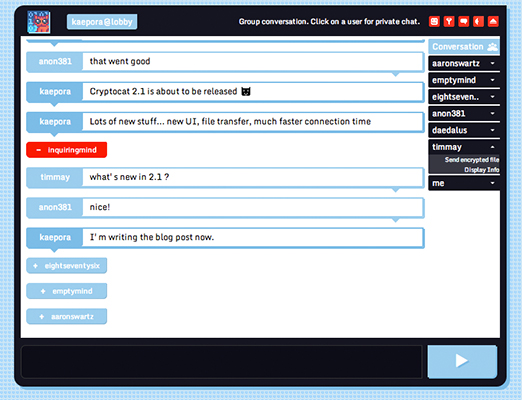
Though Cryptocat did have a few problems with security several years ago, many security experts agree that Cryptocat has turned itself around and become a trusted messaging service. Now, like Wickr, Cryptocat's encryption is designed so that even Cryptocat's creator can't read the messages transmitted through its servers.
If you want to securely send instant messages from your computer as you work, Cryptocat may be the service for you.
Smartphone encryption
Text messages, emails, Web search histories, shopping history and financial data — your smartphone contains a lot of sensitive information. That's why many smartphones now come with a means of encryption — in other words, formatting the device so some or all of your data is stored in a scrambled form. This will make it more difficult for phone thieves, cybercriminals and investigators to read your data.
For Apple users: All iOS devices, from the iPhone 3GS and up, come with some level of hardware-level encryption baked into the phone's circuits. The unique encryption keys (to decrypt your data so you can read and interact with it) are also stored on your device.
To complete this protection, all you have to do is set a passcode on your iOS device's lock screen. This passcode will restrict people from accessing your phone's encryption keys.
MORE: How to Encrypt Files on iOS
On Android phones and tablets, it's a little trickier for now. Unlike iOS, Android doesn't automatically encrypt a device when a password is set, but if your device is running Android Gingerbread 2.3.4 or higher, you can easily enable it. This, too, will require you to set a passcode for your device's lock screen.
MORE: How to Encrypt Your Android Phone or Tablet
The latest versions of both mobile operating systems improve encryption even further. Whereas iOS previously encrypted only some of the files on a device, the newly released iOS 8 encrypts them all. The next major update to Android, already available for software developers and dubbed "L" until an official name is chosen, will also fully encrypt a device when a passcode is enabled.
Two-factor authentication
Now that major data breaches seem to be disclosed every week, using two-factor authentication (also called two-step verification or two-factor verification) is essential to online security.
Don't know what that is? You already use two-factor authentication at ATMs. Your bank card is the first factor of authentication; your PIN, which is not on the card, is the second.
Most online accounts can be unlocked with just a password, which is one factor of authentication. But passwords can be lost, forgotten, stolen or covertly reset, which makes them pretty weak lines of defense.
With two-factor authentication enabled on an online account, anyone trying to log in first enters the regular password. He or she is then prompted to enter a second, randomly generated, temporary number that has been texted to the legitimate account holder's personal mobile phone. (A voice call can also be made.)
Not only does this provide double the security of a password, but two-factor authentication relies on two different types of verification information: something you know (a password) and something you have (a cellphone registered to the legitimate account holder). Cyberintruders will need your cellphone as well as your password in order to access your account.
MORE: How to Turn On Two-Step Verification
Most major online services — including Facebook, Google, Microsoft and Twitter — offer two-factor authentication, though some are not as good as others. Apple, for example, recently expanded the range of iCloud features protected by two-factor authentication after it was discovered that data thieves had accessed celebrities' iCloud backups and stolen personal photos even with two-factor authentication turned on.
SpiderOak
Practically everyone uses cloud storage these days. But how secure are the files you store in the cloud?
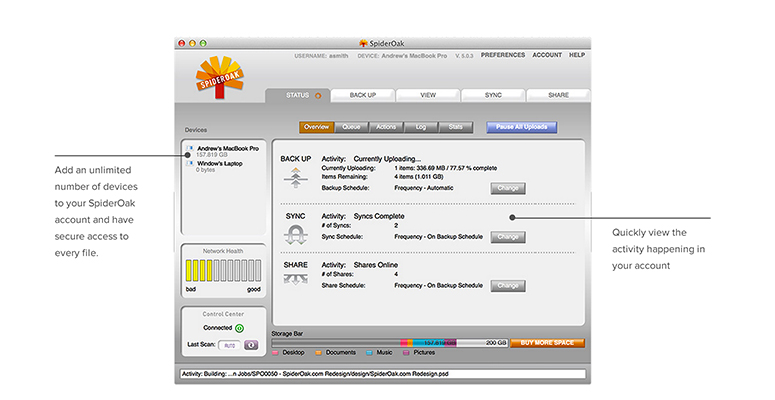
Cloud storage service SpiderOak may not be as easy to use as more widely known systems such as Dropbox or Google Drive; for example, it doesn't have local folder integration as the latter two do.
SpiderOak locally encrypts every document you upload to its systems. Your documents are encrypted before they even leave your machine, and they stay that way, during transmission to SpiderOak's servers and while they're stored there. If anyone were to intercept the transmission or gain access to SpiderOak's servers, all they would be able to see would be the unreadable encrypted versions of your documents.
RedPhone
Ever since the very first leak by Edward Snowden revealed that American telecommunications company Verizon shared telephone-call metadata with the National Security Agency, people have been skeptical of phone communications. If that sounds like you, check out RedPhone, an Android app for making encrypted VoIP (voice over Internet Protocol) calls.
RedPhone, made by the same company that produces TextSecure, also keeps you safe from potential snoops. Anyone listening in to your calls will just hear static, thanks to the app's end-to-end encryption.
But RedPhone makes our list because of its easy-to-use interface. Since you register to RedPhone with your phone's regular number, you can make and receive calls as before. To call another RedPhone user via the encrypted service, just use the app's interface, or dial the person's number with an asterisk at the end. Because RedPhone's calls go over the Internet instead of telephone lines, all calls are completely free.
MORE: How to Use RedPhone for Android
Guest Wi-Fi network
This one isn't a product but rather a useful tool that you can set up with many home wireless routers. To increase your (and your family's) security, set up a second, "guest" Wi-Fi network. This way, you won't be handing out the password to your home network to everyone who stops by.
MORE: How to Secure Your (Easily Hackable) Smart Home
If you have any "smart" appliances, you may want to connect these to a guest network or second network as well, since many smart devices have little to no built-in security. Should these smart appliances become compromised, isolating them on a separate network will keep your other devices safe.
- iOS 8 Adds Serious Security Improvements
- 7 Scariest Security Threats Headed Your Way
- Best PC Anti-Virus Software 2014
Jill Scharr is a staff writer for Tom's Guide, where she regularly covers security, 3D printing and video games. You can follow Jill on Twitter @JillScharr and on Google+. Follow us @tomsguide, on Facebook and on Google+.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Jill Scharr is a creative writer and narrative designer in the videogame industry. She's currently Project Lead Writer at the games studio Harebrained Schemes, and has also worked at Bungie. Prior to that she worked as a Staff Writer for Tom's Guide, covering video games, online security, 3D printing and tech innovation among many subjects.
-
Skylyne I'll just add a couple things to this list that I think should get some credit. These aren't the most user-friendly solutions, but are great for those who are a little more experienced.Reply
BitTorrent Bleep is an end-to-end encryption messaging service that also hosts encrypted VOIP calls. It is currently in public Alpha testing, so expect some bugs; however, the software functions quite well for being in the early stages. It's currently available on Windows, Mac OS, and Android. One of the nicest features is there is no registration necessary; you can use the application in "Incognito" mode, and pick a username with no personal information needed.
I've been using Bleep since the day of the public Alpha release (Sept. 17), and there haven't been many notable issues. My only gripe is about their VOIP call quality; the audio sounds like it's over-compressed at times, and one side of the conversation will drop out at random. Then again... this application is still in Alpha testing, so I'm not complaining just yet. Also, according to BitTorrent's blog, "Android users will need to set the app to “Wi-Fi Only” unless you have an unlimited data plan; this is only for the time being while we iron out an issue related to battery and data-plan."
The Blackphone is a nice tool that was released in June, and is running a custom version of Android 4.4.2 known as PrivatOS. It was the love child of GeeksPhone and SilentCircle, which are both security minded companies. The phone is unlocked for all GSM carriers. -
phil42 please remember! the agencies that monitor these services operate procatively. any of these programs could be trojans.Reply -
Skylyne Do your homework, phil. I've been trying to keep up with all of this stuff for the last few years, and I can confidently say that spy agencies don't need to install trojans under cover of a legit program; they have their ways of spying without all of that hassle. Half of the "secure" means of communication that we use is open to speculation on whether it's secure or not because the NSA is expending a lot of resources on breaking encryption.Reply
Creating a trojan software to trick people is not only a waste of their time, it's a waste of resources; and will hinder them from what they are trying to accomplish with mass surveillance. Not to mention, they pay people to find security flaws in everything that currently exists (breaking software security is easier than creating secure software). They're trying to make everything readable, not trick people into giving them clear text. -
Skylyne The real problem that I have seen with passwords is not the ease of guessing them through brute force attacks; however it's the lack of care that goes into quality passwords, and the ease of obtaining passwords through various tools (ie: key logging, or radio frequency eavesdropping). Numerous attempts at obtaining a more secured method of security have been attempted, but text is so far the only kind that can be done with ease across the board. Using images would be quite difficult for long term uses, as one must retain a particular image for the entire life of the security measure. If the image ever is accidentally modified, becomes corrupted, or is lost due to failed sotrage, then how would one access their restricted content? If you use text as a backup, then it suffers the same security flaw as all text authorisation, and the idea of using images becomes a moot point.Reply
This is why there have been advancements in biometrics, especially in fingerprint security. Unfortunately, it's been proven, consistently, that fingerprint security is far less reliable than text. Recently, there was a headline of using one's "heartbeat" as a means of user authentication. The problem with this? Bluetooth. Well, bluetooth is only one of the problems; there's also device cloning, or capturing a sample of the individual's heartbeat (eavesdropping on BT communications), and then spoofing the heartbeat with a new device. Okay; well, what about RFID chips/tags? That's something that's been hacked endlessly, yet we still use unencrypted RFID everywhere. Do you have a tin foil wallet? I have one...
Security measures that are currently used, or have been considered, tend to suffer from the same problem: nothing is perfect. If someone wants to break that security, they can... somehow. Fortunately, our current high-bit encryption is perfectly fine as it is - at least, that's the speculation, as it's still unknown if the NSA is harbouring a vulnerability in AES encryption, as well as others - but we must remember that the end-user is always going to be the weakest link in a strong chain; like in the case of encryption. The more secure your method is, the less forgiving it has to be. It's a perpetual cycle, and it's going to be a while before we can find a method that won't be cheated by some shmuck with nothing better to do. Eventually, encryption will be crackable with a mobile phone; but until that day comes, that's our best chance.
The only way to stop hackers from doing their thing is to not give them a reason to hack... and that will probably never change. -
Skylyne First off, I never said using pictures for passwords was new; I simply said the methods of use are, for the common consumer with no prior training, appear to be quite fallible. As modern society is so set on certain things, like text passwords, it would make things much more difficult to be implemented in a different way. Personally, I'm okay with using text passwords, and I'd rather keep it that way. I don't know of vary many people who are looking to change that; and that's where things start to fall apart. The consumer public has already been trained on one method; and it will be very difficult to implement a brand new method of authentication without having some sort of transitional period where it is extremely unreliable (thanks to consumer laziness).Reply
Since I've never seen an example of the EPS you are talking about, I can't say whether I find it to be a substantial alternative. Searching for a simpler explanation, or an actual example of such a system, yields very little helpful information. Can you explain it in a different way that doesn't seem to be almost a copy/paste of what I can find on a web search? I'm not saying you did just that, but your post reads very close to what I can find elsewhere; and, frankly, it will go over most people's heads. Since this system is not one I'm currently familiar with, I'm not about to start poking around in the dark, without a proper explanation.
As far as biometrics are concerned, I'd like to see a device that is in use with conjunction; as I've not seen it. I understand that the reason Apple's biometric security is a failure due to its method; however, unless something is directly put into use, the idea is only as good as any other idea. I'm sure there are systems out there using such a method, but I'd like to see what methods might be used to circumvent such security measures.
Even still, all of this falls back onto what I've said before- nothing is perfect. Until we make a security system that is perfect, we should always expect the flaws to be heavily exploitable. -
Aleks Rogal I bypass icloud activation on my iphone with software from this page www.hacktivateiphone.comReply -
Skylyne I love Aviator, but my everlasting bad browsing habit of not signing out of certain websites persists. I use Iron for those, and use Aviator for most everything else.Reply -
PacketMan I am going to add a few things too:Reply
RokaCom : Encrypts your voice and video calls, along with your text messages and photos. When they encrypt your data, it is with keys that only exist on your mobile devices so no more cloud hacks! My doctor friends love it to, since it keeps them HIPAA compliant.
Email : GPG or SMIME. While smime is easier to use after setup, gpg is free and widely used as well. Start telling everyone you know to encryp their email. SMIME is built in to almost every email client as well, and some webmail services (like zimbra) have built in options to allow you to use it even in webmail.