How 40,000 Home Routers Got Hijacked (and How to Fix Them)
An infection of over 40,000 routers gives consumers and office IT managers a teachable moment in changing system default settings.

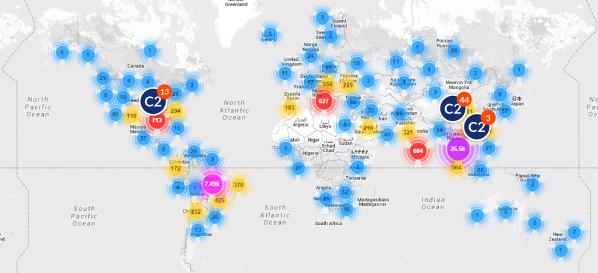
Wi-Fi routers may be easy to get up and running, but more than 40,000 small-office and home routers in 109 countries -- including the United States -- have fallen victim to hackers in attacks that could have been prevented with minimal effort. Internet security firm Incapsula reports that these compromised routers are being remotely operated to send massive amounts of traffic to websites to take them offline.
According to Incapsula, these orchestrated distributed denial-of-service (DDoS) attacks have been going on since at least December, when researchers first found evidence that malware called MrBlack had infected routers and gathered them into a botnet, a network of infected Internet-connected machines secretly working together.
MORE: Your Router's Security Stinks: Here's How to Fix It
This botnet of weaponized routers is made up primarily of small & home office routers made by Ubiquiti, a San Jose, California-based network-hardware maker. The vast majority of these devices -- 40,269 in total so far -- were easily hijacked and infected because the default administrative login credentials -- the username and password -- provided by Ubiquiti and the other vendors involved had not been modified after purchase.
Ubiquiti, whose routers are not exactly ubiquitous in the United States, sees 70 percent of its revenue coming from developing countries, including Brazil, Thailand and Indonesia, as well as richer countries such as the Czech Republic. In an emailed statement sent to The Security Ledger, Incapsula said that the well-meaning goals of Ubiquiti may have erred on the side of negligence:
"Ubiquiti Networks tried to do a good thing and bring Internet connection to Third World regions this year. Unfortunately, it's just been discovered that their routers are being actively exploited by hackers to field massive DDoS attacks, due to an overlooked exploit."
As any consumer who has ever set up their own router can attest, Ubiquiti is not the only manufacturer that does not require the user to put unique security settings in place. In fact, they are just one of many players operating by the same poor standards and practices.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The dangers of these routers being kept at system defaults go beyond being used as a pawn in a massive online blitz. Lax behavior puts personal information at risk as well. Owners of these exposed routers are vulnerable to having all communications monitored, and access granted to locally networked devices (such as Internet-connected security cameras and wireless printers).
The MrBlack malware isn't the only piece of software being used to usurp control of these routers -- others have also been found infecting the routers in this particular botnet.
Fortunately, the solution is simple. Incapsula advises router owners to change their routers' default administrative login usernames and passwords. We at Tom’s Guide also recommend more simple steps, including changing your router’s name from its branded default (i.e. "Netgear" or "Linksys") to something more obscure, and making sure your router's firmware is always up to date.
Henry T. Casey is a Staff Writer at Tom’s Guide. Follow him on Twitter @henrytcasey. Follow us @tomsguide, on Facebook and on Google+.

Henry is a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom's Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He's also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
-
zodiacfml that's weird....they don't seem to be selling consumer routers.Reply
routers available on their website are for businesses with SFP ports and Gigabit connections.
their only fault though is that remote login from the web should be disabled by default.
