This $200 Robot Cracks Safe In Just 30 Minutes
For about $200, you can assemble the parts to built a robot that can crack the combination of a home safe in less than an hour.
LAS VEGAS — Using publicly available blueprints, anyone can build a robot that will break into a combination-lock home safe in a maximum of 45 minutes, a team of hackers showed at the DEF CON 25 hacking conference here Friday (July 28).
Their robot, called SparkX, looks like a large Erector set with a motor. It methodically tried one three-number combination after another onstage as the researchers discussed their methods. After about half an hour, it opened the safe, a SentrySafe model that had been bought the day before at a local Home Depot and whose combination the researchers did not know.
The team, led by Nathan Seidle, head of SparkFun Electronics in Boulder, Colorado, has put its design online for anyone to use or improve. You'll need a 3D printer to create some components, but otherwise the parts cost about $200.
MORE: Best Smart Locks
Many combination locks and safes built for the home market have a built-in three-number tolerance to compensate for human inaccuracy. So if a combination specifies 56 as one value, then 55 and 57 will work for that value as well.
This means that for a given combination 25-33-47, you can also dial "close but not quite" combinations such as 24-34-46 or 26-32-49 to open the lock. (Commercial locks aren't as forgiving.)
This three-number spread greatly reduces the number of combinations that need to be guessed. Because of this, the safecracking robot doesn't need to guess one million (100 x 100 x 100) possible combinations on a 100-number combination lock — it needs to try only 33 x 33 x 33 (35,937).
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
It also turns out that one of the three disks in this kind of safe's lock — one for each number in the combination -- has 12 indents along its edge to confuse safecrackers who try to sense tiny differences in resistance to determine when the disk falls into place. That reduces the possible combinations to 33 x 33 x 12.
Applying a couple of other technical weaknesses further reduces the number of possible combinations so that the robot, which takes between 4 and 8 seconds for each attempt, can theoretically crack the code in 45 minutes.

In March, SparkFun livestreamed a YouTube video in which the robot opened a SentrySafe safe in 41 minutes. (Seidle's wife had bought it for him on Craigslist for $20 after the original owner forgot the combination.)
Unlike that model, the newer unit Seidle had on the DEF CON stage also came with a fail-safe tubular lock, similar to that used in a bicycle U-lock, as a backup to the combination lock.
"But," Seidle said, "if you know anything about tubular locks, you know that the casing from a Bic ballpoint pen works really well in opening them."
As he spoke, Seidle said he was nervous that the combination wouldn't be found before his presentation's 50-minute slot was over. But at about the half-hour mark, the machine beeped and Seidle opened the safe. From our vantage point, we couldn’t see whether he used the Bic pen as well.
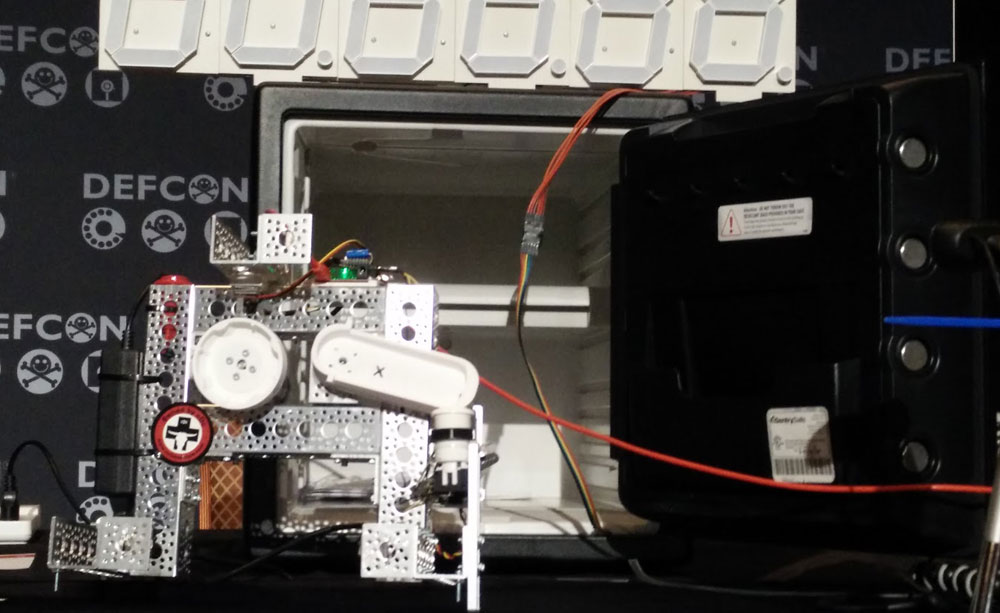
The successful combination that the robot determined was 51-36-93. Seidle's team looked in the box the safe came in and found that the "proper" combination was 52-33-93, indicating possibly even more tolerance than presumed.
In case anyone's worried about the security of their combination-lock safes, bear in mind that other kinds of safe might not be any better. Seidle played a video showing that a keypad-entry safe could be opened by simply holding a magnet at the right spot.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

