'POODLE' Web Flaw: How to Fix Your Browser
A newly disclosed flaw in Web encryption threatens all secure online communications. Fortunately, there are easy ways to avoid it.


Heartbleed, Shellshock ... POODLE?
The latest serious flaw to be discovered in open-source software, disclosed yesterday (Oct. 14) by Google researchers, may not have a scary name (it's an acronym for Padding Oracle on Downgraded Legacy Encryption). But whether you run Windows, Mac OS X or Linux, POODLE directly impacts the way your Web browser interacts with secure websites.
An attacker snooping on your Wi-Fi traffic could use POODLE to capture the "cookies" that authenticate your secure Web connections, such as to Facebook or to a bank website, then re-use those cookies to take over your accounts, at least temporarily.
MORE: 12 Computer-Security Mistakes You're Probably Making
Fortunately, there are ways to make sure that doesn't happen, even as you wait for the major browser makers to roll out patches for POODLE. (You can check your browser for POODLE vulnerability at https://www.poodletest.com/ or https://poodle.io/.)
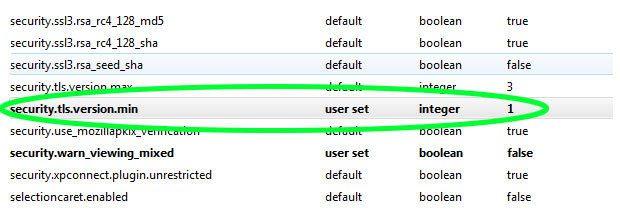
Microsoft Internet Explorer
Click the Tools icon in the top right corner (the icon looks like a gear). Scroll down and click Internet Options. In the resulting pop-up window, select the Advanced tab, then scroll through the list of settings until you reach the Security category. Uncheck Use SSL 3.0, click Apply, and then click OK.
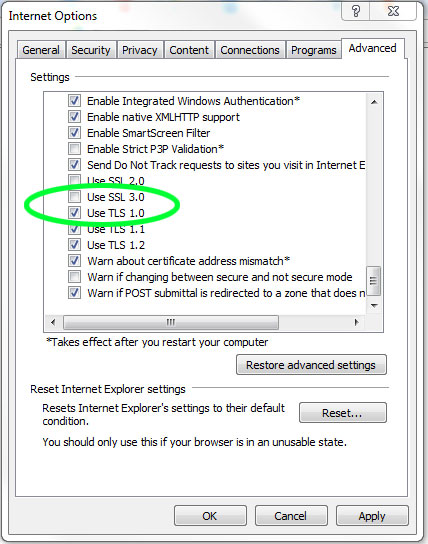
Mozilla Firefox
Type about:config into the address bar and hit Enter or Return. Click "I'll be careful, I promise!" in the resulting warning window. Scroll down the list of preferences and double-click "security.tls.version.min". Change the integer from 0 to 1 and click OK.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
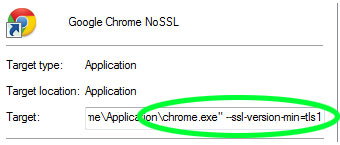
Google Chrome
For Google Chrome, you'll have to temporarily become a power user and use a command line. The instructions are a bit different for Windows, Mac and Linux.
In Windows, first close any running version of Chrome. Find the desktop shortcut you normally click to launch Chrome and right-click it. Scroll down to and click Properties. Click the Shortcut tab. In the Target field, which should end with "/chrome.exe", add a space, then add this: "--ssl-version-min=tls1" (without quotation marks). Click Apply and then OK.
In Mac OS X, first quit Chrome. Open the Terminal command-line application in the Utilities folder (reachable by typing Command+Shift+U). In Terminal, type "/Applications/Google Chrome.app/Contents/MacOS/Google Chrome --ssl-version-min=tls1" (without quotation marks).
In Linux, quit Chrome. Open up a console window and type "google-chrome --ssl-version-min=tls1" (without quotation marks).
Relaunch all those browsers (and in the case of Internet Explorer, reboot the PC), and you should be good to go.
How POODLE makes a mess
POODLE isn't as disastrous as its immediate predecessors, both of which will keep IT administrators patching systems for months to come.
"If Heartbleed/Shellshock merited a 10, then this attack is only around a 5," wrote Robert Graham, CEO of Errata Security in Atlanta and the popularizer of the Shellshock nickname.
POODLE takes advantage of flaws built into the SSL 3.0 Web security protocol, first written in 1996 and long since replaced by newer protocols. The problem arises because two computers that want to encrypt their one-on-one communications must first agree on which protocol to use; if one party insists on SSL 3.0, the other must follow.
Because of bad math in the SSL 3.0 encryption procedures, a determined attacker sharing the same local network as a target need run through only 256 permutations to crack and steal session cookies, which browsers use to maintain authorized connections. That would expose social networks, online email accounts and possibly online bank accounts to the hacker hidden in the crowd at the local Starbucks.
SSL 3.0 is still used because Internet Explorer 6, which shipped with Microsoft Windows XP and had a five-year reign as Microsoft's flagship browser, is still used. IE6 can't use SSL 3.0's successor, TLS 1.0. Hence, millions of Web servers keep SSL 3.0 alive just so that millions of Windows XP users who never upgraded to IE 7 or IE 8 can see those sites.
It might not be so terrible to simply disable SSL 3.0 at the server end as well as at the client (Web browser) end. Network-reliability provider CloudFlare last night did so by default for all its clients, after determining that only 0.09 percent of its traffic used the protocol. (CloudFlare clients can turn SSL 3.0 back on manually.)
"Hopefully, this will be the straw that breaks the camel's back and gets us to abandon obsolete protocols like SSLv3," wrote Matthew Green, a cryptography expert at Johns Hopkins University, on his blog. "But nobody every went bankrupt betting on insecurity. It's possible that 10 years from now, we'll still be talking about ways to work around POODLE and its virulent flesh-eating offspring."
- iOS 8 Security Tips to Keep Your Data Safe
- Best Free PC Antivirus Software 2014
- 7 Scariest Security Threats Headed Your Way
Paul Wagenseil is a senior editor at Tom's Guide focused on security and gaming. Follow him at @snd_wagenseil. Follow Tom's Guide at @tomsguide, on Facebook and on Google+.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
lopezjavier Missing for your browser list is Safari. How would anyone disable SSL 3 on Safari?Reply -
Paul Wagenseil lopezjavier, I honestly don't know. I've been searching for that, but can't find any instruction from Apple. There's no obvious setting in Safari. I suspect that because Safari is so deeply hooked into the OS, fixing this may require a full system update.Reply -
Shelama In my Mac OS 10.6.8, the Terminal command to fix Google Chrome returns only "/Applications/Google: No such file or directory"Reply
The Google Chrome app is, indeed, right where it belongs in the App folder.
-
EricTheByteMan For Firefox, that setting may break Firefox 33+Reply
For all versions of Firefox use Mozilla's own plugin to prevent SSL3 connections:
https://addons.mozilla.org/en-US/firefox/addon/ssl-version-control/ -
Paul Wagenseil lopezjavier: as I suspected might happen, Apple fixed POODLE for Safari by pushing out a security update for Mountain Lion and Mavericks. Yosemite users get the patch built in; Lion users are out in the cold, and would need to update to Yosemite (or Mountain Lion or Mavericks if they can find an installation image):Reply
http://www.tomsguide.com/us/apple-yosemite-patch,news-19799.html