New 'Petya' Ransomware Attack Spreads: What to Do
Six weeks after WannaCry, a new ransomware worm was spreading rapidly around the world. Fortunately, protecting against it is simple.
Less than six weeks after the massive WannaCry attack, a second Windows ransomware worm made its way around the planet today (June 27).

The ransomware, which we'll call Petya at the risk of being technically incorrect, may be "the worst worm ever seen," according to one expert. There was evidence that it was tied to tax-collection software that the Ukrainian government requires be installed on every workplace computer in the country. Even the radiation monitors at the ruined Chernobyl nuclear power plant were said to be affected.
While Petya itself appears to be quite sophisticated, its ransom-collection system is primitive, leading some security experts to speculate that Petya may be part of a state-sponsored cyberattack on Ukraine. However, an Israeli security researcher based in Boston may have found a way to stop Petya from spreading.
How to Protect Yourself
If you're a home user, make sure your Windows computers have installed at least the April 2017 Windows Update security-patch bundle from Microsoft. If you're not sure, go to Control Panel (Windows 7) or Windows Settings (Windows 8, 8.1 or 10), open Windows Update or Updates and Security, and check for recent patches.
Updating the machine fully will provide some degree of protection against today's ransomware worm, which we'll call Petya at the risk of being technically incorrect.
You should also run antivirus software. As of 5:30 pm ET, 39 different antivirus brands detected the ransomware, including Avira, Bitdefender, ESET, Kaspersky, McAfee, Panda, Symantec/Norton and Trend Micro.
MORE: Petya Ransomware: What It Is, Who's Behind It, How to Stop It
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
However, you should not use a personal Windows machine to connect to a corporate or enterprise network using a virtual private network (VPN) — at least not today. That's because the Windows patches won't entirely protect machines on enterprise networks, where even patched machines are being infected.
If the malware gets onto a single machine in an enterprise network, it scans the machine for Windows administrative usernames and passwords. It then uses two Windows administration tools, called PSEXEC and WMC, to infect all the machines it can — which will include many home machines connected to the enterprise server via VPN.
Late Tuesday, Israeli researcher Amit Serper with the Boston-based company Cyberreason said that he might have found a "kill switch" within Petya's code.
"I found a way to stop the malware," Serper tweeted. "Create a file in c:windows called perfc with no extension and #petya #Nopetya won't run!"
Other experts responding to his tweet confirmed that his method seemed to work.
Whatever you do, don't pay the ransom — it probably won't do any good. The ransom note instructs victims to email "wowsmith123456@posteo.net" to obtain the decryption key. But Posteo, an email provider based in Berlin, said it had suspended that address, cutting off communications between the malware operator and his or her victims.
A specter is haunting Europe
One of the first indications of the ransomware worm came from Ukraine, where one of the country's deputy prime minsters posted a photo of a computer screen bearing a DOS screen stating that the computer was reformatting its hard drive.
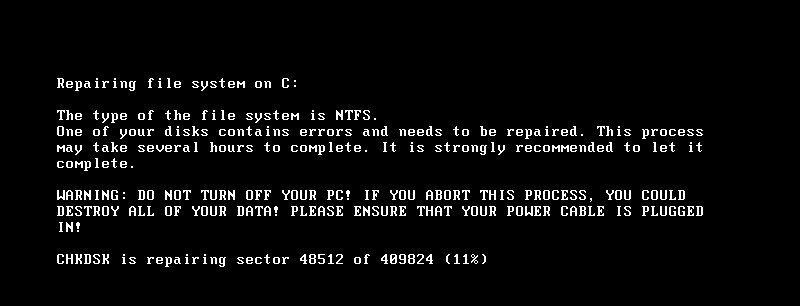
Commenters on Twitter quickly noted that the screen appeared to belong a new form of the Petya ransomware. Romanian antivirus firm Bitdefender identified the new malware as "an almost identical clone of the GoldenEye ransomware family," which in itself is a hybrid of Petya and another form of ransomware called Mischa. (Kaspersky Lab says that the worm may not be related to Petya at all.)
MORE: What Is Ransomware and How Can I Protect Myself?
Most of the initial reports came in from Europe. The Danish shipping line Maersk, the British advertising giant WPP and the Anglo-American law firm DLA Piper confirmed that their internal networks had been infected. The Russian energy company Rosneft also said it had been hit. Other reports came in from Germany, France, India, the Netherlands, Poland and Spain.
Pharmaceutical giant Merck, based in Kenilworth, New Jersey, not to be confused with the German company of the same name, confirmed on Twitter that it was compromised, making it one of the largest affected companies in the United States.
One photo on Twitter, posted by Dutch malware researcher Yonathan Klijnsma, showed all the checkout-terminal screens at a supermarket in an Eastern European country displaying the malware's ransom note.
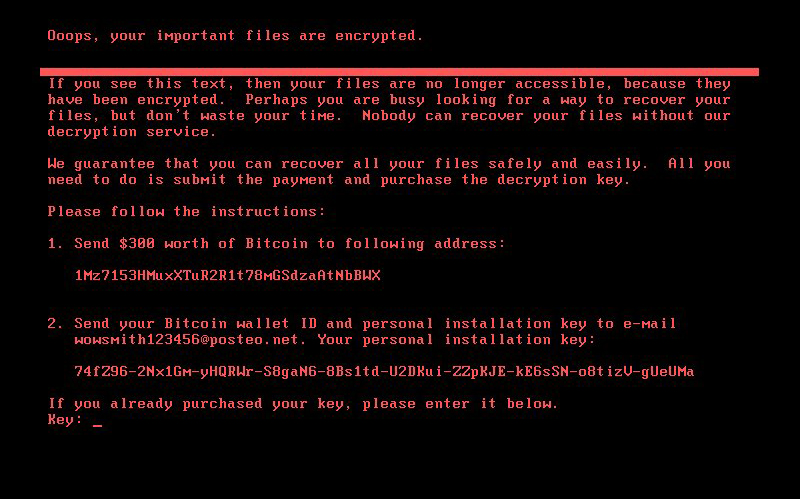
The ransomware note asked victims to pay $300 in bitcoin to a specific Bitcoin address. (That may indicate that the ransomware authors are newbies, as many sophisticated ransomware variants use a separate Bitcoin address for each victim.) As of about 5:30 pm Eastern time, the address had received about $8,000 in payments.
The earliest payment was made at 8:49 am Eastern time. That payer and most other shelled out between 0.12 and 0.13 bitcoins, just about $300. But one clearly angry victim paid 0.0000666 bitcoins, about 16 U.S. cents, from the nonstandard address "1F[***]YouRJBmXYF29J7dp4mJdKyLyaWXW6".
Petya ransomware is especially damaging, as it encrypts not only certain user files, but also the computer's file table and Master Boot Record. The victim will not be able to restart his or her computer.
How Petya spreads
The ransomware, which may be a variant of the Petya/Mischa/Petrwrap/GoldenEye ransomware family, seemed to be using the ETERNALBLUE networking exploit developed by the NSA several years ago, then stolen and posted online several months ago. WannaCry also used ETERNALBLUE, but WannaCry was clumsily made; this variant of Petya (which some researchers insist is not related to the original Petya at all) was crafted by more skilled hands.
"#WannaCry was the warning shot," tweeted a security researcher using the pseudonym zerosum0x0. "#Petya #NotPetya is the real deal by someone who knows what they're doing. Probably worst worm ever seen."
Petya also uses the two aforementioned Windows administrative tools, called PSEXEC and WMC. Some reports indicated that a second Windows flaw that affected Office files was being used to infect networks via phishing emails. That flaw was patched with Microsoft's April 2017 round of updates, but other reports attributed that attack to an entirely different strain of ransomware.
One theory was that infected Office files were being spread by phishing emails. However, Marcus Hutchins, the 22-year-old who single-handedly stopped the WannaCry attack, posited that the malware spread entirely within computer networks.
"All the current infection vectors I've seen would suggest the malware only spreads within an already infected network, therefore contained," Hutchins tweeted.
So how did it get on so many machines? One clue was that all the original infected machines seemed to be running a piece of financial tracking software called MEDoc that is mandatory on all workplace computers in Ukraine, perhaps to combat tax evasion.
Petya "explicitly targets a Ukrainian software package, mandated by Ukrainian government," tweeted British malware expert Kevin Beaumont. Kaspersky Lab thinks that the malware might have come in the form of a fake MEDoc software update.
The MEDoc company itself gave conflicting statements about the situation. It first posted a message in Ukrainian stating "Our server made a virus attack. We apologize for the inconvenience!" (according to Google Translate), then took that down. A subsequent post on the company's Facebook page denied that it was the source of the infection.
The Petya worm could have traveled along corporate networks from Ukrainian subsidiaries to enterprise servers in other countries, some experts hypothesized.
However, other experts pointed out that there were still enough computers globally that had not patched against ETERNALBLUE, or closed the pathways that that exploit travels, to explain Petya's spread.
From Russia with love
The fact that Petya seemed to target specifically Ukrainian software, and that the software seemed to be well made while the payment structure was not, got information-security researchers on Twitter thinking.
"[There's a] development disparity between infection and spread vectors and the payment pipeline ... the targeting and initial entry points for UA ... No f[***]ing way this is criminals," tweeted the pseudonymous zero-day broker and security expert The Grugq.
Ukraine's big enemy is, of course, Russia. The country is fighting a low-level civil war with Russian-backed separatists, has had one of its richest provinces annexed by Russia at gunpoint, and has been the targets of sophisticated cyberattacks in the past, most recently with malware that knocked out several power plants.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
Winkhorst "When the Petya ransomware infects a machine it searches for a folder called "perfc.dll". If it can't find the folder it takes hold of the computer, locking files and part of the hard drive. In the event that it finds the file the ransomware is not able to work."Reply
http://www.telegraph.co.uk/technology/2017/06/28/security-researcher-creates-vaccine-against-ransomware-attack/ -
Paul Wagenseil Reply19871562 said:Does the 'perfc' file actually nullifies the worm?
Supposedly, yes -- it will stop or prevent the encryption process on an individual machine. It won't stop the ransomware from spreading to other machines in the local network.
But we're seeing reports now that adding 'perfc' may not work on Windows 7, and that the person(s) behind the Petya ransomware may have changed the code so that adding 'perfc' doesn't stop new infections. -
Winkhorst By the way, the file needs to be set to "read only."Reply
https://www.bleepingcomputer.com/news/security/vaccine-not-killswitch-found-for-petya-notpetya-ransomware-outbreak/ -
Paul Wagenseil Reply19874269 said:By the way, the file needs to be set to "read only."
https://www.bleepingcomputer.com/news/security/vaccine-not-killswitch-found-for-petya-notpetya-ransomware-outbreak/
Thanks -- I saw that this morning but haven't had a chance to update the story yet. I am also seeing some reports that this immunization method doesn't work on Windows 7, and may not work on newly infected systems because the malware author(s) may have changed the source code.
-
Paul Wagenseil Reply19874189 said:"When the Petya ransomware infects a machine it searches for a folder called "perfc.dll". If it can't find the folder it takes hold of the computer, locking files and part of the hard drive. In the event that it finds the file the ransomware is not able to work."
http://www.telegraph.co.uk/technology/2017/06/28/security-researcher-creates-vaccine-against-ransomware-attack/
Yes, thanks -- that's already in our story.