OnePlus Backdoor Brouhaha: What You Need to Know
A factory diagnostic app is buried in OnePlus phones, which is kind of cool, but it could let a local hacker or malicious app seize control.
UPDATED 10:30 a.m. EST Nov. 15 with comment from OnePlus and promise that EngineerMode will be removed in an upcoming update. Updated again at 2:15 p.m. EST Nov. 15 with comment from Qualcomm.
OnePlus phones, and possibly phones made by other prominent manufacturers, have a hidden Qualcomm debugging app installed that could let a rogue app or a physical attacker take control of the device.

The app, called EngineerMode on OnePlus devices, was discovered by a Twitter user calling himself "Elliot Alderson," after the protagonist of "Mr. Robot." After he posted yesterday about it finding it on a OnePlus 5, other Twitter users said they'd found the same app on handsets made by Asus, Lenovo, Motorola and Xiaomi.
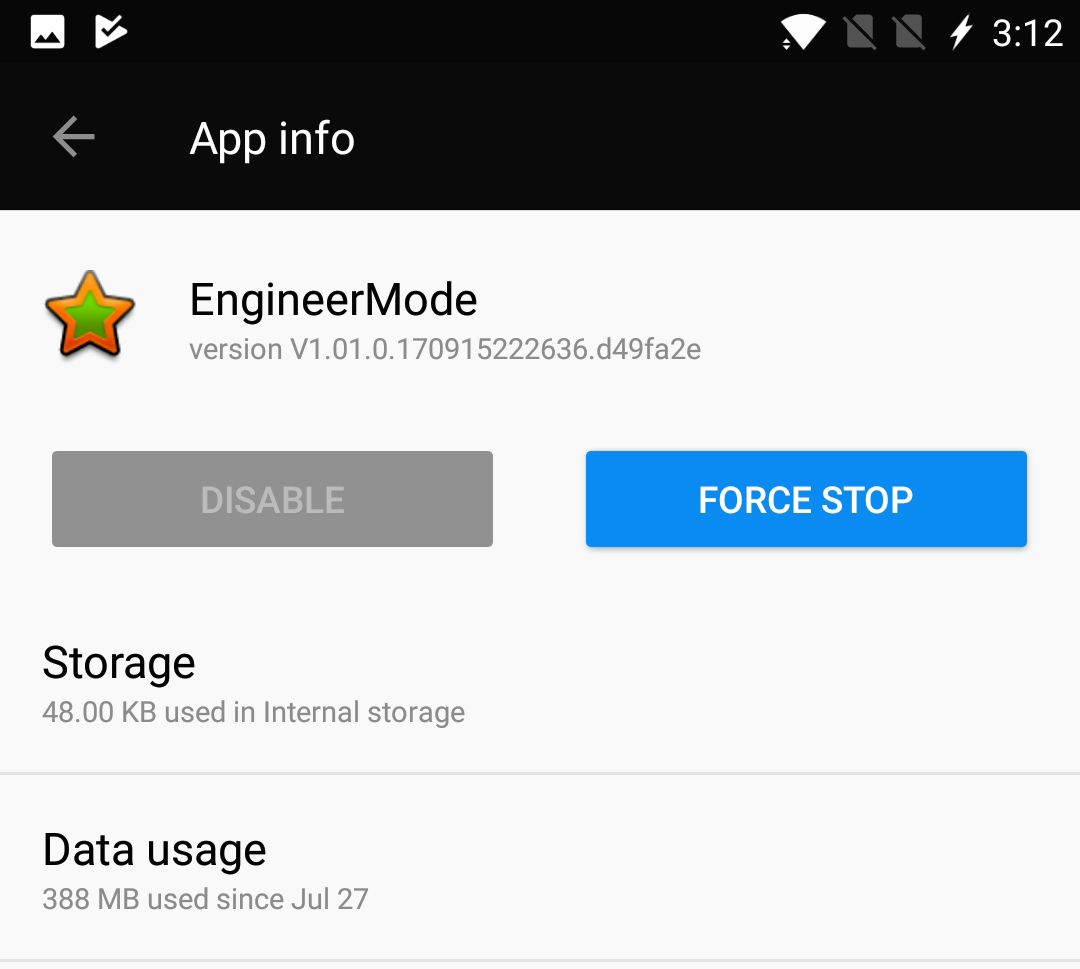
To see if your handset has EngineerMode, go to Settings —> Apps, and then hit the menu icon in the upper right corner of the app list to show system apps. We found it on a OnePlus 5, but not on a Motorola Moto Z2 Play. Android Police found it on all OnePlus models running OnePlus' OxygenOS, but not on a OnePlus One running the original CyanogenOS.
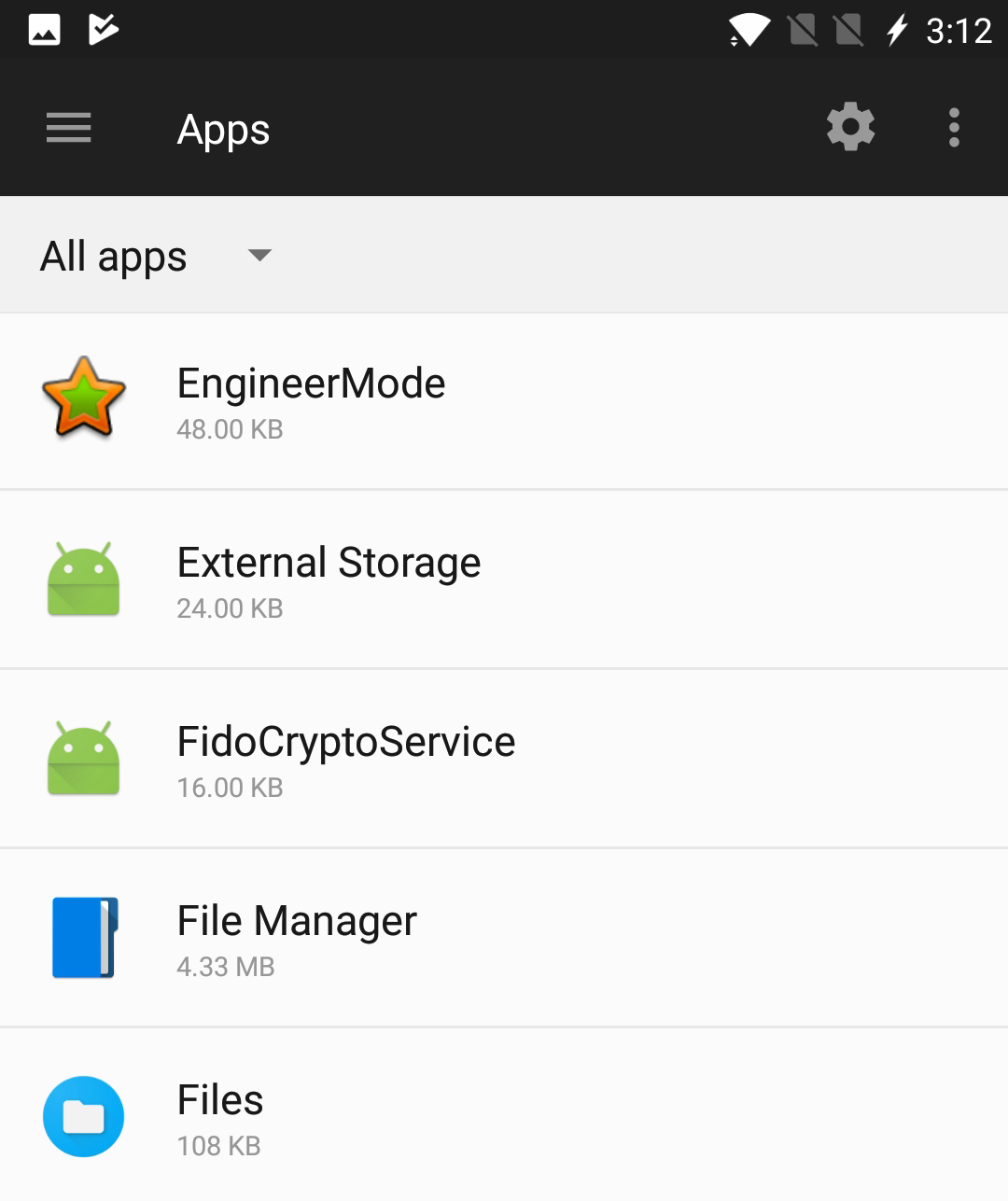
Unfortunately, while you can temporarily kill the app, you can't remove the app without rooting the phone — which, ironically, EngineerMode makes a lot easier.
MORE: Best Android Antivirus Apps
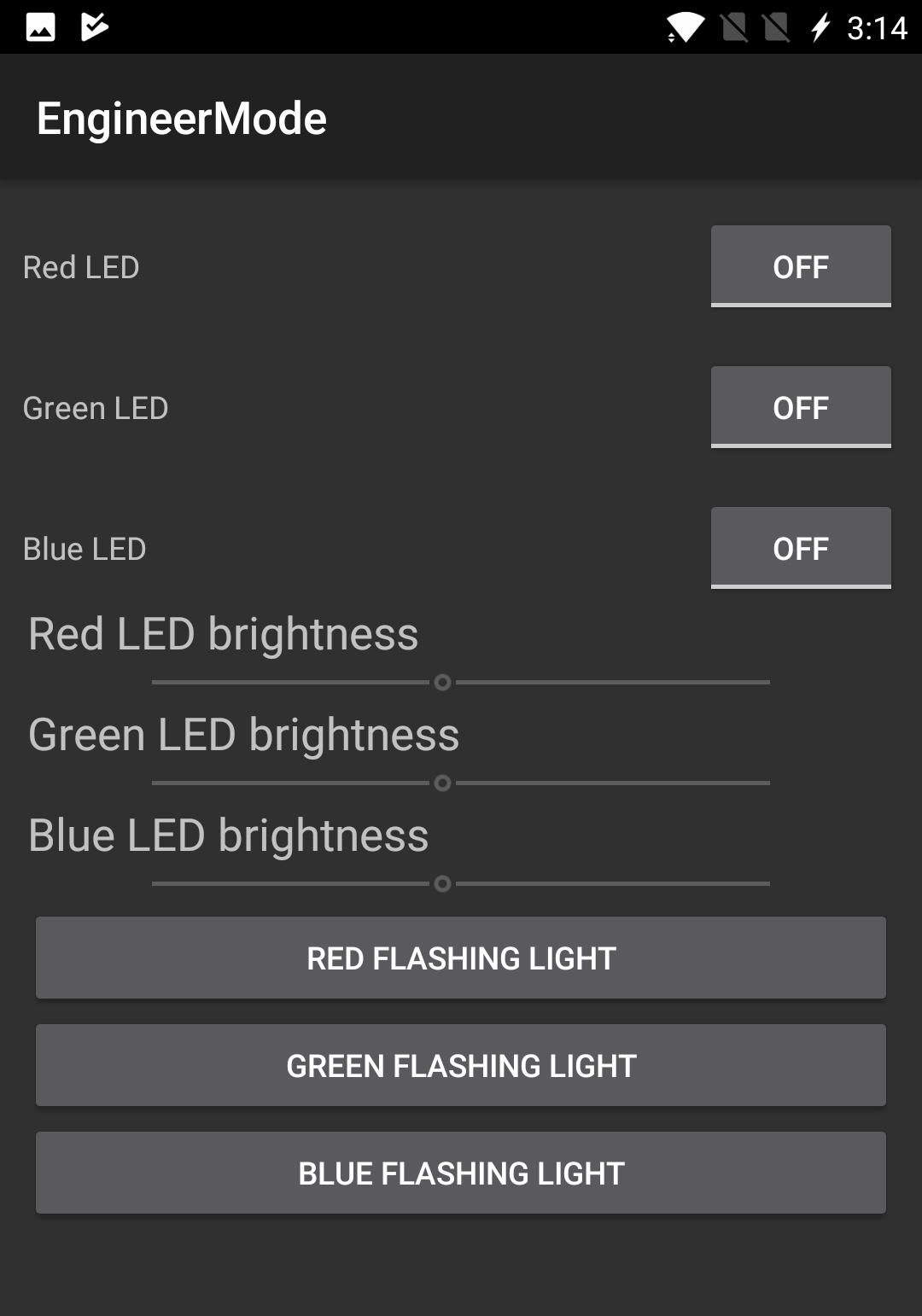
EngineerMode is actually pretty useful for the technically inclined phone user. On a OnePlus phone, you can access and run a long list of diagnostic tests and settings adjustments by dialing the special code "*#808#" in the phone dialer. (Sadly, we couldn't find one that fixes the OnePlus 5 "jelly effect" screen issue.)
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
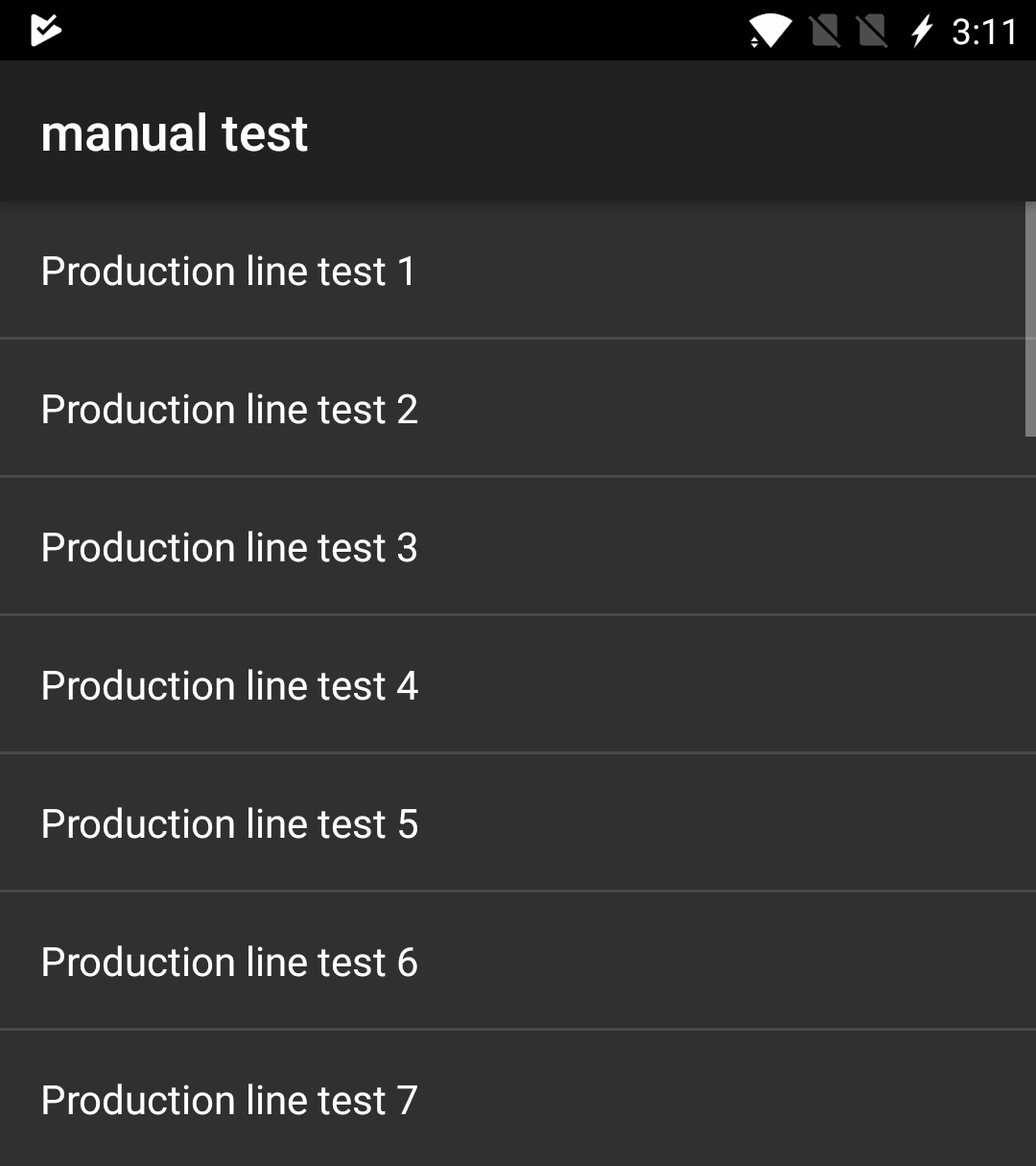
But "Elliot Alderson" said the real power of EngineerMode is unlocked when you access it in ADB (Android Debugging Device Bridge) mode, for which you've got to tether the phone to a computer via a USB cable.
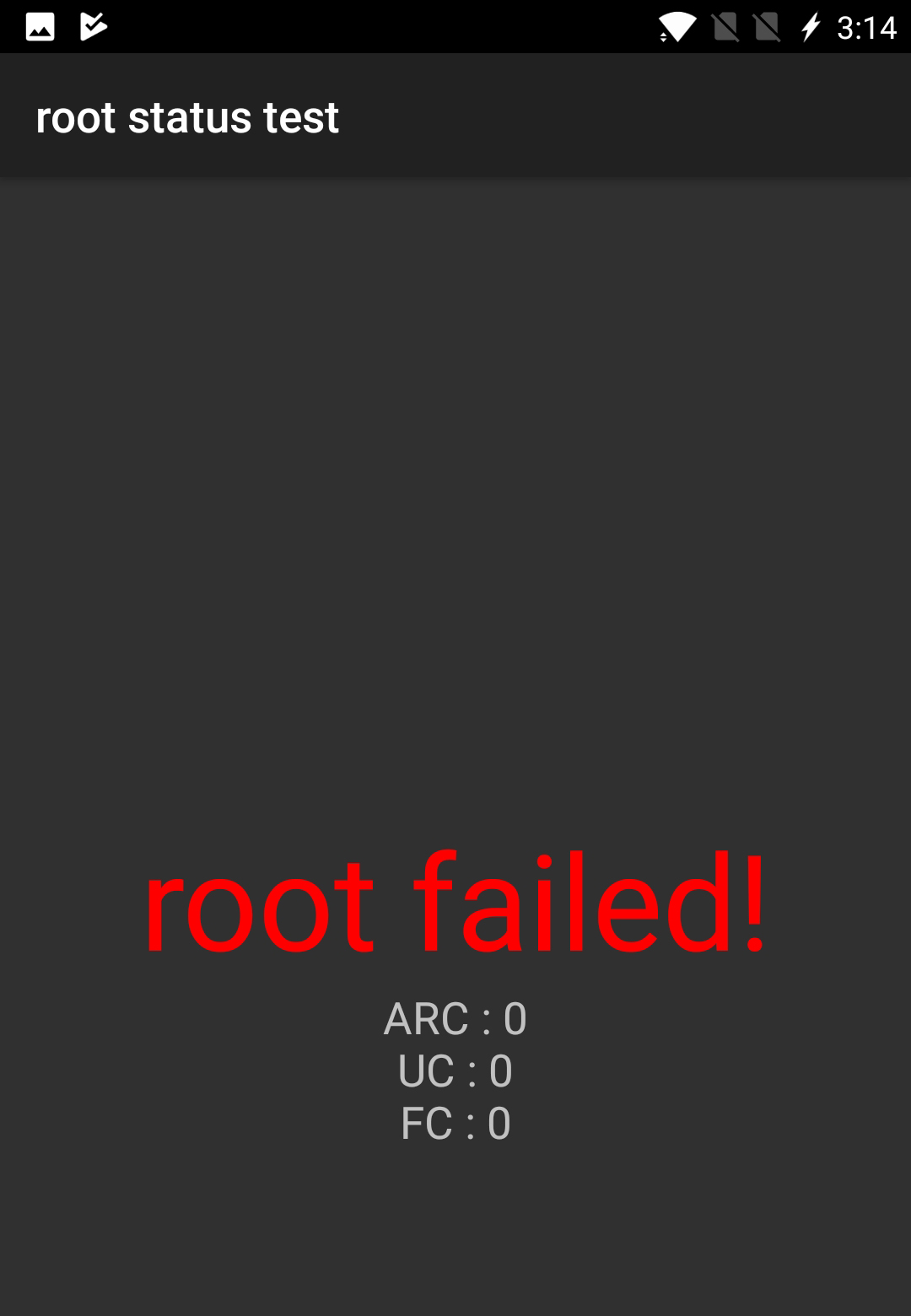
"Elliot Alderson" said if he could get the password to elevate privileges in ADB, he could probably root the phone without unlocking the bootloader. Sure enough, some of his Twitter followers went to work and within hours had the password. It's "angela," which in a delicious coincidence just happens to be the name of the fictional Elliot Alderson's love interest on "Mr. Robot."
The problem is that if "Elliot Alderson" can root his own OnePlus device in a few minutes, so can anyone else with physical access to a OnePlus device — and it's possible that even an rogue Android app could as well. "Elliot Alderson" said he was working on creating such a proof-of-concept app.
Piling on the irony, "Elliot Anderson" said he was motivated to look for OnePlus bugs after learning that OnePlus phones sent an inordinate amount of personal user data back to China. He also said on Twitter that this latest problem wasn't the only interesting thing he found, and promised more to come.
It's likely that OnePlus didn't have any malicious intent, but accidentally forgot to remove EngineerMode from the final customer releases of OxygenOS. Still, it's been in OxygenOS from the get-go, and leaving such a powerful app in there is a pretty big oversight.
You could just root your phone and remove EngineerMode that way, which of course you can now do with EngineerMode installed. But those who don't feel comfortable getting into the guts of their Android device via the command line might want to wait for an official software update — if that ever comes.
Responding to "Elliot Alderson's" tweetstorm, OnePlus head honcho Carl Pei had a terse comment.
"Thanks for the heads up," Pei tweeted last night. "We're looking into it."
UPDATE: In an official OnePlus company blog post later Tuesday, OnePlus OxygenOS Omega Hsu addressed the EngineerMode issue.
"EngineerMode is a diagnostic tool mainly used for factory production line functionality testing and after sales support.
We've seen several statements by community developers that are worried because this apk grants root privileges. While it can enable adb root which provides privileges for adb commands, it will not let 3rd-party apps access full root privileges. Additionally, adb root is only accessible if USB debugging, which is off by default, is turned on, and any sort of root access would still require physical access to your device.
While we don't see this as a major security issue, we understand that users may still have concerns and therefore we will remove the adb root function from EngineerMode in an upcoming OTA [over-the-air update]."
UPDATE: On Nov. 15, Qualcomm provided us with this statement:
"After an in-depth investigation, we have determined that the EngineerMode app in question was not authored by Qualcomm. Although remnants of some Qualcomm source code is evident, we believe that others built upon a past, similarly named Qualcomm testing app that was limited to displaying device information. EngineerMode no longer resembles the original code we provided."
Screenshot credits: Paul Wagenseil/Tom's Guide.
Best Android Antivirus Apps

You'll have to pay $15 per year for Bitdefender Mobile Security, but its excellent malware protection and intuitive user interface make it well worth paying for.

Norton Mobile Security may seem pricey, but its excellent protection, multidevice license and unique privacy features make it a worthwhile investment.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.


