Nest Cams ‘Hacked’ — How to Protect Yourself Now
Most of these Nest camera 'hacks' you hear about are due to reused passwords -- but unfortunately, Nest's interface encourages that.
You've probably heard of the California family that was terrified when a malicious prankster "broadcast" an emergency alert through their Nest home-security camera that North Korean missiles were headed for the United States.

Or maybe you've heard about the jokesters hijacking Nest cameras and directing the cameras' users to subscribe to PewDiePie on YouTube. Or about the 5-year-old in New York who heard a stranger's voice coming out of his family's Nest camera. Or about the guy in Phoenix whose Nest camera told him his password had been compromised.
The mother of the California family said Nest told her that her camera's account credentials had been compromised in a data breach — and not a Nest data breach. That wasn't enough of an explanation for her. "I want Nest and other corporations that get involved in these data hacks to 'fess up to their customers and avoid situations like this," she told the East Bay Times.
That's a little unfair. Scary and bewildering as these incidents may be, the unfortunate truth is that all of these Nest camera hijacks could have been avoided if the Nest camera owners had used unique passwords during the setup process, or turned on two-factor authentication.
But don't let Nest off the hook just yet. This is Nest's fault too, because its smartphone-app account-setup process misleads users into recycling passwords that they've already used before.
MORE: Best Wireless Home Security Cameras
The Nest smartphone app does not tell you that you should use a unique password when you create an account. It does not mention anything about two-factor authentication. (The app does make you use a password of at least eight characters with at least one number and one capital letter, which is good.)
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Misleading the users
In fact, the Nest smartphone app, at least on Android, does something really dumb. It scans your phone for existing email addresses, pops them up on the screen and suggests that you use one of them for your Nest account.
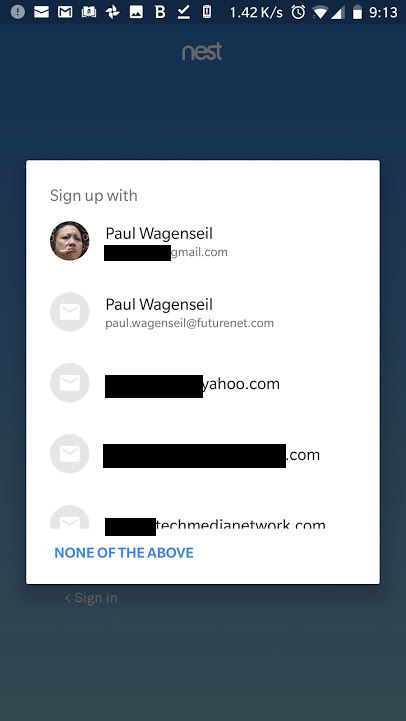
Honestly, if I didn't know any better, I would think Nest already had access to one or more of my email accounts. My first instinct would be to assume that I could use one of those accounts to log into Nest. After all, many websites let you log in with your Facebook or Google credentials instead of making you create a new account.
So I can totally understand why many new Nest users would think it would be fine to create a Nest account using the same email address and password that they'd already used for one of their primary email accounts.
That would be a disaster. Because when you reuse credentials — a password combined with a username or an email address — across two or more accounts, you're setting yourself up to be hacked.
So, so many stolen passwords
Nest has better security than most other brands of home wireless cameras, but all that security doesn't do a bit of good if you're logging into the Nest account with the same username and password you've already used somewhere else. If that other account is compromised in a data breach, then so is your Nest account.
In all likelihood, that's how all these Nest cameras are being hijacked by pranksters. (I don't know if I'd call them hackers, since there's no real technical skill required.)
There are billions of stolen username-password combinations floating around on the internet. A huge cache of them was uncovered just last week. Most of these credentials were stolen in old data breaches years ago, but many of them are still valid.
Some of those stolen passwords and email addresses are probably yours. You can check at HaveIBeenPwned.com, which sifts through billions of known compromised credentials and will tell you if yours are among them. (Don't worry — the site is legitimate, and you can't check your email address and your password at the same time.)
Breaking into your Nest account
You can log into your Nest account through a web browser at https://home.nest.com/. If you have a Nest camera, you can see the camera feed and talk to the people who are in the room with the camera, right through your browser.
So all one of these jerks would have to do is to grab a few of those stolen credentials, go to the Nest browser interface and try combinations until he or she got in.
Nest doesn't put a lot of obstacles in the way. Using a fake email address and bunch of gibberish passwords, the Nest site let me try to log in 10 times before it temporarily blocked me. After a few minutes, it let me try again.
It's just a really tempting target for someone out to make mischief — and also for people with darker motives, such as spying on people and possibly even recording embarrassing footage for extortion purposes.
How to avoid becoming the next victim
When you're setting up a Nest camera, another brand of security camera, or indeed any smart-home device, remember a few cardinal rules:
- Use a totally new password, make it strong and long, and don't use it anywhere else. After all, you wouldn't use the same key to lock your house that you use to start your car.
- Turn on two-factor authentication on every account that offers it. If possible, use an authenticator app such as Authy or Google Authenticator to create the second code instead of relying on texted codes.
- If you have trouble remembering all those passwords, use a password manager. Most are cheap, and some are free.
Image credits: Tom's Guide

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
