Malwarebytes Racing to Fix Its Own Security Flaw
If you use Malwarebytes Anti-Malware to protect your computer, make sure you update it during the next month to patch a nasty flaw.
A good anti-malware program can clean up your computer after a malicious attack, but what happens when your anti-malware program itself is a possible point of intrusion?
The developers of Malwarebytes Anti-Malware, a well-liked anti-malware application, are in the process of patching potentially severe security flaws in both the software's free and paid versions that the Malwarebytes company has known about since November.

If you use the free Malwarebytes Anti-Malware to clean up your computer, or its paid version, Malwarebytes Anti-Malware Premium (which is full-fledged, proactive antivirus software), to protect your computer, make sure you keep it updated assiduously during the next month. Malwarebytes expects to have version 2.2.1 of both its free and paid products ready by the end of this month.
Malwarebytes CEO Marcin Kleczynski took to the company's Unpacked blog to explain the situation. In November, a prominent Google security researcher named Tavis Ormandy privately told Malwarebytes about four vulnerabilities in Malwarebytes Anti-Malware that range between "nearly harmless" and "fairly severe," depending on how you define these things.
Now that 90 days has passed since the private disclosure, Ormandy has gone public, and detailed how the flaws work, in a Google Security Research posting. (Kleczynski was more reticent, for obvious reasons.) The most serious flaw boils down to the fact that Malwarebytes updates its malware signatures using the plain, unencrypted HTTP protocol instead of the SSL-secured HTTPS. (Most antivirus firms do the same.)
This means that a dedicated cybercriminal could launch a man-in-the-middle attack on the data transmission, engineering his or her own phony update and using it to infect or hijack a computer via the very program intended to stop or recover from such attacks. Malwarebytes does encrypt the code that's sent via the unencrypted transmission protocol, but Ormandy showed that the code would be trivial to decrypt.
(For more information about Windows antivirus software, please have a look at our page about the best antivirus software; for other platforms, check out our pages on the best Mac antivirus software and the best Android antivirus apps.)
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The other flaws stem from sloppy coding. All software has access control lists (ACLs) that determine which users or processes can read, write, execute or delete files; Malwarebytes' ACLs are too loose, letting anyone take full control of the program. The software also doesn't adequately limit revisions to its own code, and doesn't limit what kind of customized cleanup processes can be created, making it easy to add or insert malicious code.
In his blog posting, Kleczynski implied that the flaws may not be quite as catastrophic as they sound, saying that "we believe that [inserting malicious code] could only be done by targeting one machine at a time." This would make it an inefficient method of attack compared to mass phishing or malvertising, albeit one perfect for targeted attacks, such as practiced by the National Security Agency or similar intelligence agencies.
Nonetheless, Kleczynski recommended that users of Malwarebytes Anti-Malware Premium enable the self-protection module in the settings menu, which should prevent unauthorized program updates.
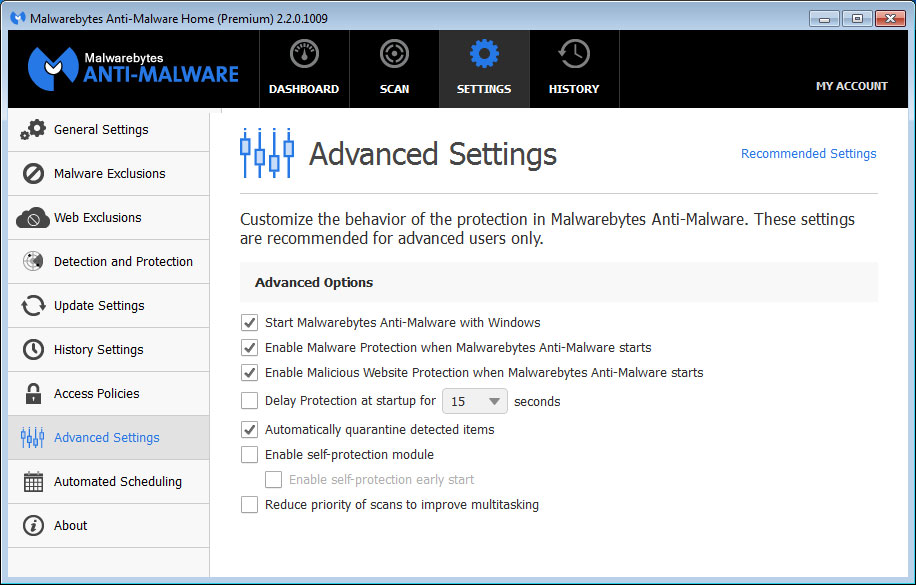
Free users will simply have to wait the three or four weeks until the patch becomes available. If you're extremely paranoid — and you might be justified, since skilled coders will be able to reverse-engineer Ormandy's findings — you can eschew malware signature updates altogether during that time, although doing so would somewhat defeat the purpose of having an anti-malware program.
Bear in mind that the free version of Malwarebytes Anti-Malware is not antivirus software, and does nothing to protect your computer from attack. It's only a cleanup tool. We like Malwarebytes Anti-Malware and recommend its use, but it must always be used alongside a true antivirus program, whether that's Windows Defender or (better yet) a third-party alternative.
Keeping programs up-to-date is usually one of the best defenses against malware, but there's always an exception that proves the rule. In the meantime, Kleczynski encouraged security researchers to keep hunting for bugs, for which they can now receive moderate payouts under the just-launched Malwarebytes Bug Bounty program.
Marshall Honorof is a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.

