Macs Face Double Threat from New Ransomware, Spyware
New forms of Mac ransomware and spyware that anyone can use against enemies or victims have shown up in online criminal marketplaces.
A new strain of Mac ransomware will encrypt files on your Mac's hard drive and demand that you pay about $700 to (maybe) get them back. A strain of Mac spyware created by the same author aims to capture screenshots, ambient audio, user photos and browser history from compromised Macs.

For now, neither piece of malware — unimaginatively named MacRansom and MacSpy — can get past macOS' Gatekeeper security function without triggering a user alert. But that could change as the malware gets more sophisticated, or if someone figures out how to trick users into installing the malware.
To avoid infection by these bugs, Mac users should validate every piece of software that tried to install itself on their Macs, and should run Mac antivirus software to catch what slips past Apple's own defenses.
MORE: Best Mac Antivirus Software
Both MacSpy and MacRansom showed up on a cybercrime forum late last month, and appear to have been created by the same author, according to Bleeping Computer. Compared to their Windows equivalents, they're rather clunky, but they do work — and their existence demonstrates that online criminals think there's money to be made from Mac malware.
With MacRansom, the malware creator seems to be starting a "ransomware as a service" business in which he creates malware, then franchises it out to budding online crooks who do the actual distribution and infection of victim machines. The creator gets a 30 percent cut of all revenue earned in exchange for keeping the malware running properly.
Such arrangements are common in the Windows ransomware world, but this is the first time we've seen this kind of rent-a-ransomware targeting Macs. It permits even technically unskilled people to get involved in cybercrime.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
There is a catch, however, that for the moment would slow the spread of MacRansom.
"Unless you have excellent social-engineering skills to trick the target to download and click on the executable himself, you must have physical access to the target's Mac," the ransomware creator said in a FAQ captured by California information-security firm Fortinet.
That's because, as noted above, the targeted user has to authorize installation of MacRansom. However, other crooks have fooled victims by disguising malware as something you'd need to install to watch a video file or, heaven forbid, use pirated software.
The malware creator could also "sign" MacRansom with an Apple developer certificate, which he could get from Apple with $99 and an email address. If he did so, Apple's Gatekeeper software would let it install, no questions asked. Previous forms of Mac malware have gone this route, including the first known piece of Mac ransomware to appear "in the wild."
Victims infected by MacRansom will have a maximum of 128 files encrypted, and will see a ransom note that they have one week to "buy" decryption software from the ransomware creator for 0.25 bitcoins, about $700 at current exchange rates. After seven days, the note says, the victim's decryption key "will be automatically removed from our server" and the files forever lost.
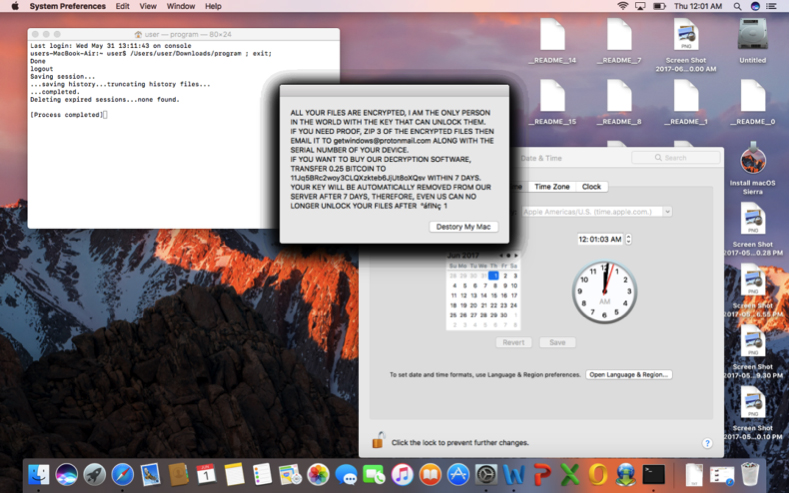
"It is not every day that we see new ransomware specifically targeting Mac OS platform," a Fortinet blog post says. "Even if [this] is far inferior from most current ransomware targeting Windows, it doesn't fail to encrypt [the] victim's files or prevent access to important files, thereby causing real damage."
Likewise, MacSpy won't get past Gatekeeper without a user alert — for the moment. If it does manage to install, it will take a screenshot of the user's screen every 30 seconds, capture photos being synced to the user's iCloud account, record ambient sound even with the microphone switched off, grab browsing and download history from Chrome and Safari, capture clipboard contents (which often contain passwords) and possibly even log every keystroke the user types in.
"People generally assume when they are using Macs they are relatively safe from malware," noted a blog post from AlienVault, the California information-security firm that analyzed MacSpy. "This has been a generally true statement, but this belief is becoming less and less true by the day, as evidenced by the increasing diversity in Mac malware."

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
Paul Wagenseil Reply19873276 said:I heard that it does not work for mac,right?
Sorry, but could you specify what you're asking about? The malware mentioned in the story you're commenting on does work on Macs.
If you're asking about the Petya ransomware worm that hit many companies in Europe yesterday, then no, that does not run on Macs.
 Club Benefits
Club Benefits





