'Dear Valid LinkedIn User': Don't Fall for This Phishing Scam
The URL in a recent LinkedIn scam e-mail seems to go to a valid LinkedIn page, but it quickly bounces you to a phishing page.

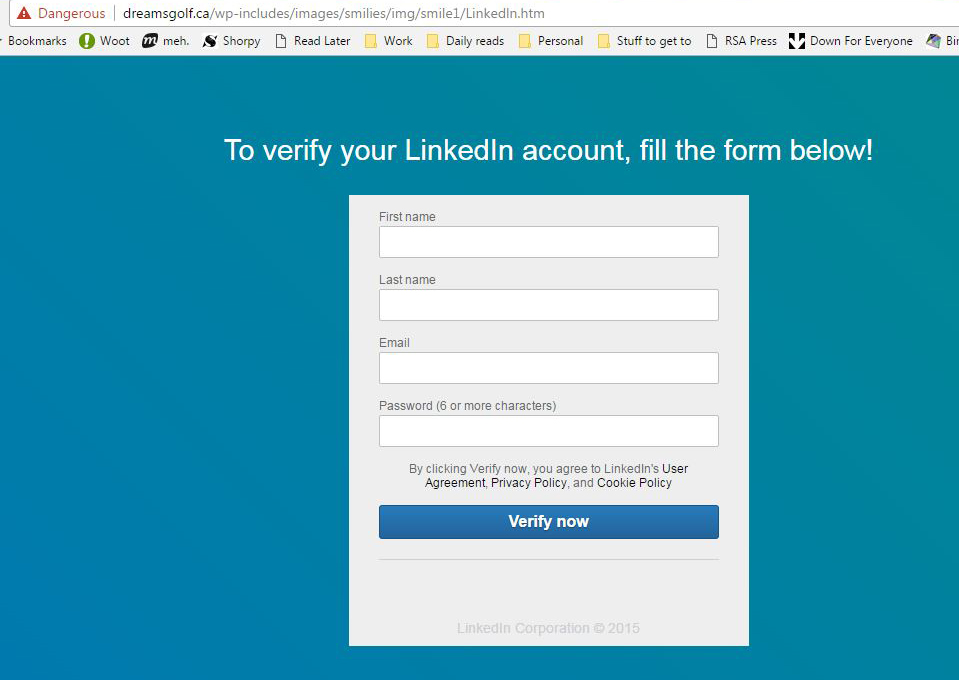
UPDATE noon ET Monday: The phishing page now has been updated to link to another website, which hosts a fairly convincing replica of the actual LinkedIn login page.
Another day, another phishing scam. LinkedIn, which hasn't always had the best security to begin with, may be the delivery method for a curious email message that's been going around.
Like most phishing attempts, it claims to represent a popular social media site and asks for login information. Unlike other scams, though, the link it provides doesn't actually go anywhere (it may have been removed by LinkedIn). It's not clear whether the scam's goal is to steal your login credentials, infect your system with malware or lure you into paying for useless tech support, making the threat pretty mild — for now.
A staffer at Tom's Guide received an email message entitled "Important User Alert" from "linkedIn.customerservices.us1@fsr.net". Even casual users will notice right away that this is not a legitimate LinkedIn email address. Rather, FSR is a Moscow, Idaho-based Internet provider, not really notable for anything other than the fact that it's decidedly not LinkedIn. The "LinkedIn" username is pure fabrication.
MORE: 10 Worst Online Scams and How to Avoid Them
"Dear Valid LinkedIn User," the e-mail begins, and this should be your second tip-off that the message is a scam. The real LinkedIn is aware of your real name and can address messages to you personally. The email continues with errant capitalization on "Important Message" and questionable grammar:
"Our system indicates your account signed-on from different IP recently, do not panic, this happens mostly when your ISP provider changes the IP without your knowledge, but we advise you kindly follow up by Updating to the system to enable auto unflag," and so on, and so forth, in an incredibly grating run-on sentence.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
One need not be very internet-savvy to presume that LinkedIn employs better copywriters than this.
The email warns that users could lose their LinkedIn privileges unless they click on a suspicious link, but that's where two unusual things happen. First off, the URL appears to lead to an actual LinkedIn address, complete with the site's secured HTTPS server. Second, there's nothing there. The site is completely blank and thus, for the moment, apparently harmless. Generally speaking, links like this lead to shady copies of legitimate websites that ask for, then catalog, usernames and passwords.
There are a few possibilities for why there's nothing at the URL. The site could simply be unfinished, but it's possible that the scammers sent out an incorrect link (they would hardly be the first cybercriminals dumb enough to do so).
The fact that the page appears to be hosted on the real LinkedIn website is also interesting, but not necessarily shocking; users can create their own blog posts and pages, so it would not take a very daring criminal to make a malicious LinkedIn page. It's eminently possible that LinkedIn, now owned by Microsoft, already discovered the page and shut it down.
The lesson here is the same as always: Don't click on links in strange emails, and make sure to verify sender addresses in incoming messages to ensure you don't wind up giving away your login information to scammers. The page doesn't work this time, but there are much smarter tricksters out there.
UPDATE: After we posted this story Monday morning New York time, we tried the link in the email message again and found that it now did bounce to a different website that hosted a somewhat convincing replica of the LinkedIn login page. (The colors were wrong and the copyright date read 2015, but the grammar was at least correct.) A screenshot of the phishing page is here, with the URL visible. Google Chrome blocks this page as deceptive.
Marshall Honorof is a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.

