LastPass Can Be Spoofed in Devastating Phishing Attacks
Browser restrictions and scripting vulnerabilities mean that fake LastPass login windows are the perfect vehicles for phishing attacks.
WASHINGTON, D.C. — The password manager LastPass can be impersonated in a phishing attack that could steal all of a user's passwords and credit-card numbers, a researcher demonstrated at the ShmooCon hacker conference here Saturday (Jan. 16).

Sean Cassidy, chief technology officer of the Seattle security firm Praesidio, showed how he "spoofed" a fake LastPass login window in a Web browser to capture a victim's username and master password. Until this past Sunday (Jan. 17), when LastPass fixed part of the issue, if two-factor authentication (2FA) had been enabled, the user would actually have been easier to fool.
"Using two-factor authentication in LastPass makes you less secure," Cassidy said on Saturday.
MORE: Best Mobile Password Managers
Like most password managers, LastPass needs the user to remember only a single master password. This unlocks the LastPass "vault," in which all other account passwords (and sometimes credit-card numbers and other sensitive information), are kept.
When the LastPass software is installed on a computer, it adds extensions to installed Web browsers so that when the user visits a website with a known account, LastPass automatically logs into the site.
For security reasons, LastPass periodically signs the user out of his LastPass account and forces him to log in again with his master password. By default, this happens every two weeks, but the user can change that to happen every time the computer starts up, or when a browser closes, or when a browser has been idle for a certain period of time.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
If the user is logged out of LastPass and visits a website to which LastPass holds the password, the browser displays a banner with a login button stating that "Your LastPass session appears to have expired. Please re-login."
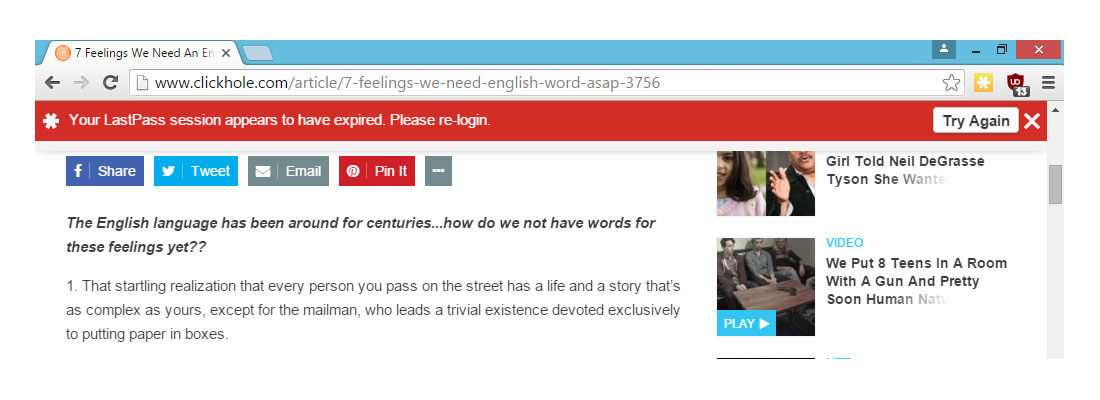
That's all well and good, Cassidy said, but the way LastPass browser logins are handled creates a perfect phishing opportunity. If a malicious or corrupted website were to display a fake logout banner, then a fake login window, the attacker behind the website could seize control of a victim's LastPass account, and then any account — social, financial or Webmail — that had its login credentials in the LastPass vault.
So Cassidy created a proof-of-concept attack, called LostPass, that did just that in Google Chrome.
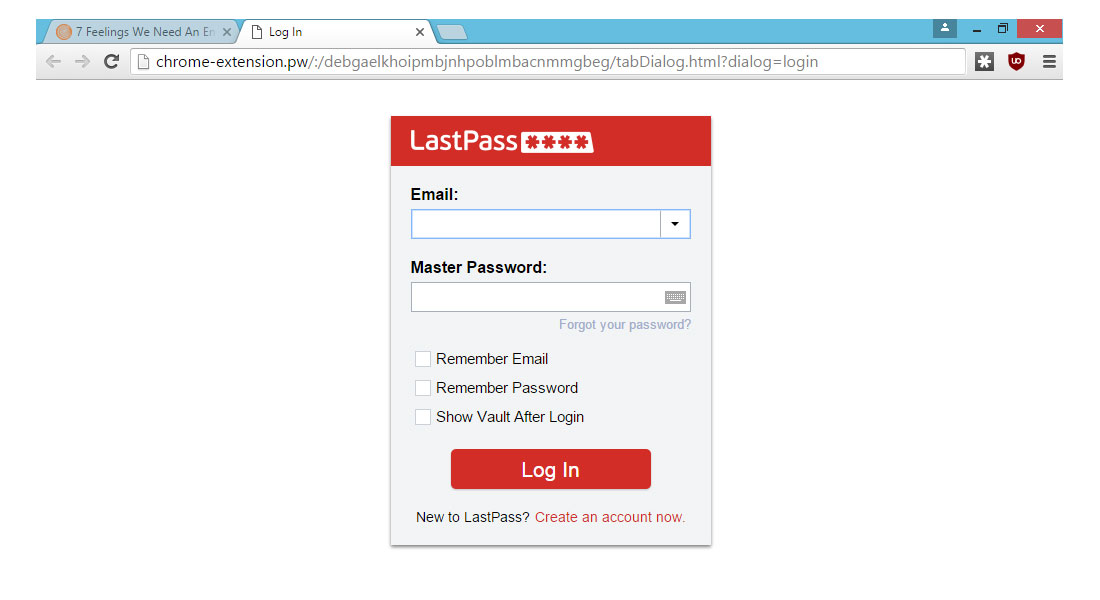
The basic problem, Cassidy said, is that most of the LastPass notifications and login windows appear within the browser's main window, or "viewport," in which websites are displayed. That means any website controlled by an attacker could display pixel-by-pixel reproductions of those LastPass notifications.
In Google Chrome, the logout-notification banner, login window and demand for a 2FA code all appear within the viewport, and Cassidy was able to replicate them perfectly by simply viewing browser source (hit Ctrl + U) and copying and pasting the source code. He even created a close match of the signature "chrome-extension" URL by registering a "chrome-extension.pw" and then using the real Chrome extension's alphabetic ID as the directory name.
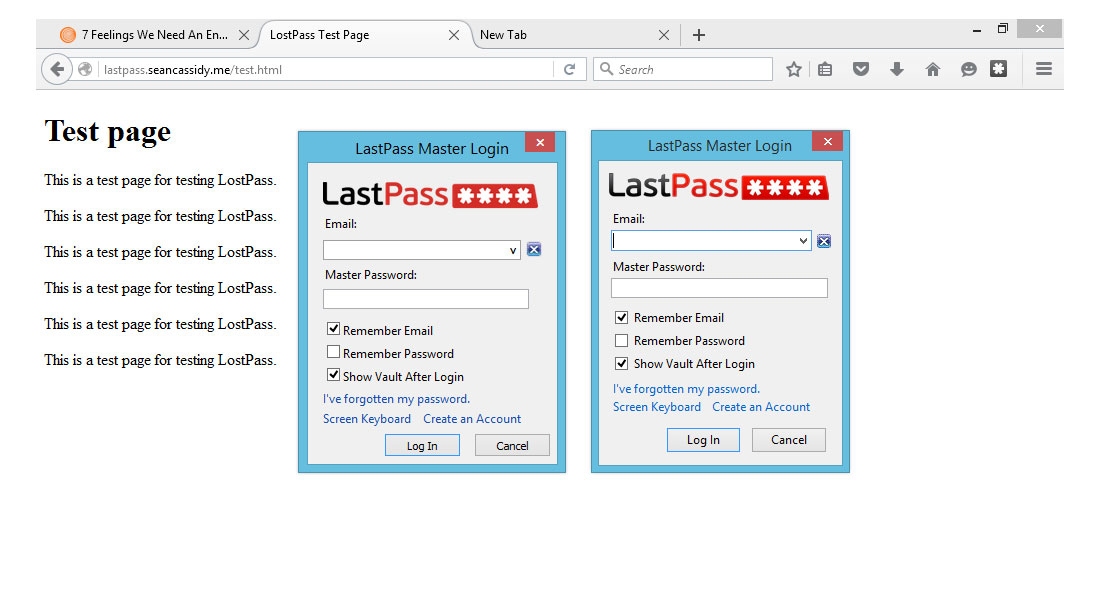
In Mozilla Firefox, the logout-notification banner is in the viewport, but the login window behaves differently on different operating systems. In Windows 8, the login window pops up as a separate box outside the viewport, but Cassidy was nevertheless able to create nearly perfect (but as of yet non-working) facsimiles.
"If it's easy for an attacker to fake, then it's broken," Cassidy said. "If users are tricked, then it's the fault of the software designer. Good UX [user experience] is a security measure."
Until recently, Cassidy said, the LastPass browser extension had a cross-site request forgery (CSRF) weakness, which meant that any website could force the LastPass user to become logged out. (LastPass fixed this after having been notified by Cassidy in November.)
Upon landing on a page with a fake banner warning him that he's logged out, the LastPass user would have immediately checked the LastPass browser icon on the right site of the browser menu bar — and seen that he indeed was logged out.
Another recent LastPass fix involved 2FA. If a user tries to log into LastPass from a new device, LastPass sends the user an email asking him to confirm that he is indeed making that request.
But until Sunday, if that user had previously enabled 2FA, the email would not be sent, and the user would instead be asked to provide a second authentication code provided by the authentication option he had selected. (LastPass supports more than a dozen 2FA options, including Google Authenticator, Microsoft Authenticator, RSA SecurID and YubiKey.)
Cassidy managed to replicate the LastPass notification window in Chrome that asked for a Google Authenticator code. Had the user provided it, even a user with 2FA would have had his account hijacked.

"We have now changed the default so that all users, even those with two-factor authentication, will be directed to the verification process when logging in from unknown devices or locations," LastPass wrote in a lengthy statement Sunday regarding Cassidy's presentation.
Nevertheless, the underlying problem of notifications occurring within the browser viewport still exists in Google Chome, the LastPass statement said. It's just that LastPass has no control over it.
"LastPass has encouraged Google for years to provide a way to avoid using the browser viewport for notifications," the statement said. "As a true solution to this threat, Google should release infobars in Chrome that give extensions the capability to do proper notifications outside the DOM," or main browser window.
As Cassidy pointed out, phishing attacks are the perfect way to steal data. They don't require any malware, and often not much coding, and work very well if they can convince the target that he or she is interacting with a trusted party.
"Phishing is the most dominant attack vector, and is used by everyone from run-of-the-mill Cryptolocker types to APTs," Cassidy wrote in a blog posting put up the day of his ShmooCon presentation. "The real solution is designing software to be phishing resistant. Just like we have anti-exploitation techniques, we need anti-phishing techniques built into more software."
If you'd like to try this proof-of-concept out yourself, Cassidy has released the code for LostPass on GitHub, though he adds in the GitHub README notes that he is "not particularly interested in making it weaponized."
Until Google lets Chrome extensions create new windows, then you might want to consider logging into your LastPass account in Mozilla Firefox, or, even better, within the LastPass application itself.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

