Apple Needs to Add 2FA to Find My iPhone
One student almost had his phone erased by a stranger because Apple doesn't apply two-factor authentication to the Find My iPhone feature.
Apple doesn't apply its two-factor authentication (2FA) security (which requires you to provide additional proof of identity) to all of its iCloud services. This oversight can make it pretty easy for a stranger to erase your iPhone, Mac or iPad. One student learned this the hard way when some no-good miscreant(s) almost leveraged the flaw against him.

Kapil Haresh Vigneswaren, a computer science graduate student at the University of Waterloo in Canada found himself in the middle of such an attack when he discovered someone using Apple's Find My iPhone to ring his device and lock it down by activating Lost Mode.
In a blog post, Kapil detailed the attack, which continued with his iPhone's screen getting dimmed and presenting the message, "Hey why did you lock my iPhone haha. Call me at (123) 456–7890." The attacker likely wanted a phone call in order to ransom some cash out of Kapil, but Kapil never dialed the number.
MORE: Best Android Antivirus Apps - Mobile Security Software
Since Kapil realized that the attacker had leveraged the Find My iPhone function, Kapil immediately took his iPhone and MacBook Pro offline, to prevent the ransomer from formatting the Apple products. After Kapil changed his passwords and took his devices back online, he discovered pending erase requests for both his phone and laptop, which were easy to dismiss.
What's unfortunate about this circumstance is that Kapil took one of the most responsible steps a user can take: He turned on 2FA security for his iCloud account after the infamous uber-hack of Mat Honan. But it turns out that Apple's 2FA implementation doesn't cover the Find My iPhone, Apple Pay or Apple Watch settings, as those options appear on the bottom of the screen after entering an account's username and password.
We spoke with Kapil, and while he cannot pinpoint how the attacker accessed his username and password, he told us that he is not alone. Another user claimed to have had his iCloud account accessed despite "using a completely random password" that wasn't recycled for other accounts.
If Apple doesn't find a way to restrict Find My Phone to device owners, it will continue to put its users data and privacy in jeopardy.
Some could argue that Find My iPhone shouldn't require a second level of authentication, as the missing iPhone can't be used to receive the code that's sent out. That's not a good enough argument, though, as the current implementation gives too much power to anyone who's figured out your Apple ID and password. This is where security questions and answers, which Apple removes when you set up 2FA, could prove useful.
Apple could also have locked out the attacker by keeping track of devices and geolocations. Kapil used the signature at the bottom of the Find My iPhone to sleuth out that the attack had come from Ireland — pretty far from his phone's usual location in Ontario, Canada. Further, emails sent to Kapil show the request was sent from a Windows computer, which could have raised another red flag, as he most often logs in from Macs.
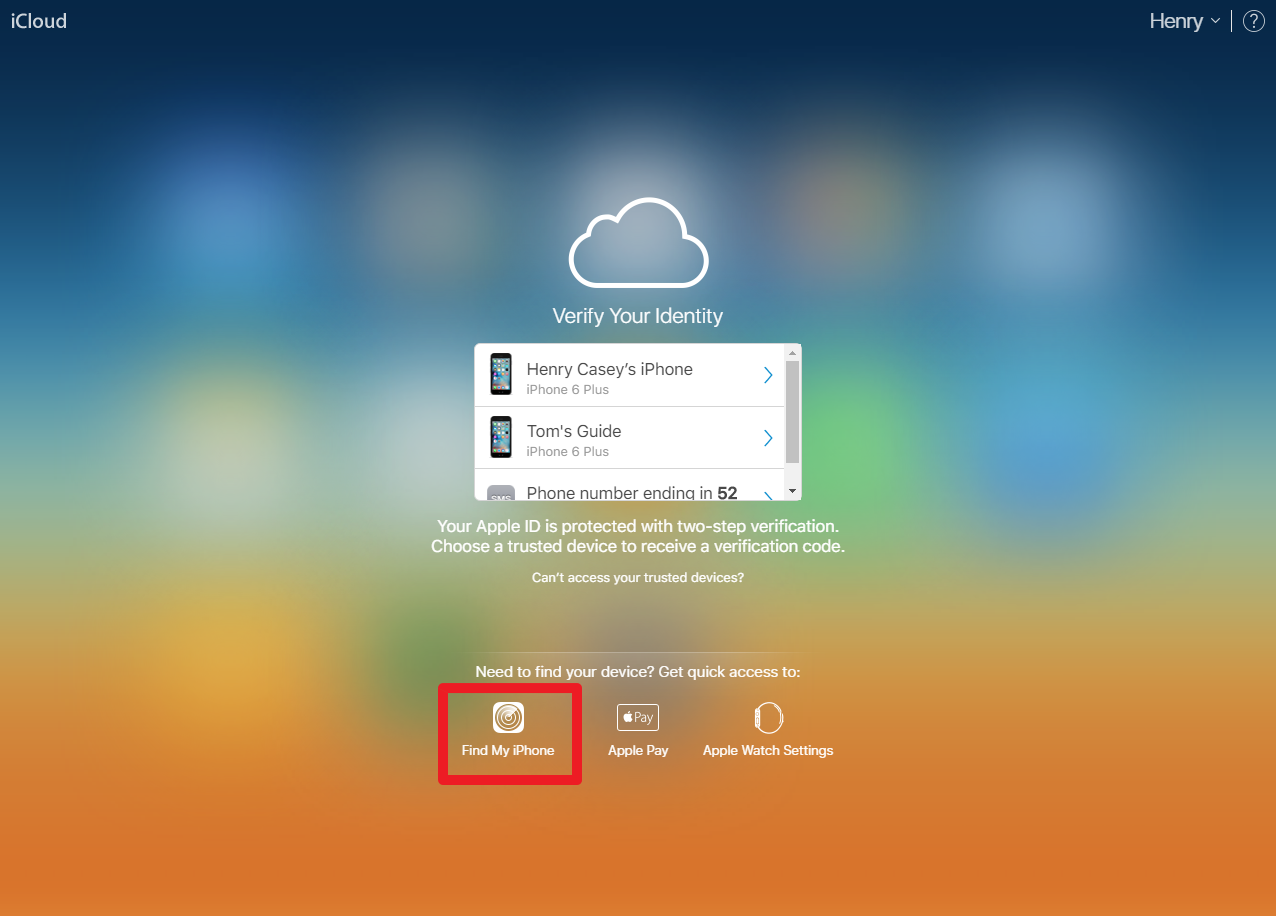
The other unintended problem of not restricting Find My iPhone access with 2FA is that it allows attackers to see where you (assuming you're in possession of the device) are. Sure, this is the intended effect of Find My iPhone, but it gave Kapil's adversary his precise geographic location as well. If Apple doesn't find a way to restrict Find My Phone to device owners, it will continue to put its users' data and privacy in jeopardy.
In the meantime, our best advice is simple: Use complex, hard-to-guess passwords, and watch out for suspicious messages on your iPhone's display.
We reached out to Apple, but the company declined to comment.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.

Henry is a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom's Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He's also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
