Hardware Router Need To Know 2006
Everyone with a high-speed Internet connection needs a router. So why not learn how to choose the one that best meets your needs? We've updated and expanded our classic Hardware Router Need To Know to help you do just that!
Logging
Logging is your router's way of telling you what it's been up to, and more importantly what the folks using it have been doing. Most consumer-class routers have fairly simple logging features and little or no way to "drill down" into the data to look at a particular user's activity. Logs entries tend to be pretty cryptic and in many cases, indeciperable to non-technical users (Figure 8).
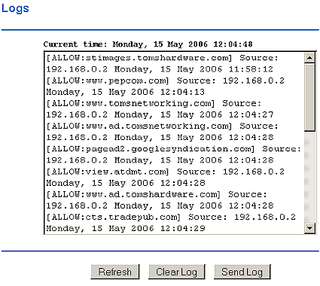
Figure 8: A not-so-helpful log
Other products do a better job of formatting log information and translating it into something that non-geeks at least have a chance of understanding (Figure 9).
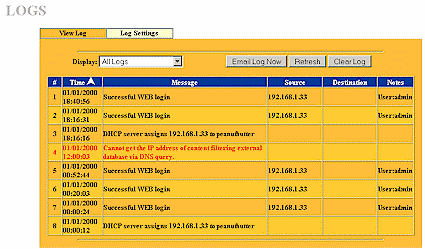
Figure 9: You might be able to understand this log
The three main types of data that are logged are administrative, "hack attempts", and user traffic. Administrative activity includes things like router startup, shutdown, and reboots. You'll also find admin interface logins, too. "Hack attempt" logs usually include any attempt to access your router from a machine on the WAN or Internet side of the router. These attempts are usually not aimed at your router specifically, but result from broad network (or subnet) wide port scans from any number of sources.
Routers can usually interpret and log more potentially damaging attacks such as Denial of Service (DoS), fragmented packet, and other nasty stuff. Finally, user traffic logs keep track of the website, FTP, and other data requests that users make for Internet services.
As mentioned earlier, many routers provide a simple log interface, usually consisting of a page in the admin interface where you can just view a raw list of the logged activities. Some routers allow you to clear and/or save the list to a file, while others just keep a certain number of logged events, discarding the oldest ones as new events are added.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Another kind of simple log is a URL or web traffic log, which may just show the number of visits to a specific web domain, without keeping track of the specific pages visited. If you're interested in keeping track of what a specific user is doing, or need other cuts at the logged data, you should look for products that support external logging.
There are two methods used for external logging. Syslog support lets you specify the IP address of a machine on your LAN that runs a syslog daemon or server. This handy service originated in the unix community and can be added to a Windows or MacOS systems by installing one of the programs that are available. Once installed, it allows your router to send it a copy of its logging information, which can be then be manipulated in various ways.
The other popular external logging method is the SNMP trap, which is the method primarily used by some Linksys routers.
Finally, some routers support Email alerts and reports. These features allow the router to send an email when it detects certain access ("hack") attempts from the router's Internet side, or email a copy of selected log reports on a scheduled basis. Nice features to have if, like most of us, you don't have the discipline to regularly check your logs!
Tom's Guide upgrades your life by helping you decide what products to buy, finding the best deals and showing you how to get the most out of them and solving problems as they arise. Tom's Guide is here to help you accomplish your goals, find great products without the hassle, get the best deals, discover things others don’t want you to know and save time when problems arise. Visit the About Tom's Guide page for more information and to find out how we test products.
