'Gossip Girl' Hackers Behind World's Worst Cyberweapons
U.S. and Israeli hackers have worked together longer and created more cyberweapons than we thought, two researchers said.
The U.S.-Israeli hacking partnership that created some of the world's most powerful cyberweapons is older and more productive than previously known, two researchers said yesterday (April 8) at the Kaspersky Security Analysts Summit in Singapore.

The researchers, Juan-Andres Guerrero-Saade and Silas Cutler from Google sister company Chronicle Security, said that malware called Flowershop, operational in 2002, and spyware called Flame 2.0, discovered in 2016, were both related to Stuxnet, which crippled Iran's nuclear-weapons program in 2010, and Flame, which spied on Middle Eastern computers until its discovery in 2012.
The researchers have given the long-standing collaboration between the two nation-state hacking operations, which may still be operation, a new name: Gossip Girl.
"[State-sponsored] threat actors don't go away after exposure; our aggressors never truly vanish," Guerrero-Saade and Cutler wrote in a blog posting yesterday. "They have an intelligence remit to fulfill and will go to great lengths in doing so."
MORE: Best Antivirus Software and Apps
All the pieces of malware examined seem to have been developed by various groups of U.S. and Israeli state-sponsored hackers, not always working together but often sharing parts and code.
The Chronicle researchers picked the name Gossip Girl for the collaboration -- which they call a "Supra Threat Actor" since it involves several known hacking groups -- after a reference in a Canadian intelligence document leaked by Edward Snowden.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Stuxnet is widely believed to have been jointly developed by hackers working for the U.S. National Security Agency and the Israeli military's Unit 8200, and Flame by the NSA and possibly the Israelis as well.
A related piece of malware, Duqu, was discovered in 2011. It shared code with Stuxnet and is thought to be the work of Unit 8200. A fourth espionage tool, Gauss, found in 2012, shares code with Flame and is thought to have been an NSA project.
Make me a match
Since 2012, security researchers have obtained powerful new tools that let them analyze malware code in bulk to look for similarities. Guerrero-Saade and Cutler used one of these tools, YARA, to scan years of samples obtained by the Google-owned malware repository VirusTotal. They found two new matches for the Stuxnet/Flame/Duqu/Gauss family tree.
One match was Flowershop, discovered (but not publicly disclosed) by Kaspersky Lab in 2013. It's believed to have spied on Middle Eastern targets since 2002. Gurrero-Saade and Culter found that Flowershop shared four different communication modules with Stuxnet, but with no other pieces of malware.
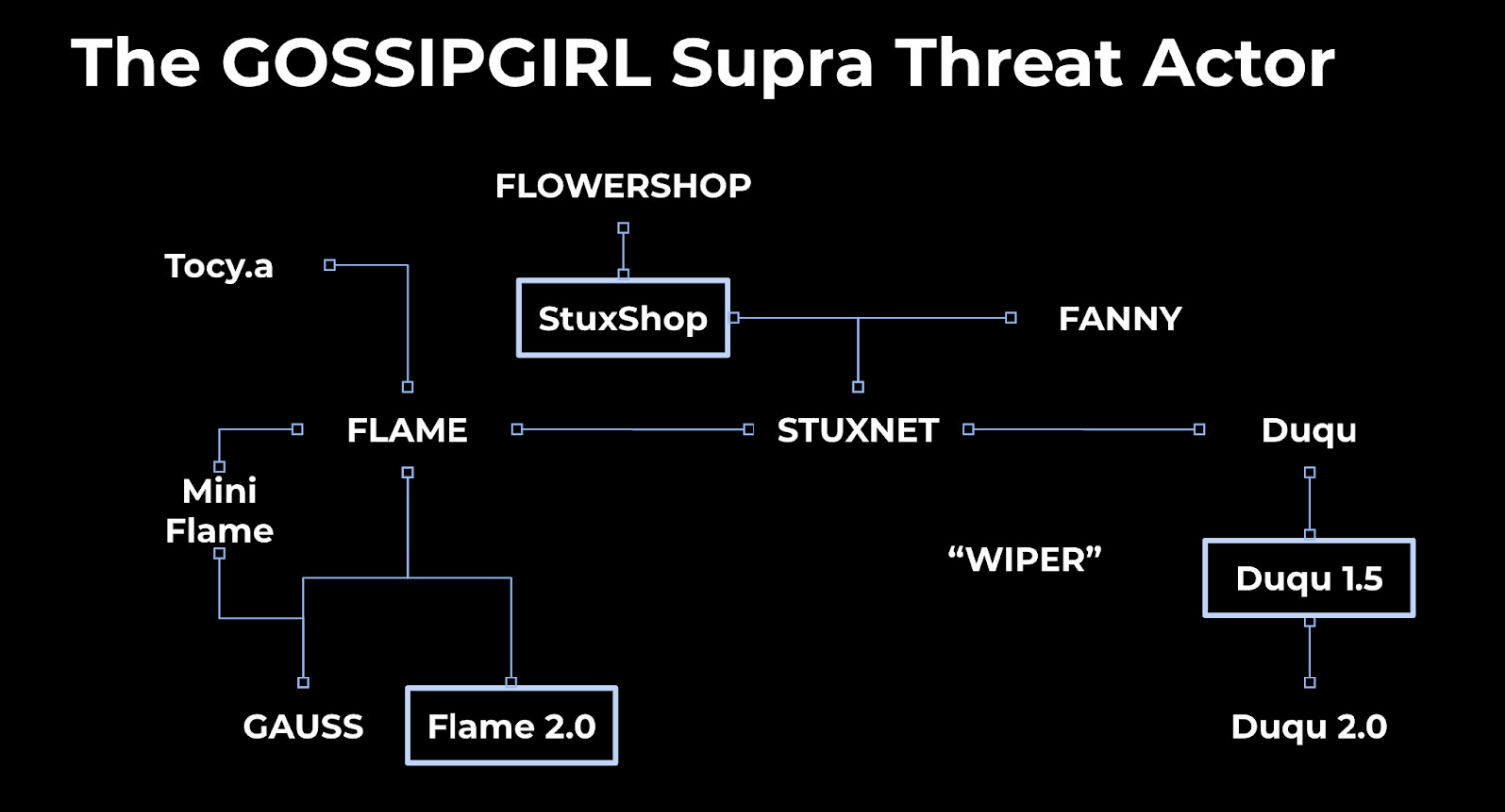
The other match was what Guerrero-Saade and Cutler dubbed Flame 2.0. The original Flame spyware, still one of the most sophisticated pieces of malware in existence, was seemingly killed by its operators using a "suicide" command when the malware was revealed in 2012.
But, as Guerrero-Saade and Cutler wrote, "Flame faked its own death."
They found that a new version of Flame was uploaded to VirusTotal in late 2016, and had originally been created in 2014. Its files were heavily encrypted, so it's not quite clear exactly what Flame 2.0 does or what its targets might be.
More than we can handle
Guerrero-Saade and Cutler didn't offer any opinions about whether Flame 2.0 might still be in operation. But it's a possibility, given that it was only disclosed yesterday.
"We actually fished out more discoveries than we could handle," the pair wrote in their blog posting, inviting other researchers to pick up where they left off by reading three technical papers they posted online. "We hope other researchers, malware analysts, and defenders will benefit from the breakdowns and technical indicators."

Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
