Google Docs Big Phishing Scam: What You Need to Know
A widespread phishing scam involving Google Docs made its way across the internet yesterday. Here's what to do if you fell for the scam.
UPDATED 5:45 a.m. PT Thursday with claim that the incident was an academic experiment gone wrong, and with Google statement.
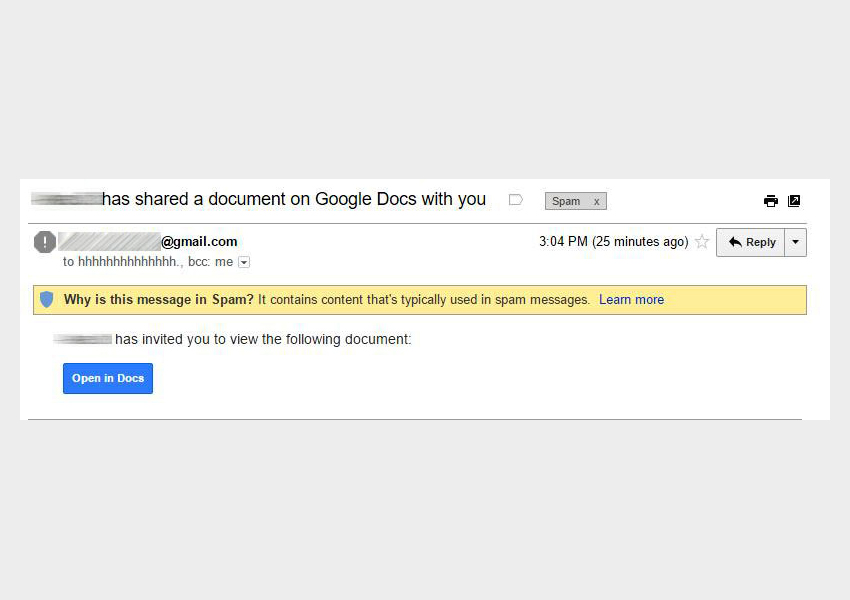
A widespread phishing scam involving Google Docs made its way across the internet yesterday (May 3), with multiple Twitter users and at least two Reddit threads documenting spam messages coming from "hhhhhhhhhhhhhhhh@mailinator.com". Google appeared to have shut down the phishing campaign within about an hour.

The phishing email arrived in your inbox and said that someone you knew had shared a Google Doc with you. There was a button to "Open in Docs" — if you clicked it, you were redirected to a non-Google address, and everyone in your Google address book then got the same phishing email, only with you as the sender. There's no evidence than anything more malicious occurred.
"I just got a Google Doc invite from a BuzzFeed email address, clicked on it, and it spammed everyone I've ever emailed," tweeted Joe Bernstein, a BuzzFeed technology reporter. (This reporter got one of these emails from Bernstein.)
READ NEXT: Why the Google Docs Hack Will Happen Again
It's not yet clear what the aim of the phishing scam was. A posting on the official G Suite blog said that "the problem with Google Drive should be resolved."
If you received such an email and clicked on the"Open in Docs" button, go to https://myaccount.google.com/permissions and see if "Google Docs" is listed as one of the apps that has access to your Google account.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
If so, that's the fake one — the real Google Docs shouldn't appear on this page. Select the fake Google Docs and click the blue "REMOVE" button. (We originally advised changing your Google password, but that doesn't seem to have been necessary.)
"This big phishing attack is clever; an OAUTH based attack. Tricks you into giving 'permission' to read your emails," tweeted Matt Tait, a British security expert.
0Auth is a widely used credentialing standard that keeps you logged into accounts for a long period of time, and can also be used across accounts. For example, when you log into Gmail on one Chrome tab, then open another tab to open Google Drive, a 0Auth "token" logs you into the second tab's content automatically. (Update: It turns out Google uses a proprietary mechanism for that.)
Likewise, if you keep a browser logged into a Twitter account indefinitely, that's OAuth at work. Malicious hackers love stealing 0Auth tokens because they can be reused until the user completely logs out of an account on all devices.
MORE: Best Antivirus - Top Software for PC, Mac and Android
Tait added that the ongoing attack was very similar to a spear-phishing campaign last year carried out by APT28, aka Pawn Storm or Fancy Bear, and documented by the Tokyo-based security firm Trend Micro in a recent report. APT28 is one of the two Russian groups that hacked into the Democratic National Committee's email servers during the 2016 U.S. presidential election campaign.
However, the source code for today's attack was quickly found on at least two code-sharing websites. Its availability indicated that this email virus may have been the work of "script kiddies," or juvenile pranksters, rather than cybercriminals or nation-state-backed hackers.
UPDATE: A Twitter account created Thursday morning by someone calling himself Eugene Pupov, and claiming to be a graduate student at Coventry University in England, said that the Google Docs virus was simply an academic experiment gone wrong.
"The emails I sent were not not a 'phishing scam,' or a scam at all," the purported Pupov said in a series of Tweets. "I was simply testing out a program I had written as my graduate final project for Coventry University. This is a total misunderstanding, and the whole situation has taken a toll on my family's, and my own life. My intention was not to 'phish' or 'scam' individuals. The emails were sent simply as a test."
If that's true, then this situation is eerily similar to the Morris worm, an academic experiment by a Cornell University graduate student that accidentally flooded the pre-web internet in the fall of 1988. However, Tom's Guide could find no other evidence of a Coventry University student by the name Eugene Pupov, or by common variants of that name. Coventry University told Vice Motherboard it had no such student.
Security researchers discovered yesterday that the code behind the Google Docs virus had been signed by a Eugene Pupov, but that was disclosed before the Twitter account was created.
Google itself commented on the incident with this statement: "We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts. We've removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again. We encourage users to report phishing emails in Gmail. If you think you clicked on a fraudulent email, visit g.co/SecurityCheckup and remove apps you don't recognize."
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
RKO153 I do have an app added to Permissions called Google Chrome which was added about the time I received this email from a friend. Today I can't send email because my Gmail says I reached my sending limit. Any advice on the above two issues?Reply

