New Gmail Phishing Attacks Can Easily Be Stopped
If you've got two-factor authentication enabled, you'll be safe from new attacks tricking Gmail users into turning over their passwords.
UPDATED March 15, 2017 with information that Google has updated the Chrome browser to make attacks like this one easier to spot.
A new style of phishing attack targeting Gmail users reaffirms the best easy-to-follow advice we offer to everyone: Turn on two-factor authentication. The latest attack aims to trick users into entering their login credentials with a site that looks just like Google's sign-in page.

This news comes to us from the WordPress security site Wordfence, which reported the attack last week and noted that it began in 2016. The firm notes that the phishing technique has hit "experienced technical users" in the recent weeks, suggesting that even savvy users can fall prey if they're not looking closely enough.
MORE: Mobile Security Guide: Everything You Need to Know
Users get routed to this hijack page by clicking an image in an email that is styled to look like Gmail's attachment interface. Almost everything on the hijack page is picture-perfect, except its URL, which starts with "data:text/html," which should be a red flag to eagle-eyed users.
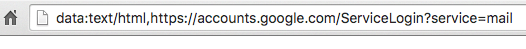
According to a discussion thread on the tech forum Y Combinator, after users enter their Google passwords on the fake login page (which uses all of the same animations as the real thing), their Gmail accounts immediately become compromised. It's unclear whether the attackers are using an automated service to perform account takeovers so speedily, but once they're in your email account, they weaponize the account to attack other users.
What You Can Do
Users can protect themselves, as we've said, by using Google's two-factor authentication (2FA) which would demand that anyone logging into the account from an unrecognized account provide a second item of verification, such as a code sent by Google to the legitimate user's mobile phone or a physical USB security key that the legitimate user carries.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
To activate 2FA, first sign into Google, then visit the My Account page, click "Signing in to Google" and click "2-step verification."
News of this latest phishing scam is an opportunity to remind reader to never recycle passwords. While your Google account may be protected by 2FA, the attackers could try to sign into other sites with the same username and password combination, just to see what works. Make sure nothing works by using a password manager to create unique and hard-to-guess passwords.
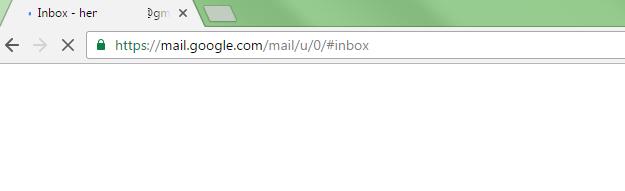
Lastly, always check the URLs of the pages you're viewing to look for clues such as the "data:text/html," string. In Chrome, you shouldn't enter your username and password into any page that doesn't feature a green lock icon at the start of the address field.
UPDATE: Wordfence has updated its blog post to note that an update to Google Chrome makes clear that the URL being accessed in this scam may be malicious by displaying "NOT SECURE" in the address bar.

Henry is a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom's Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He's also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
