Huge Ransomware Attack Stopped by Accident: What to Do
UK hospitals, a Spanish telecom and organizations from the US to Taiwan were hit by ransomware that used an attack developed by the NSA.

Update 5/14 5:17 pm PT: Microsoft has criticized the NSA for what it says is the agency's role in weaponizing a weakness in Windows and allowing it to be stolen by hackers, which was reportedly used to launch the largest ransomware attack in history.
As reported by the Los Angeles Times, "This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem," wrote Brad Smith, president and chief legal officer at Microsoft.
A massive ransomware attack spread across the globe May 12, with reports of computer systems being locked up in Russia, Western Europe, East Asia and North America. British hospitals and a Spanish telecom were the most visible victims, but the largest number of attacks seemed to be in Russia.
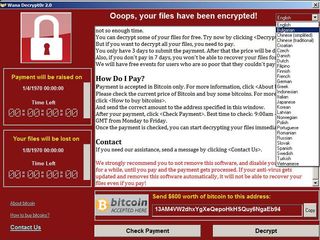
What you need to do: If you've not installed the March, April or May Windows Update bundles, do so immediately. It's worth shutting down your system for a few minutes if it gives you a chance to avoid this. If you're still using Windows XP, you're out of luck, but the March and April update bundles should be available to Windows Vista. (UPDATE: Microsoft has released a patch for Windows XP and its server counterpart Windows 2003.)
The ransomware, variably called WanaCryptor 2.0, WannaCry, WCry or WCrypt, seemed to be using an exploit that was developed years ago by the U.S. National Security Agency (NSA) and revealed publicly in a data dump last month. Microsoft secretly patched Windows against the attack in March, but many systems in large organizations had apparently not been updated.
MORE: What Is Ransomware and How Can I Protect Myself?
Global impact
Several hospital systems in England reported that their computer screens displayed a message demanding $300 in Bitcoin. The Spanish telecommunications giant Telefonica had its systems brought down by ransomware that showed a ransom screen nearly identical to those hitting English hospitals, according to a report by the newspaper El Mundo.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
A live interactive map posted on the British tech blog MalwareTech showed infections in the United States, Canada, Mexico, and most countries in South America and East Asia. But Europe, including Russia, appeared to have the densest concentration.
ZDNet reported that at least 16 National Health Service (NHS) hospital systems in England had been hit by the ransomware, and that the infections had appeared in Scotland as well. The BBC raised that number to 25 hospital systems, and said that Prime Minister Theresa May was being kept informed of the situation. English and Scottish hospitals were reportedly postponing appointments and directing patients to unaffected facilities.
Russian antivirus firm Kaspersky Lab said it had detected more than 45,000 infections in 74 countries, the vast majority of them in Russia. The Czech antivirus firm Avast detected 57,000, with the worst-affected countries being Russia, Ukraine and Taiwan. England's NHS and Spain's computer emergency response team each issued public warnings.
A Twitter feed purportedly belonging to a hacktivist group calling itself SpamTech claimed responsibility for the attack, stating that "The 'WannaCry/WCRY' was created by one of our members. We've taken over NHS computers and major engineering operation components." The group didn't offer any proof to verify its claim.
Spreads on its own
The ransomware appears to be "wormable." In other words, it's spreading from system to system by itself as a computer worm, rather than relying on human interaction as a Trojan horse, or infecting desktop applications like a traditional computer virus.
"Something like this is incredibly significant," tweeted the blogger behind MalwareTech. "We've not seen P2P" — malware jumping from one "peer" computer to another — "spreading on PC via exploits at this scale in nearly a decade."
Other experts compared today's infection to the Conficker worm, which continues to attack computer systems around the world despite the fact that the security flaw it exploits was patched in 2008.
However, Conficker does no immediate damage and hides so that it can use infected computers as part of a "botnet" to send out spam and fake antivirus software. The worm spreading today immediately alerts the user to its presence, displaying two countdown clocks: the first tied to a deadline when the ransom amount will increase, the second to when all encrypted files will be deleted.
MORE: Best Identity-Protection Services
The $300 ransom demand — in some instances, $600 — indicates that hospitals and other large organizations do not appear to have been selected as targets, but rather infected randomly. In previous ransomware attacks against large institutions, cybercriminals running the malware have raised ransom demands into tens of thousands of dollars once they've realized the value of the infected systems.
Image, movie, email, database and Microsoft Office files were among those targeted for encryption, as were files containing encryption keys.
Some of the victims seemed to be paying up, with two of the Bitcoin wallets — here and here — specified as recipients by the ransomware screens reporting 16 payments today totaling about $4,675.
"One thing is for sure," said Rich Barger, director of cyber research at database-software maker Splunk, in a statement. "Somebody is going to get very rich, or spend a very long amount of time in jail."
Ties to the NSA
At least two reports said the WanaCryptor ransomware was using an NSA exploit called ETERNALBLUE that was revealed in a cache of files posted online by WikiLeaks a group calling itself ShadowBrokers on April 14. Encrypted files are given the file suffix ".wncry".
ETERNALBLUE exploits a previously unknown flaw in Microsoft's Server Message Block (SMB) protocol. (SMB lets machines on the same network share access to printers, files, network ports and other objects) The ShadowBrokers last summer tried and failed to auction off a large amount of information the group said had been stolen from the NSA.
The public disclosure of ETERNALBLUE's code by the ShadowBrokers caused a moderate amount of panic in the information-security world, until Microsoft revealed the day after the dump that it had quietly patched the SMB flaw — and several others mentioned in the dump — a month earlier, with the March "Patch Tuesday" security updates.
UPDATE: The ransomware attack was stopped dead in its tracks Friday by a British information-security professional, who tripped an unintentional "kill switch" in WanaCryptor, more or less by accident.
The pseudonymous IT pro, who blogs under the name MalwareTech, analyzed WanaCryptor's code and noticed that it reached out to a server at a specific web address. He saw that there was no actual server at that URL, so he bought the address name — in technical terms, he registered the domain — and set up his own "sinkhole' server to see how many infected computers would connect to it.
Much to MalwareTech's surprise, the ransomware samples he and other researchers were analyzing suddenly stopped encrypting infected machines.
"I will confess that I was unaware registering the domain would stop the malware until after I registered it, so initially it was accidental," MalwareTech tweeted late on Friday. "So I can only add 'accidentally stopped an international cyber attack' to my résumé."
In a detailed blog posting, MalwareTech explains that the "kill switch" may have been designed to hide the ransomware from antivirus researchers, who often run malware in restricted environments that simulate internet connections. The criminals behind the malware may not have thought that anyone would register that domain.
Microsoft also took the trouble to release patches against the ransomware for Windows XP and Windows Server 2003, both of which stopped receiving regular security patches in 2014. It's likely that many of the British hospitals hit were still running Windows XP, upon which many legacy medical devices depend.
If you haven't updated your systems to prevent infection by WanaCryptor, do so immediately, because MalwareTech's kill switch is not a permanent solution.
"One thing that is very important to note is our sinkholing only stops this sample," he noted in his blog posting. "There is nothing stopping them removing the domain check and trying again, so it’s incredibly important that any unpatched systems are patched as quickly as possible."
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.












-
Avast-Team Our threat labs posted an interesting article on this attack today. WanaCrypt0r has been around since February, but we've seen over 75,000 detections worldwide just today.Reply
https://blog.avast.com/ransomware-that-infected-telefonica-and-nhs-hospitals-is-spreading-aggressively-with-over-50000-attacks-so-far-today -
Paul Wagenseil Reply19682760 said:Our threat labs posted an interesting article on this attack today. WanaCrypt0r has been around since February, but we've seen over 75,000 detections worldwide just today.
https://blog.avast.com/ransomware-that-infected-telefonica-and-nhs-hospitals-is-spreading-aggressively-with-over-50000-attacks-so-far-today
Yes, I've already linked to your blog posting in the story above. -
Avast-Team Reply19682803 said:19682760 said:Our threat labs posted an interesting article on this attack today. WanaCrypt0r has been around since February, but we've seen over 75,000 detections worldwide just today.
https://blog.avast.com/ransomware-that-infected-telefonica-and-nhs-hospitals-is-spreading-aggressively-with-over-50000-attacks-so-far-today
Yes, I've already linked to your blog posting in the story above.
Thanks Paul, I see it now! Apologies for the double post if it was already included.
-
mjslakeridge This is the lead story on Foxnews.com right now. Their article says that the malware was stolen from the N.S.A. last year.Reply -
Intishar Why should governments, hospitals, public offices and telecoms go around buying expensive Windows products which causes them much havoc form time to time, sometimes from rather minuscule malware codes?Reply -
topher_1 You can just hold ctrl alt del and pull up task manager then close your browser. Problem solved.Reply -
kittyhundal Correction: It wasn't a Wikileaks dump that released this. It was the ShadowBrokers code dump.Reply




