New Ransomware Looks, Acts Like Windows Update
The new Fantom ransomware looks and acts just like Windows Update -- until you receive the note asking for payment to decrypt your files.
Microsoft no longer lets you decide whether to install Windows system updates, and online criminals have noticed. The new Fantom ransomware takes advantage of this situation by nearly perfectly mimicking the Windows Update process, and will keep almost any user fooled until it's too late.

AVG security researcher Jakob Kroustek discovered Fantom last week. He notified the Bleeping Computer blog, and the details are pretty scary.
The ransomware itself is called "CriticalUpdate01.exe," the file it extracts is called "WindowsUpdate.exe," and the screen that displays as it begins to encrypt your files looks very much like the modern blue screen that Windows 8, 8.1 and 10 users are familiar with.
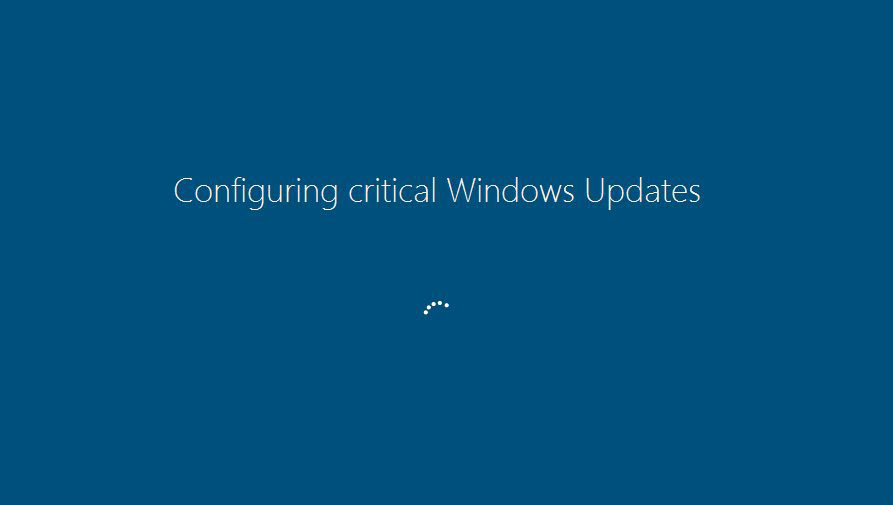
"Unfortunately, there is no way to currently decrypt the Fantom Ransomware," Bleeping Computer noted, adding that the ransomware was built using the open-source ransomware kit called EDA2.
MORE: What Is Ransomware and How Can I Protect Myself?
While you're waiting for Windows Update to finish and the machine to restart, Fantom is happily at work encrypting all the files it can find bearing any of about 600 different suffixes, including those commonly used for music, video, photo and office files. Encrypted files get the additional suffix ".fantom."
When the encryption process is finished, Fantom pops up a ransom note instructing the user to email a Russian email address. No specific ransom amount is mentioned, but presumably the response from the online criminals will include one. Victims have a week to pay up or the files will be erased, the note says in pretty poor English.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
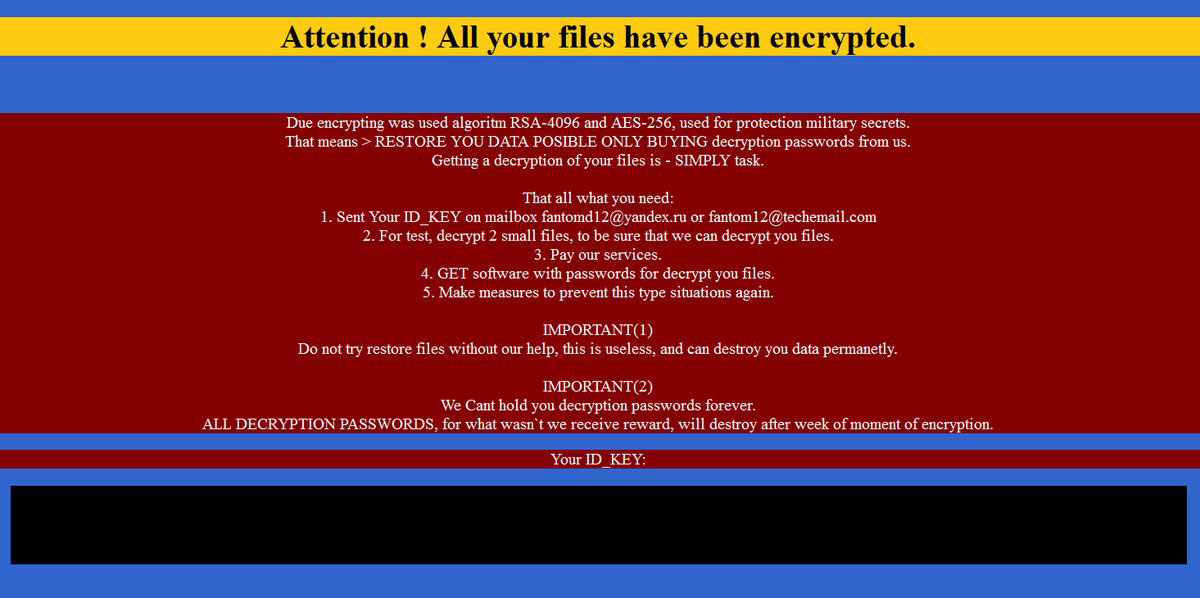
If you're seeing that screen, you're pretty well hosed. Your only options will be to either negotiate a ransom payment (many of these crooks won't be offended if you try to haggle) or hope that any recent system backup you may have wasn't encrypted too.
To prevent infection by any kind of ransomware, don't click on any links in email messages you don't expect; configure your Windows user accounts so that your day-to-day-usage account is a "limited" one that can't install software; and install and run robust, continually updating antivirus software.
Windows 7 and 8.1 users can go into Control Panel and set Windows Update to install patches only when they want it to. That won't prevent infection, but if a random Windows Update screen pops up, you'll know it's bogus and can shut down the machine immediately. (After that, boot antivirus software from a rescue disk — here area few you can burn to a CD or put on an USB flash drive — to clean your system without starting Windows.)
Windows 10 Home users can't stop automatic system updates. Microsoft, in its infinite wisdom, has taken away that choice from you. Even Windows 10 Pro users can only postpone, not opt out of, system updates. So if that Windows Update window takes over your screen, you won't be able to tell if it's the real thing, or ransomware.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
elcaab This only happens if you get your updates outside of the official support channels! Note that for most people, using the automatic update provides much more protection than risk of infection.Reply -
carl0ski Not true elcaabReply
What happens is the initial prompt mimicking the get updates prompt windows 10 shows every couple of days that has became normal windows 10 user experience.
If the user can then be tricked into running the next step then that is bad -
RahSa_EnGre I agree with carl0ski. I got infected a few days ago just because I trusted a freelancing company that connects me with clients via their platform. In this case, the attackers used their application, the hacker actually presented himself and talked to me for 20 minutes through a fake profile just to send me a virus. He even encouraged me to click on it, assuring me that the file is safe. Luckily, I used my old computer, and i have a backup of all files that were there. I am still in negotiations over how will this be resolved, which is why I won't name the company responsible at this moment.Reply
This is a question of irresponsibility and companies that simply do not care for our safety even after we pay for their services should be prosecuted and held liable. And it's not only the private companies, governmental institutions, education systems and even healthcare services are continuously endangering their citizens, users, students and patients.
https://www.securelink.com/securelink-blog/2016-the-year-of-ransomware/
We need a wake up call people. THe number of ransomware attacks quadrupled over the past few months and we are still believing that this can't happen to us. I am a living proof that it can.
http://www.theinquirer.net/inquirer/news/2462564/ransomware-attacks-increase-fivefold-in-just-one-year -
Christopher1 Or, better yet: ONLY use Windows Update and updates from Microsoft's OWN website. Period!Reply
Also, do not download every Dick and Jane program on the internet and install them to your computer!
I swear.... I have not gotten hit with a true virus (I have gotten hit with 'scareware' game trainers being labeled trojan horses) ever since I enabled No/NotScript on Waterfox/Chrome and started being very very very leery about enabling scripts on websites.

