Chromecast Flaws Could Lead to Smart-Home Invasion
Kaspersky Lab tested four smart-home devices, including Chromecast, for security flaws, and the results were not encouraging.
The Internet of Things is, by and large, not very secure. While there haven't been too many recorded attacks on smart-home gadgetry yet, the known vulnerabilities keep stacking up, while the companies that produce the tech are often hesitant, or even unable, to offer patches. To demonstrate just how simple it might be to hack the average smart home, Kaspersky Lab tested four devices at random, including the common Chromecast streaming stick, and the results were not encouraging.
Kaspersky Lab, a Moscow-based security firm, researched the story and wrote up its findings on the Securelist blog. The company claimed that it "gathered up a random selection" of smart-home devices, then chose four to illustrate how a savvy attacker might take advantage of a whole chain of devices to compromise a whole home.
MORE: Best Smart Home Gadgets
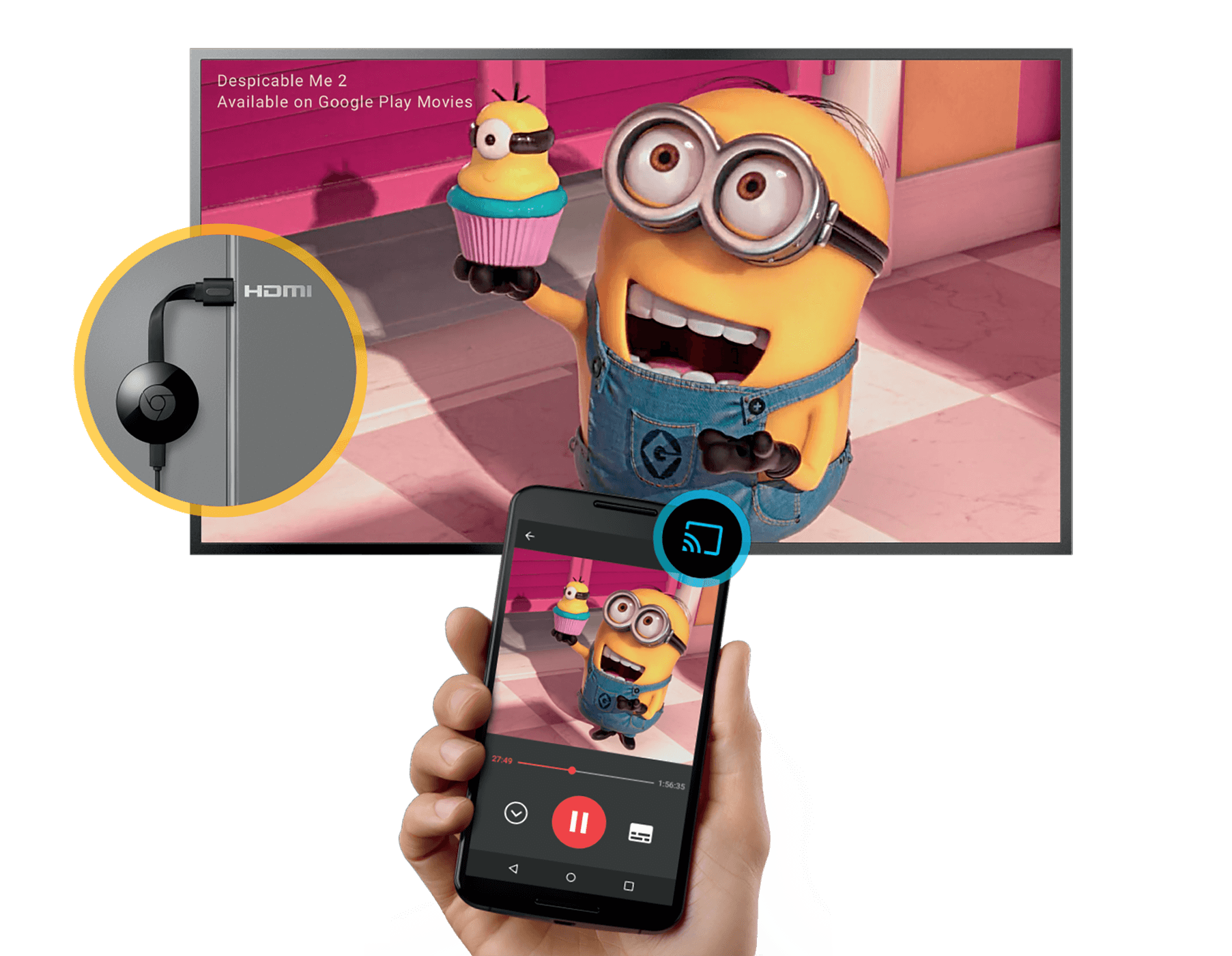
The process begins with the Google Chromecast streaming stick (the 2013 model; the 2015 Chromecast model may also be affected). Hijacking the Chromecast's output is quite simple, due to two features that combine to form a bug.
Firstly, a Wi-Fi command called "deauth" lets a hotspot end its connection to any client device. Common hacking software tools use deauth to kick targeted devices off Wi-Fi networks. Secondly, if you've ever set up a Chromecast, or used it in a hotel room, you'll know that it can broadcast its own Wi-Fi network.
Now, if you kick a Chromecast off a Wi-Fi network, it will start its own network and look around for devices to connect to. That's when you connect your own device and start streaming content to the Chromecast, much to the surprise of its legitimate user. This was amply demonstrated by a security researcher last year when he used a mini-computer to rickroll his annoyed friends on their own TVs.
That researcher needed to be in the same home as the Chromecast, or just outside the window, for the rickroll to work. But the Kaspersky team found that with a cheap directional Wi-Fi antenna, they could do it from farther away so that the targeted user wouldn't spot them.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
It's harmless enough to send a cheesy '80s music video, but a clever attacker could "phish" the Chromecast's user by sending a notification to the TV screen that the user has to re-enter, or even change, his or her Wi-Fi network password. The trap is set.
Now an attacker has your Wi-Fi password. What can he or she do with it? The next device Kaspersky Lab tested was an Internet-connected security camera marketed as a baby monitor. Baby-monitor cameras are well-known targets for attacks, since they are often poorly secured. Kaspersky researchers used a Philips model and found that all they needed to access it was a freely downloadable app and the appropriate Wi-Fi credentials.
Seeing into a user's home is bad enough, but from there, a little creative tinkering allowed them to access user e-mail addresses associated with the baby monitor. Now, an attacker would have a Wi-Fi password, an e-mail address and the ability to see inside a victim's home.
Supposing the Chromecast phishing trick didn't work, there's still another way to hijack your Wi-Fi login: your coffee maker. Kaspersky Lab experimented with a "smart" coffee maker (brand withheld) and found that it also presented a rather simple way to steal a Wi-Fi password.
When the machine initially connects to a user's phone, the coffee maker, like the Chromecast, creates a temporary hot-spot. Anyone in possession of the coffee-maker app (and close enough to connect) can then try to hijack the password. The password is encrypted, but shockingly, the encryption key is not. Deciphering the password, then is simply a matter of basic app programming and cryptology.
If you have a Wi-Fi password and an email address, you can then theoretically hack into a smart-home security hub -- although, to do so, you'd have to reverse-engineer its software, and that's beyond the ability of most workaday hackers. What almost anyone can do, though, is fool a smart-home security hub's sensors.
The Kaspersky Lab team found that one model's door and window sensors were easily fooled by powerful magnets (a common problem) and that its infrared motion sensors were fooled by cold objects (another common problem). As long as you knew where the motion sensors and door and windows sensors were located in a home (which you might, if you've hacked the baby monitor), you could put on cold clothing or use magnets and walk right past.
Kaspersky Lab notified the vendors about these possible means of intrusion, and as of now, all of the baby-monitor issues have been patched. The Chromecast, coffee-maker and security-hub issues are still in existence.
To be fair, the vulnerabilities are complex, and the likelihood of an attacker taking advantage of these flaws seems just about as probable as an attacker casing and breaking into a non-smart home. But if you purchase these devices, be aware that they may open up security holes in your home that everyday dumb devices don't allow.
Marshall Honorof is a senior editor for Tom's Guide, overseeing the site's coverage of gaming hardware and software. He comes from a science writing background, having studied paleomammalogy, biological anthropology, and the history of science and technology. After hours, you can find him practicing taekwondo or doing deep dives on classic sci-fi.

