Dropbox Says You Should Reset Your Password: Here's How
If you haven't changed your Dropbox password since mid-2012, there's no time like the present. Here's how to improve your account's security.
UPDATED Wednesday, Aug. 31 with the number of Dropbox accounts affected by the 2012 breach.
UPDATED Thursday, Sept. 1 with news that the stolen accounts were being sold online.
There's no need to panic — really — but if you signed up for Dropbox in 2012 or earlier and haven't ever bothered to change your password, the cloud-storage services thinks that you probably should do so.

The reason? Dropbox says in a blog post that its security team learned about an old set of Dropbox user credentials that included email addresses and hashed and salted pass that apparently fell into the wrong hands at some point in 2012. Dropbox doesn't think any accounts have been compromised, but as a precaution it wants users who haven't changed their passwords since the middle of 2012 — an entire presidential election ago! — to get on the ball.
MORE: How to Create and Remember Super-Secure Passwords
In fact, Dropbox is so insistent about you changing your 2012-era password that you'll be required to do so the next time you log into the file-sharing service.
But if you'd prefer not to wait or if you're just one of those cautious types, here's how to change your password right now, using Dropbox's web interface.
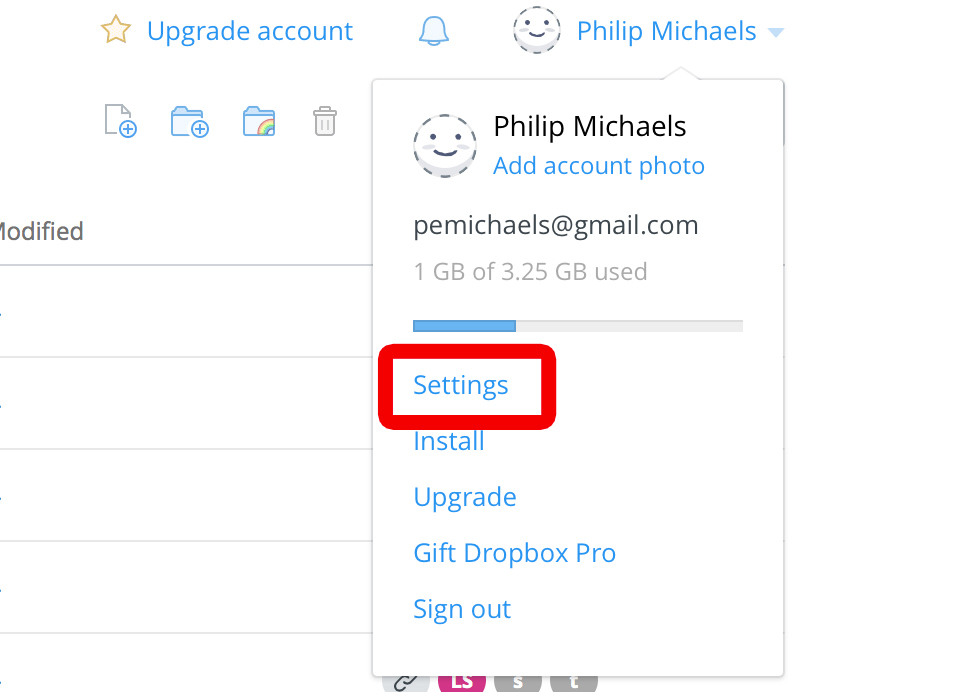
1. Go to Dropbox.com and click on your name in the upper left corner. Select Settings from the drop-down menu.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
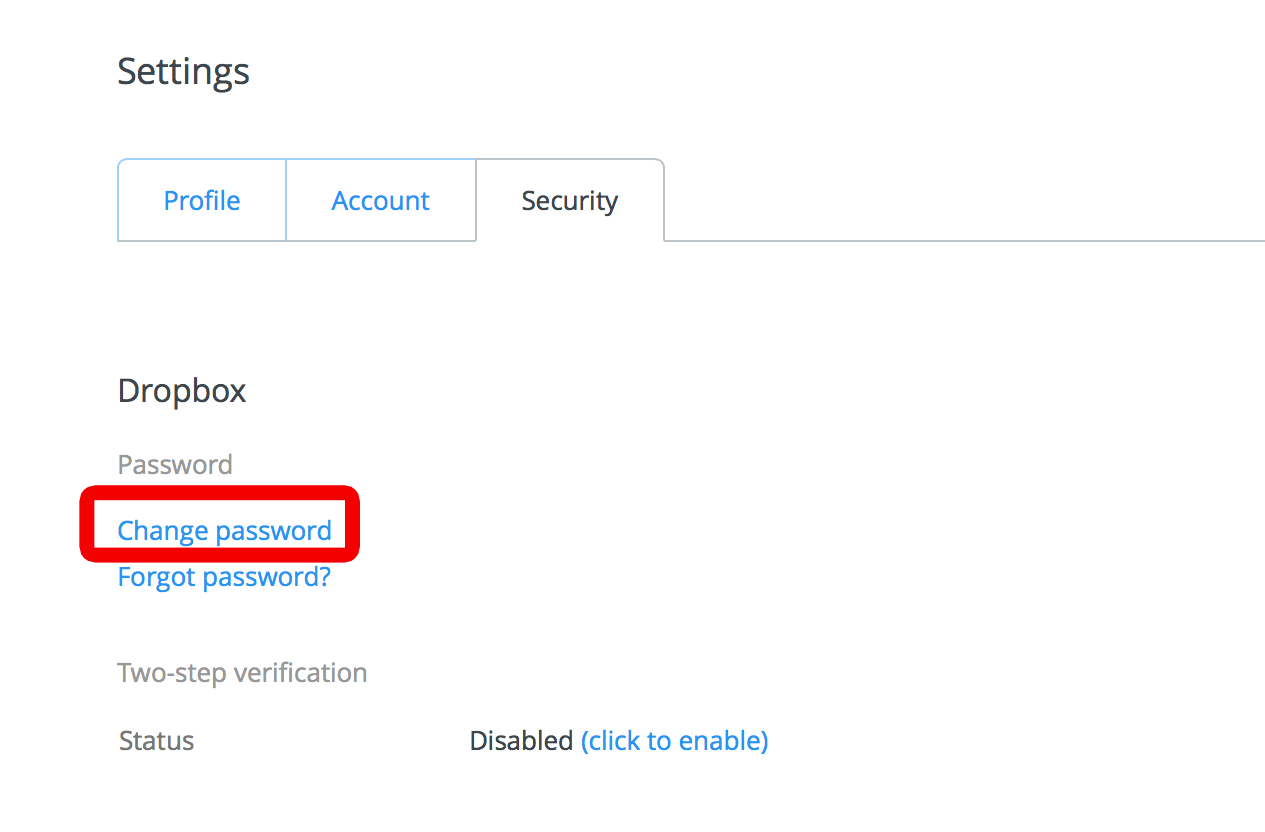
2. Select the Security tab and click on Change Password.
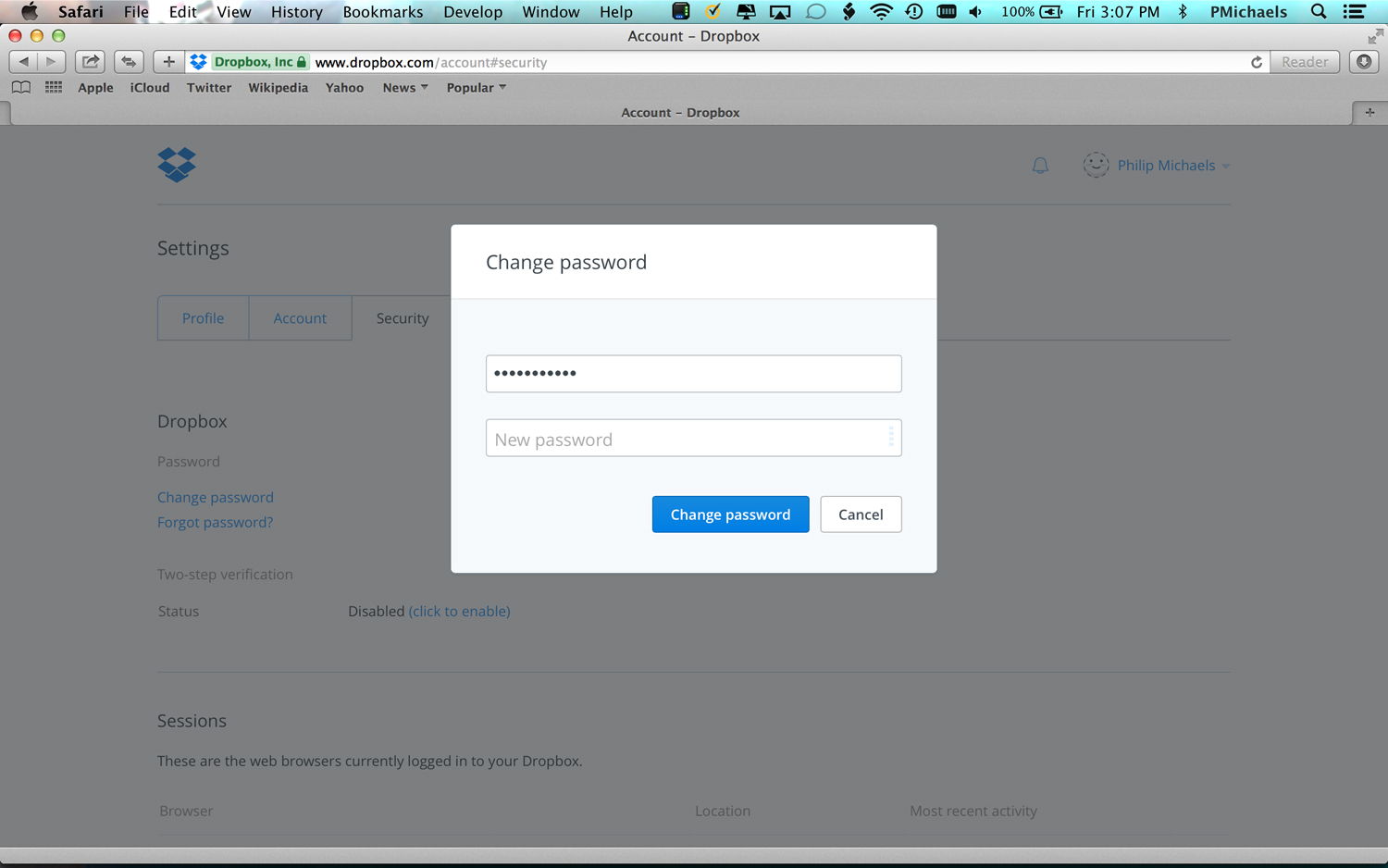
3. Enter your old password, and then your new one. Click on Change Password.
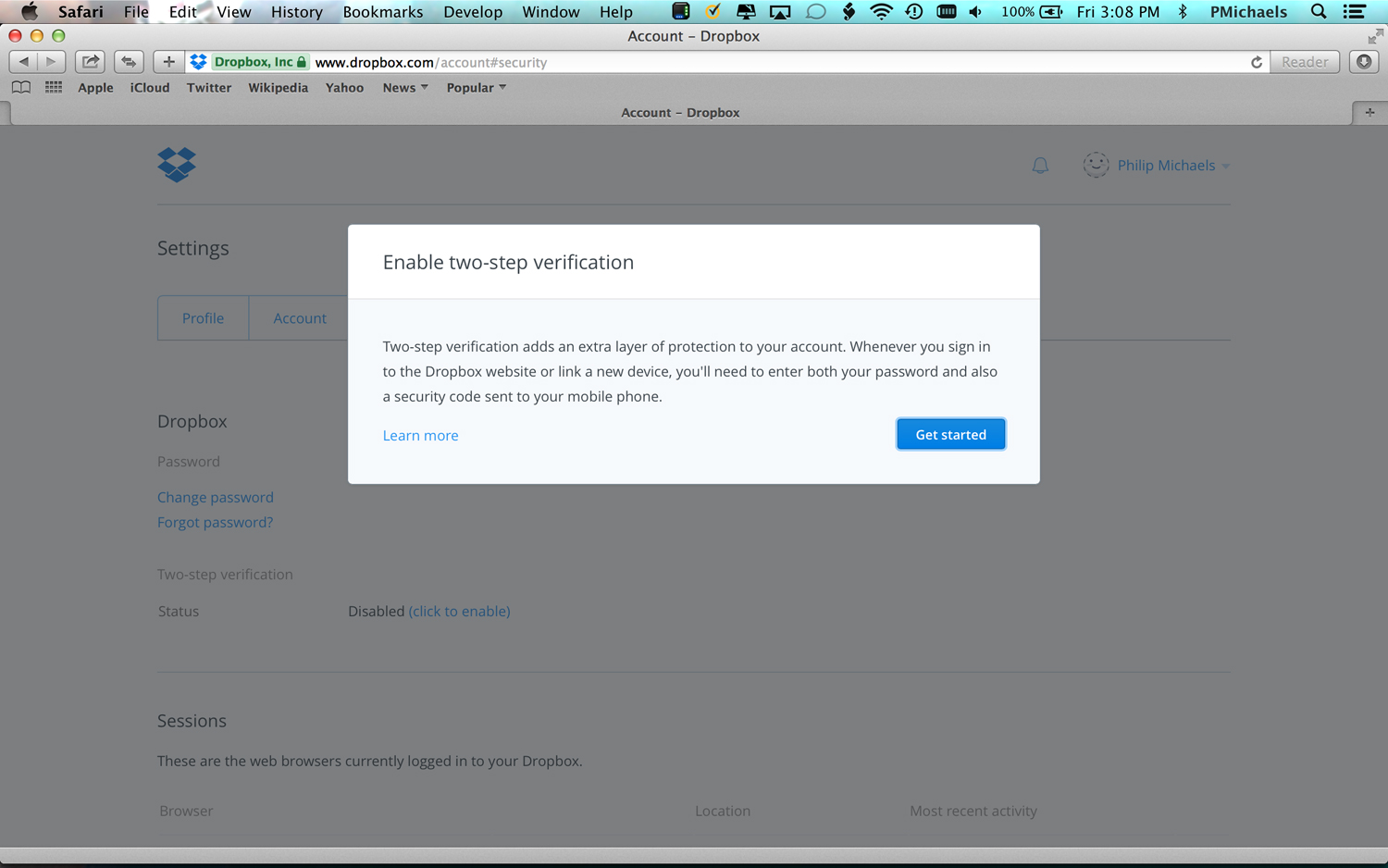
At this point, Dropbox is going to nag you to enable two-step verification if you haven't already. (And it's a good guess that you haven't if your password has remain unchanged since the first Obama term.) Here's how to do that.
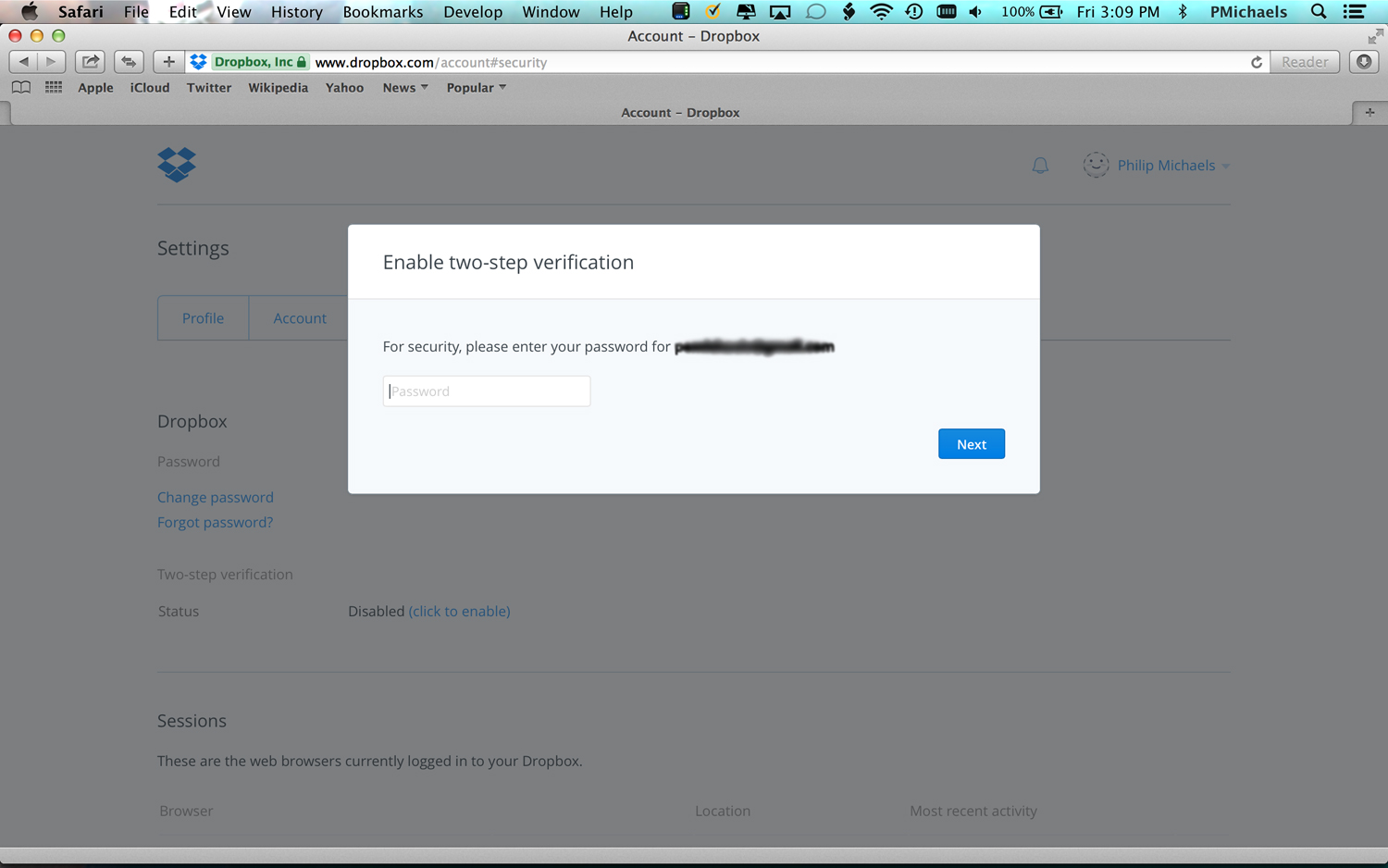
1. Enter your password when prompted.
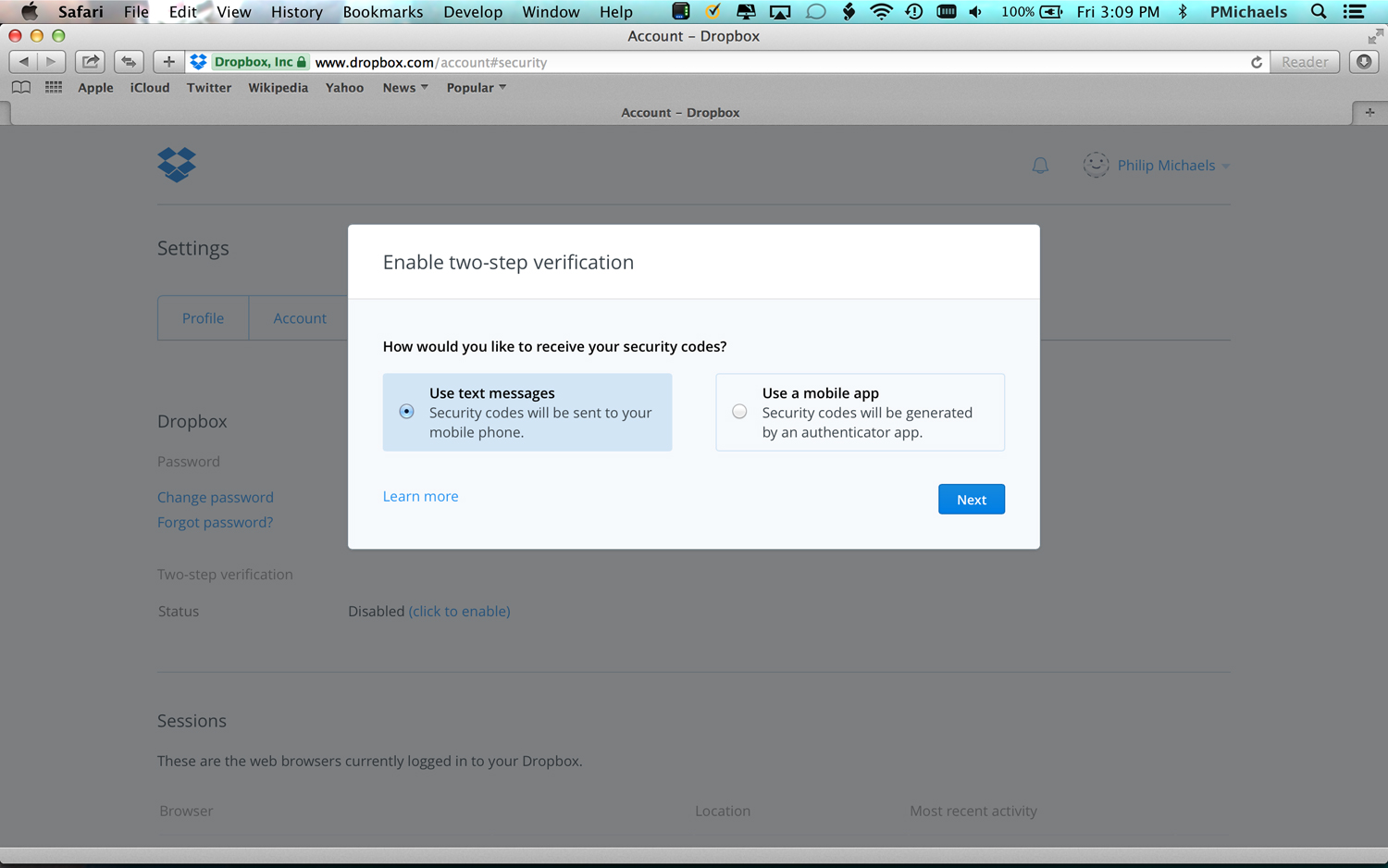
2. Select how you'd like to get your security code. In this example, we'll pick the method where Dropbox texts a code to your mobile phone.
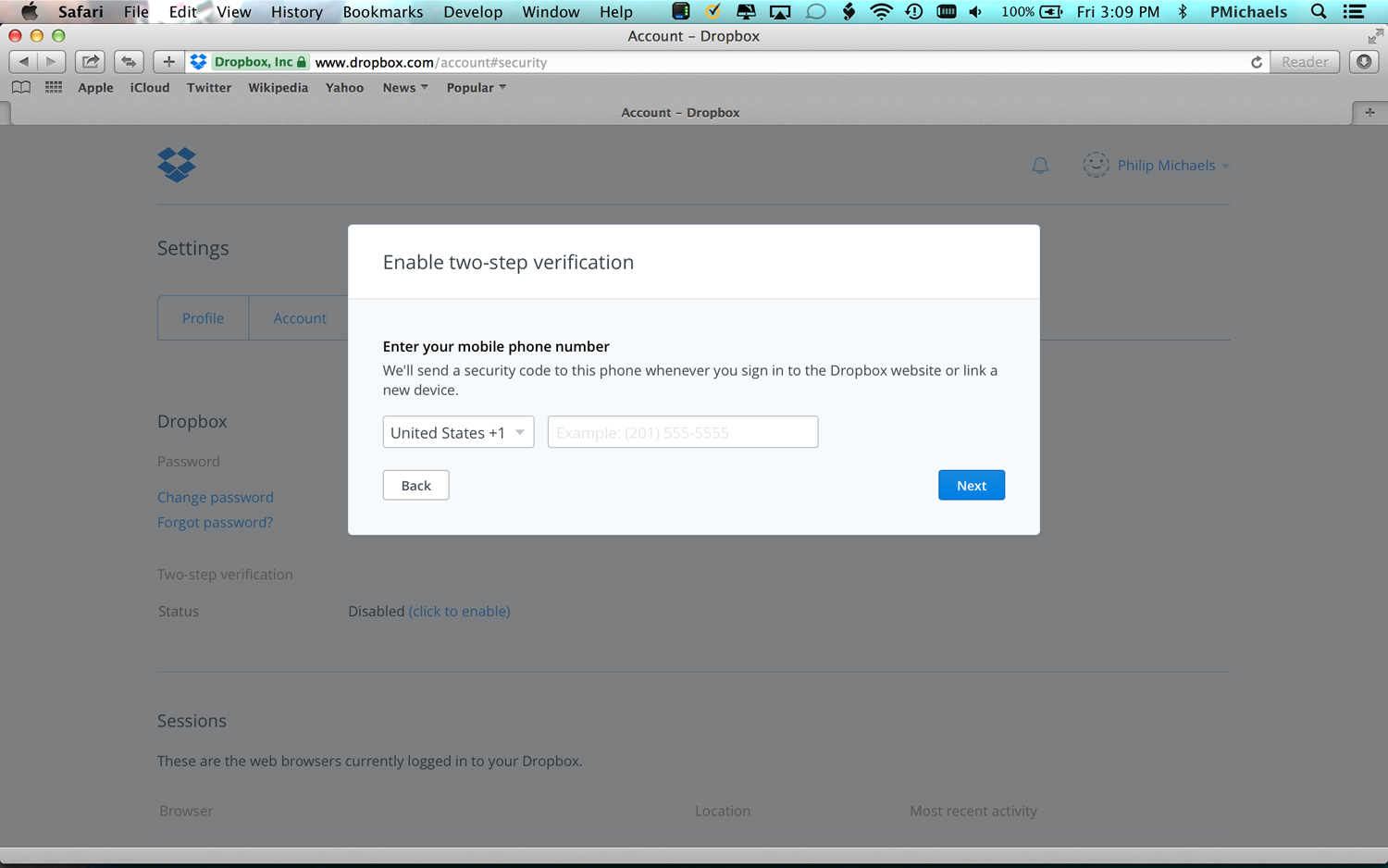
3. Enter your mobile phone number when prompted.
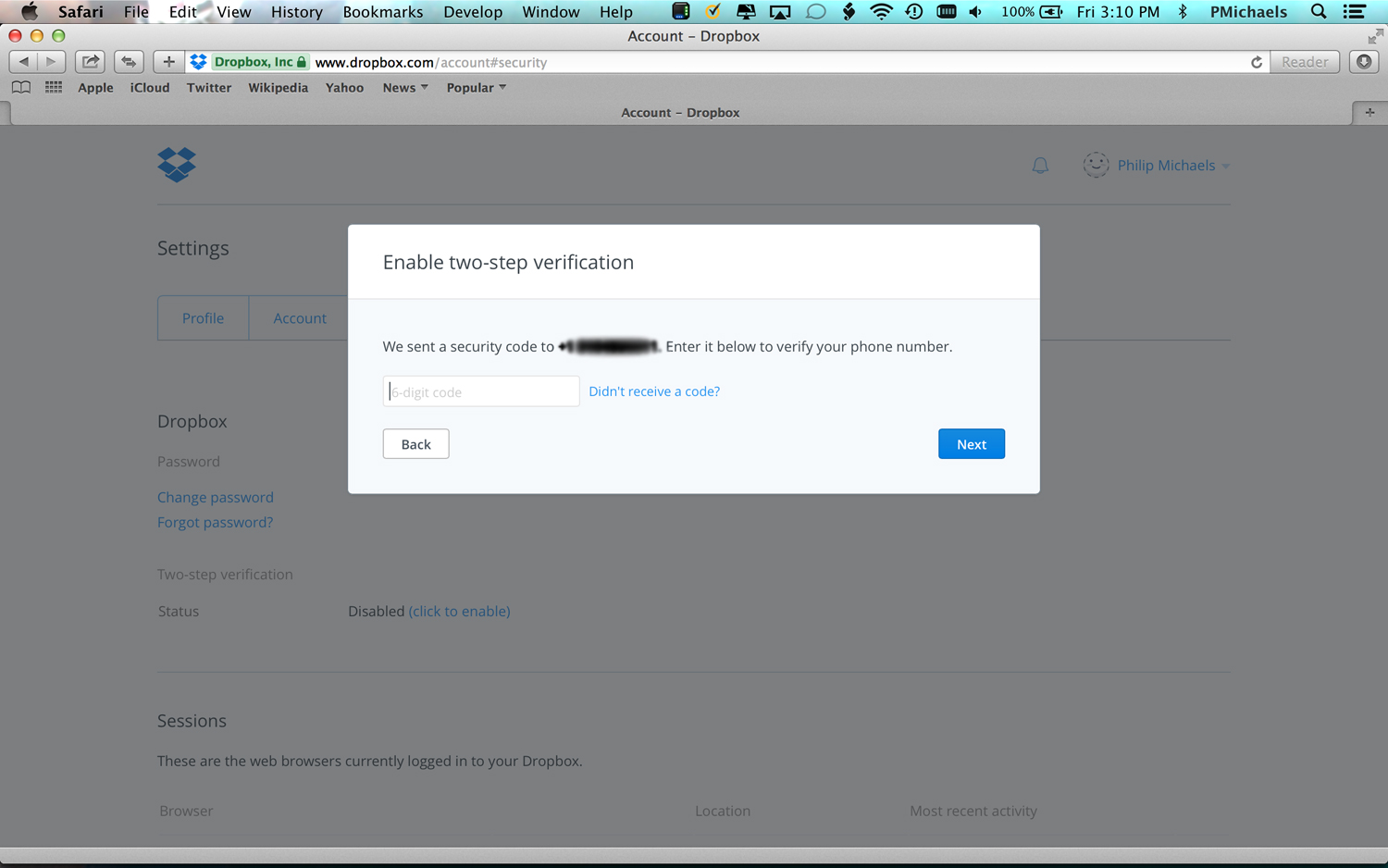
4. Enter the security code that Dropbox has sent to your mobile number.
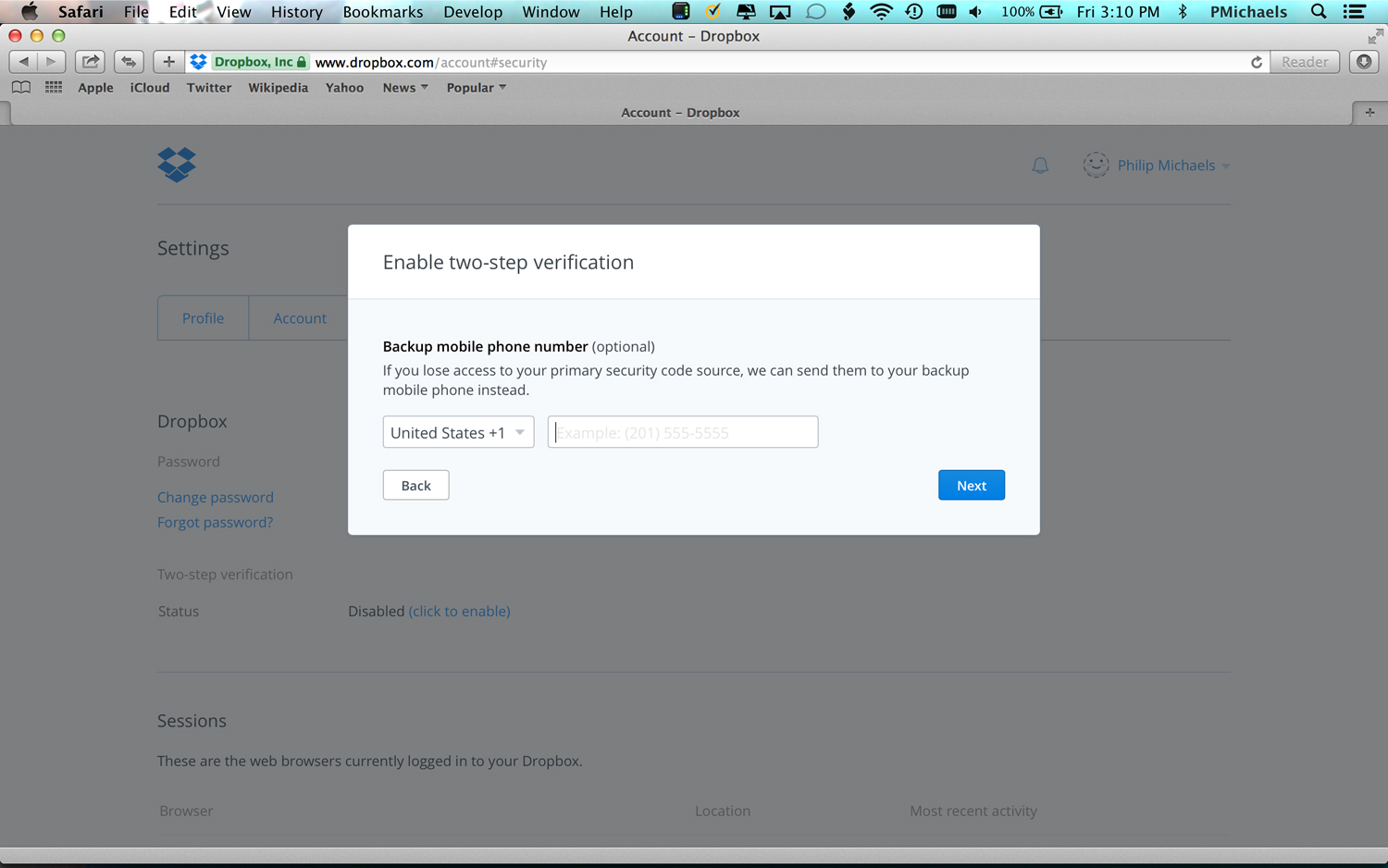
5. Enter a backup mobile phone number. This will come in handy if you ever lose your main phone.
6. At this point a screen will appear with one-time backup codes that Dropbox encourages you to write down. If you think I'm sharing that screen with you, you're nuts. At any rate, click the Enable Two-Step Verification command on this screen to complete the process.
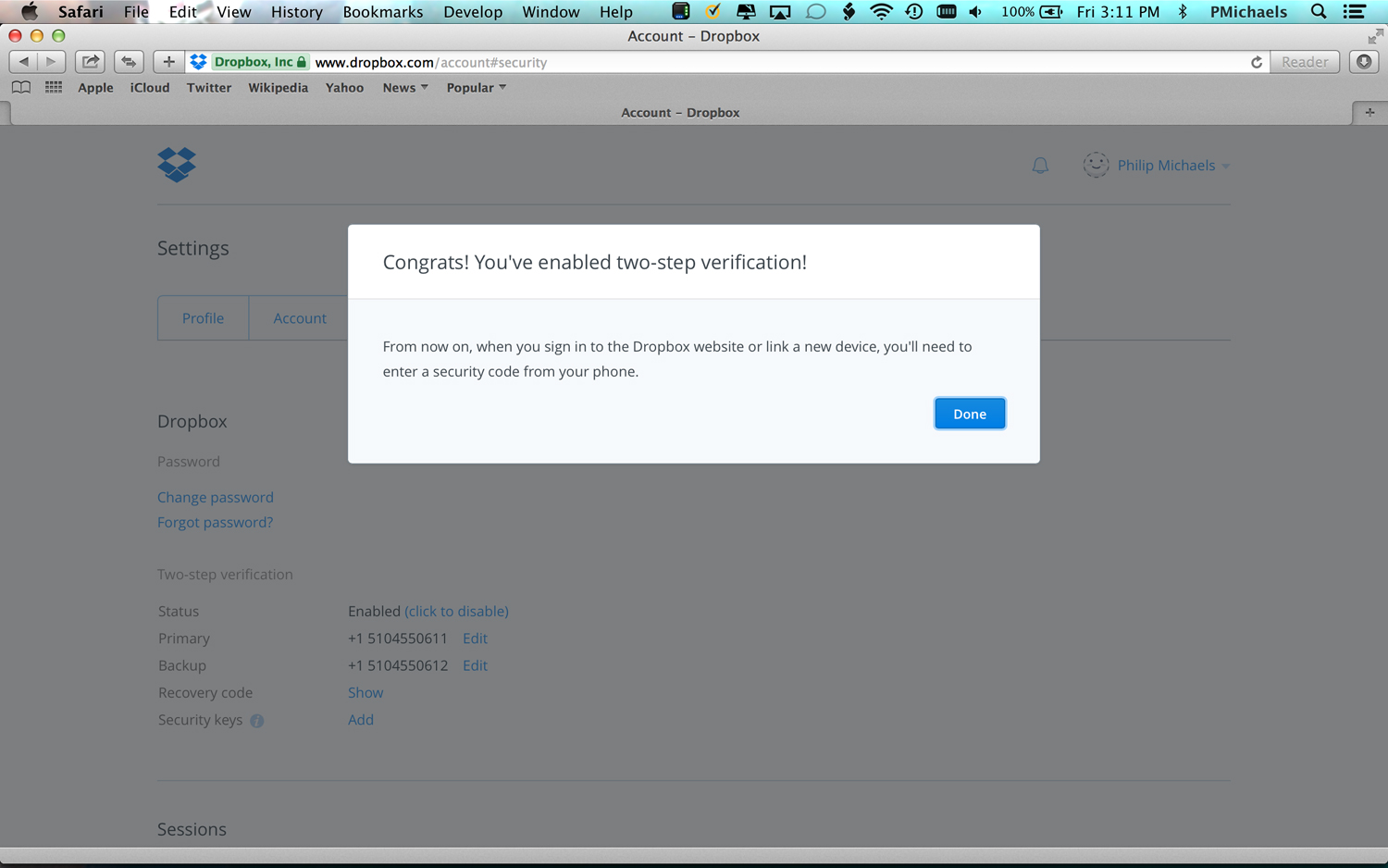
Dropbox will remind you that when you sign on to the service you'll need to enter a security code from your phone.
UPDATE: The number of Dropbox accounts affected by the 2012 breach turns out to have been more than 68 million, according to reports from VICE Motherboard and Have I Been Pwned? publisher Troy Hunt. Both Hunt and Motherboard received copies of the data dump from sources unknown.
The good news is that about half the account passwords appear to have been "hashed" — mathematically scrambled in a way designed to be impossible to reverse — with Bcrypt, a very strong hashing algorithm. The other half used the weaker SHA-1 hashing algorithm, but had been "salted" with random data to make it very difficult to match stolen hashes with precomputed hashes of common passwords.
This all means that it will be hard for password crackers to figure out most of the stolen Dropbox passwords. Nevertheless, the data is real, because Hunt confirmed that the Bcrypt hash of his wife's Dropbox password matched the one in the data dump.
"There is no doubt whatsoever that the data breach contains legitimate Dropbox passwords," Hunt wrote on his personal blog. "You simply can't fabricate this sort of thing."
Hunt has added all 68 million credential sets to Have I Been Pwned? He also offers a free notification service to alert you if your email address is part of a data breach he encounters.
Dropbox reportedly had 50 million users in November 2011, so it's possible that the breach in July 2012 involved the company's entire user set at the time.
UPDATE: Vocativ on Sept. 1 reported that all 68 million sets of credentials were being offered online for 2 bitcoin, or about $1,140 U.S. The seller, using the pseudonym "doubleflag," supplied 50 sets of credentials to Vocativ, all of which the website verified as part of the Dropbox breach.
Philip Michaels is a Managing Editor at Tom's Guide. He's been covering personal technology since 1999 and was in the building when Steve Jobs showed off the iPhone for the first time. He's been evaluating smartphones since that first iPhone debuted in 2007, and he's been following phone carriers and smartphone plans since 2015. He has strong opinions about Apple, the Oakland Athletics, old movies and proper butchery techniques. Follow him at @PhilipMichaels.

