Lost Bitcoins? Don't Click on This Malware Spam
Don't compound the pain of losing your digital shirt by clicking on this malware-laden link that promises to recover lost bitcoins.


Have you lost money in the collapse of Bitcoin exchange Mt. Gox? Are you hoping to get some of it back? Then you're the perfect target for a new malware-distributing spam campaign.
"I've noticed a scam mail that is going around the Internet recently claiming that Mt. Gox has decided to return customers their bitcoins," posted Reddit user "strongleaf" yesterday (March 3). "It goes by, 'Have you lost your MTGOX Coins? Go watch our news to claim your Bitcoins back!'"
MORE: Mt. Gox Bankruptcy: What Bitcoin Owners Need to Know
The email message then displays a link to a page on the website "bitcoinbreaknews [dot] com." That page has since been removed, but the website is still up — its front page mimics the video-player index page of The Wall Street Journal website, complete with working videos.
However, the main video screen on the fake WSJ site is replaced by a pop-up window that asks you to "install Adobe Flash Player." You can bet your bottom bitcoin that it doesn't install the real Flash Player.
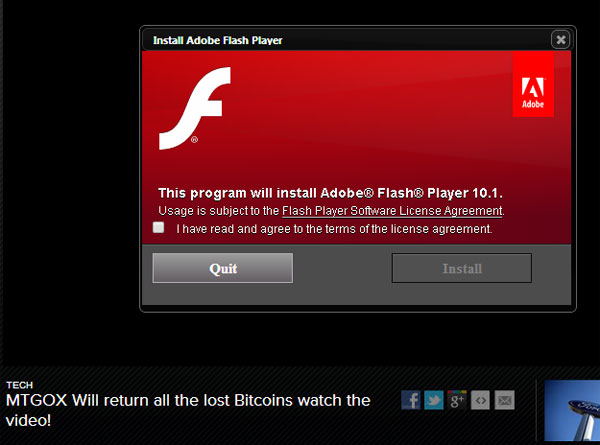
"Clicking the Install button downloads a .rar file," a type of compressed archive, wrote Malwarebytes researcher Chris Boyd in a company blog post. (Real Adobe Flash Player installers are regular Windows ".exe" files.)
The original Reddit poster downloaded and opened the archive and saw three files being extracted: a fake version of Adobe Flash Installer, a license file and a README file.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
"After clicking onto the malicious Adobe_Flash_Installer.exe, the file will immediately disappear," wrote strongleaf.
"It is apparent that the malware has installed onto the virtual machine. However, no obvious indication can be seen from [Windows] Task Manager."
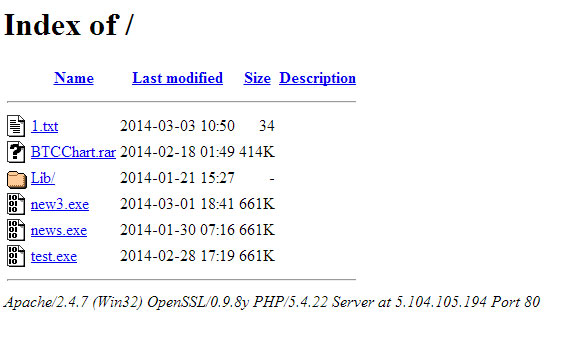
By using a packet sniffer, a software tool that analyzes Internet traffic, strongleaf saw that "the machine began to make connections to IP address 5.104.105.194 and attempts to download multiple malwares from the IP.
"By listing the directory index, the IP appears to host multiple files namely, news.exe, test.exe, BTCChart.rar," strongleaf wrote.
Tom's Guide was able to confirm strongleaf's observations, although we didn't try to install the fake Adobe Flash Player.
Needless to say, if you receive this message, don't click on the link, and don't install that bogus software, no matter how many bitcoins you lost when Mt. Gox went belly-up last week.
"Sites offering a faint ray of hope in the form of 'Mt. Gox is going to fix it all and please install this file, thanks' could well add more misery to an already considerable pile," Boyd noted.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
neieus I originally liked the idea of bitcoins but after watching graphic card prices skyrocket then something like this happened... I have never mined a bitcoin before and now I don't think I want too. It's bad enough our credit and debit cards can be hacked why add a new target?Reply -
DarkSable Seriously? Malware that you have to click on the news, decide that you want to read it enough to "install flash," learn how to unpack a .rar (if computers aren't your thing, which is true for the targets of malware and such), and THEN run a .exe.This seems like a ridiculous and ineffective way of spreading malware, especially since it applies only to those who lost bitcoin.Reply -
house70 ReplySeriously? Malware that you have to click on the news, decide that you want to read it enough to "install flash," learn how to unpack a .rar (if computers aren't your thing, which is true for the targets of malware and such), and THEN run a .exe.This seems like a ridiculous and ineffective way of spreading malware, especially since it applies only to those who lost bitcoin.
Actually, faking a legit web page and including a Flash installer (which, BTW, can happen on a legit web page, as well) instead of trying more sneaky ( and more obvious) ways is bound to work with half-PC literate people (same way that you're more likely to open the front door for someone in a nice suit than someone in dubious-looking clothing). The only thing about this scam that's not going to work is the fact that people that got into Bitcoin mining or trading are a little more than half-literate when it comes to computers. Other than that, it has more chances than the classic Nigerian princess scheme. -
Murissokah Reply"Clicking the Install button downloads a .rar file," a type of compressed archive
Glad we cleared that up. -
munch123 This is happening to my computer now, but not because of bitcoins. I am not sure how it started, but since yesterday, I have been unable to navigate to Facebook and any Google-related site, and I get a message that says my Adobe Flash Player needs updating. Interestingly, I got this warning while using Safari on my iPhone 4. Apple doesn't even support Adobe Flash Player! I didn't click to install, obviously, but I cannot get these d*mn notifications to go away. NOTE: I tried to post this by using my Google and Facebook accounts, and this site wouldn't let me because "something is interfering with your secure connection to accounts.google.com" WTH!Reply

