Bad Rabbit Ransomware: What It Is, What to Do
A ransomware worm called Bad Rabbit spread across eastern Europe Tuesday, with reports that night of outbreaks in other parts of the world.
UPDATED Oct. 26 with news that the spread of the malware seems to have stopped.
A new ransomware worm dubbed "Bad Rabbit" began spreading across the world Tuesday (Oct. 24), and it appeared to be a much-modified version of the NotPetya worm that hit eastern Europe in June.

Bad Rabbit hit corporate networks in Russia and Ukraine especially hard, according to multiple reports, and there were isolated reports of infections in Turkey, Bulgaria, Japan, Germany, Poland, South Korea and the United States by Tuesday evening.
The U.S. Computer Emergency Readiness Team (US-CERT), run by the Department of Homeland Security, issued an alert but did not specify whether any infections had been detected in the U.S.
How to Protect Yourself
All the Windows antivirus software we review at Tom's Guide, including Windows Defender, should be able to detect and stop Bad Rabbit. There also seems to be a way to "vaccinate" a machine, which may be risky. We'll go over that below.
How Bad Rabbit Works
The Bad Rabbit malware enters enterprise networks when a user on network runs a phony Adobe Flash Player installer posted on a hacked website. (Flash Player, both real and fake, is a favorite cybercriminal tool.) The initial infections came from Russian-language news sites, one of which seemed to have been actively infecting visitors even as it reported on the malware outbreak.
Some reports said websites based in Denmark, Turkey and Ireland had also been corrupted with the fake Flash installer.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
MORE: Best Antivirus Software and Apps
After it has infected the initial machine in a network, Bad Rabbit uses the open-source tool MimiKatz to find any login credentials stored on the machine, then tries to use those credentials to spread to other machines. It also has a hard-coded list of dozens of the most commonly used passwords.
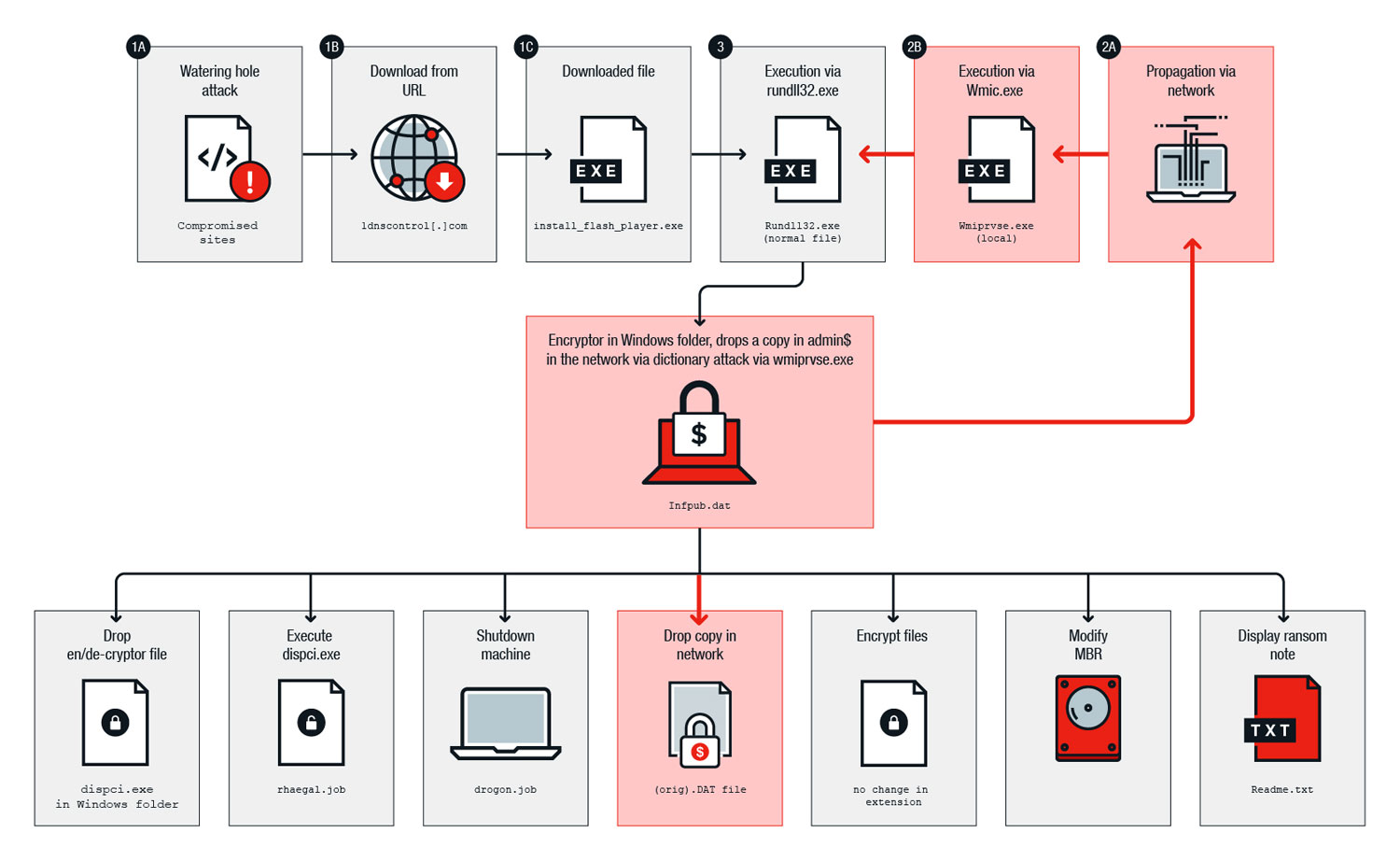
There were also some indications that BadRabbit uses the NSA's EternalBlue tool, used by both NotPetya and the WannaCry ransomware worm that spread in May, to spread through a local network, although other reports disputed that and said Bad Rabbit simply used stolen and weak passwords to spread.
Once it has spread as far as it can through a network, Bad Rabbit encrypts all files of commonly used Windows Office, image, video, audio, email and archive filetypes on infected Windows machines, using the open-source DiskCryptor utility. It then replaces a PC's Master Boot Record, reboots the machine and posts a ransom note. The victim is instructed to send 0.05 bitcoin (about $280) to a specific Bitcoin wallet.

The Slovak antivirus company ESET reported that the metro system in Kiev, the Ukrainian capital, and the main airport in Odessa, another large Ukrainian city, had been hit by the ransomware.
Game of Thrones fans may be bemused to learn that three routines carried out by the malware are named Drogon, Rhaegal and Viserion, after three dragons in the series. Part of the installer is called Gray Worm, the name of a military commander in the series.
How to 'vaccinate' your computer against Bad Rabbit
Amit Serper, a malware researcher at Cybereason, said on Twitter that he'd found a way to immunize a computer against Bad Rabbit infection.
"Create the following files c:\windows\infpub.dat && c:\windows\cscc.dat - remove ALL PERMISSIONS (inheritance) and you are now vaccinated. :)" Serper tweeted.
You'll need administrator rights on a Windows machine to do this, and you'll need to know how to set up both files so that NO users have read, write or execute permissions. To make it easier, one of Serper's colleagues at Cybereason posted instructions to walk you through the process.
We haven't tried out Serper's method ourselves, and while we can vouch for his character — he's a well-known and well-respected malware researcher — you'll be doing this at your own risk.
UPDATE Oct. 26: We finally tried Serper's vaccination method and, while we didn't download and install a copy of Bad Rabbit to see if we were protected, we can happily report that the procedure seems to have had no ill effect upon our Windows 10 machine.
Meanwhile, the Bad Rabbit infection spread seems to have stopped, or at least slowed to a crawl. Symantec reported that the vast majority of Bad Rabbit infections occurred within a couple of hours on Tuesday, and on Wednesday, multiple security firms reported that Bad Rabbit's distribution and control websites had been taken offline.
There were indications that the perpetrators were the same as those behind the NotPetya attacks upon Ukrainian businesses in May, but as with all possibly state-sponsored malware, attribution is never certain.
For the moment, our recommendations remain the same — install and run good antivirus software, which will stop Bad Rabbit infection. Following Amit Serper's inoculation procedure doesn't seem to hurt either.
Best Antivirus Software



Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
darrenskirvin @Echo offReply
Echo **************************************
Echo * Create files and revoke permissions*
Echo **************************************
@echo "created-this-to-stop-bad-rabit" >c:\windows\infpub.dat
@echo "created-this-to-stop-bad-rabit" >c:\windows\cscc.dat
icacls c:\windows\infpub.dat /inheritance:r
icacls C:\windows\cscc.dat /inheritance:r
Create this in a .bat or .cmd -
Paul Wagenseil Reply20307319 said:@Echo off
Echo **************************************
Echo * Create files and revoke permissions*
Echo **************************************
@echo "created-this-to-stop-bad-rabit" >c:\windows\infpub.dat
@echo "created-this-to-stop-bad-rabit" >c:\windows\cscc.dat
icacls c:\windows\infpub.dat /inheritance:r
icacls C:\windows\cscc.dat /inheritance:r
Create this in a .bat or .cmd
Thanks! For our non-technical readers, you would take the above steps in a command-line window, which you can get by typing "cmd" into the search field you get when clicking on the Windows logo in the bottom left of your screen. Make sure your account has administrator privileges. -
eli.lingard MERGED QUESTIONQuestion from eli.lingard : "What to do about Bad Rabbit?"Reply
I'm sorry if I've already posted this before - I wasn't sure if it had been sent through or not!! I have AVG free installed on my Windows 8 PC, but I'm worried that it won't be enough to stop Bad Rabbit if it ever infects my PC. I can't seem to run windows defender and I'm confused as to why it might be better than AVG if it doesn't have the best ratings.
I can't really afford anything too heavy, but I really don't want to be under attack!
What would you recommend? -
eli.lingard Reply20307752 said:20307319 said:@Echo off
Echo **************************************
Echo * Create files and revoke permissions*
Echo **************************************
@echo "created-this-to-stop-bad-rabit" >c:\windows\infpub.dat
@echo "created-this-to-stop-bad-rabit" >c:\windows\cscc.dat
icacls c:\windows\infpub.dat /inheritance:r
icacls C:\windows\cscc.dat /inheritance:r
Create this in a .bat or .cmd
Thanks! For our non-technical readers, you would take the above steps in a command-line window, which you can get by typing "cmd" into the search field you get when clicking on the Windows logo in the bottom left of your screen. Make sure your account has administrator privileges.
I'm afraid I'm really not technically minded; what will this command do, and how exactly do I type it in cmd? Do I need to type all of the commands listed above after the first line of text that comes up in my cmd box? -
Paul Wagenseil Reply20308024 said:MERGED QUESTIONQuestion from eli.lingard : "What to do about Bad Rabbit?"
I'm sorry if I've already posted this before - I wasn't sure if it had been sent through or not!! I have AVG free installed on my Windows 8 PC, but I'm worried that it won't be enough to stop Bad Rabbit if it ever infects my PC. I can't seem to run windows defender and I'm confused as to why it might be better than AVG if it doesn't have the best ratings.
I can't really afford anything too heavy, but I really don't want to be under attack!
What would you recommend?
AVG Free should be enough to stop Bad Rabbit. Make sure the AVG software automatically updates every day, however. You're not able to run Windows Defender because you have AVG installed, and that's fine: AVG is better than Windows Defender anyway. -
Paul Wagenseil Reply20308023 said:20307752 said:20307319 said:@Echo off
Echo **************************************
Echo * Create files and revoke permissions*
Echo **************************************
@echo "created-this-to-stop-bad-rabit" >c:\windows\infpub.dat
@echo "created-this-to-stop-bad-rabit" >c:\windows\cscc.dat
icacls c:\windows\infpub.dat /inheritance:r
icacls C:\windows\cscc.dat /inheritance:r
Create this in a .bat or .cmd
Thanks! For our non-technical readers, you would take the above steps in a command-line window, which you can get by typing "cmd" into the search field you get when clicking on the Windows logo in the bottom left of your screen. Make sure your account has administrator privileges.
I'm afraid I'm really not technically minded; what will this command do, and how exactly do I type it in cmd? Do I need to type all of the commands listed above after the first line of text that comes up in my cmd box?
These steps apparently will prevent the Bad Rabbit malware from running on your machine in case of infection. We've linked to this in our article, but Cybereason has a fairly plain-English explanation here: https://www.cybereason.com/blog/cybereason-researcher-discovers-vaccine-for-badrabbit-ransomware
-
darrenskirvin Reply20307752 said:20307319 said:@Echo off
Echo **************************************
Echo * Create files and revoke permissions*
Echo **************************************
@echo "created-this-to-stop-bad-rabit" >c:\windows\infpub.dat
@echo "created-this-to-stop-bad-rabit" >c:\windows\cscc.dat
icacls c:\windows\infpub.dat /inheritance:r
icacls C:\windows\cscc.dat /inheritance:r
Create this in a .bat or .cmd
Thanks! For our non-technical readers, you would take the above steps in a command-line window, which you can get by typing "cmd" into the search field you get when clicking on the Windows logo in the bottom left of your screen. Make sure your account has administrator privileges.
-
darrenskirvin My pleasure. You can put this in a logon script for your active directory connected windows clients.Reply -
eli.lingard Reply20308302 said:20308024 said:MERGED QUESTIONQuestion from eli.lingard : "What to do about Bad Rabbit?"
I'm sorry if I've already posted this before - I wasn't sure if it had been sent through or not!! I have AVG free installed on my Windows 8 PC, but I'm worried that it won't be enough to stop Bad Rabbit if it ever infects my PC. I can't seem to run windows defender and I'm confused as to why it might be better than AVG if it doesn't have the best ratings.
I can't really afford anything too heavy, but I really don't want to be under attack!
What would you recommend?
AVG Free should be enough to stop Bad Rabbit. Make sure the AVG software automatically updates every day, however. You're not able to run Windows Defender because you have AVG installed, and that's fine: AVG is better than Windows Defender anyway.
Brilliant, thank you! -
Avast-Team Our threat intelligence team put together a detailed synopsis of BadRabbit, including where it spread to and some of its tricks to avoid detection, if anyone is curious to learn more: https://blog.avast.com/its-rabbit-season-badrabbit-ransomware-infects-airports-and-subwaysReply
EDIT: Can confirm also that Avast and AVG both are detecting BadRabbit (this is also mentioned in the blog)

