Watch Kodi on Amazon Fire TV? You're About to Be Hacked
Installing Kodi on an Amazon Fire TV device leaves it vulnerable to infection by a crypocurrency-mining botnet.
UPDATED 9:45 a.m. ET Tuesday June 12 with evidence that Amazon Fire TVs are indeed being infected by ADB.Miner. Originally published at 7:00 p.m. ET June 11.
Thousands of Amazon Fire TV devices are vulnerable to infection by a cryptocurrency-mining botnet, Tom's Guide has discovered.
The devices are vulnerable because their owners have disabled basic security protections to install Kodi and other piracy-related streaming apps. Doing so enables an Android diagnostic tool and opens up a specific port to the internet, which the botnet scans for and detects.
As of Monday afternoon (June 11), some 2,100 devices in the United States, out of nearly 17,000 devices worldwide, were vulnerable to this exploit, according to a check of the Shodan search engine for internet-connected devices. The vast majority of the U.S. devices were Amazon Fire TV and Fire Stick devices. Infection by the botnet might mean that your device could slow down or malfunction — or possibly even overheat and be permanently damaged.
MORE: Why You Shouldn't Root Your Android Phone
How to Protect Yourself
If you've rigged up Kodi or another unauthorized app, check your Fire TV settings in Settings > Device. Select Developer options, and then select ADB debugging and turn it off.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Doing this may disable your Kodi app. We haven't tried it ourselves. But leaving ADB debugging on sends a bright beacon out into the internet screaming "PLEASE INFECT ME."
That's because ADB debugging, otherwise known as Android Debug Bridge, Developer Mode or Developer Options, isn't meant to be accessed by regular Android users. It lets you access the Android device's innards via port 5555 from a PC connected via a USB cable or over Wi-Fi. It's meant to troubleshoot or repair Android devices that may not be working properly.
What ADB Is
Google keeps ADB well hidden. You have to go into Settings, find About Phone, tap on Build or Build Number seven times, enter your screen-lock passcode, go back to the main settings screen and select Developer Mode or Developer Options, before finally scrolling down and enabling USB debugging or Wireless ADB debugging.
Amazon, on other hand, makes it super-easy to make your device totally vulnerable to hackers. You go into Settings, click Device, click on Developer options and toggle ADB debugging. Boom! You're done.
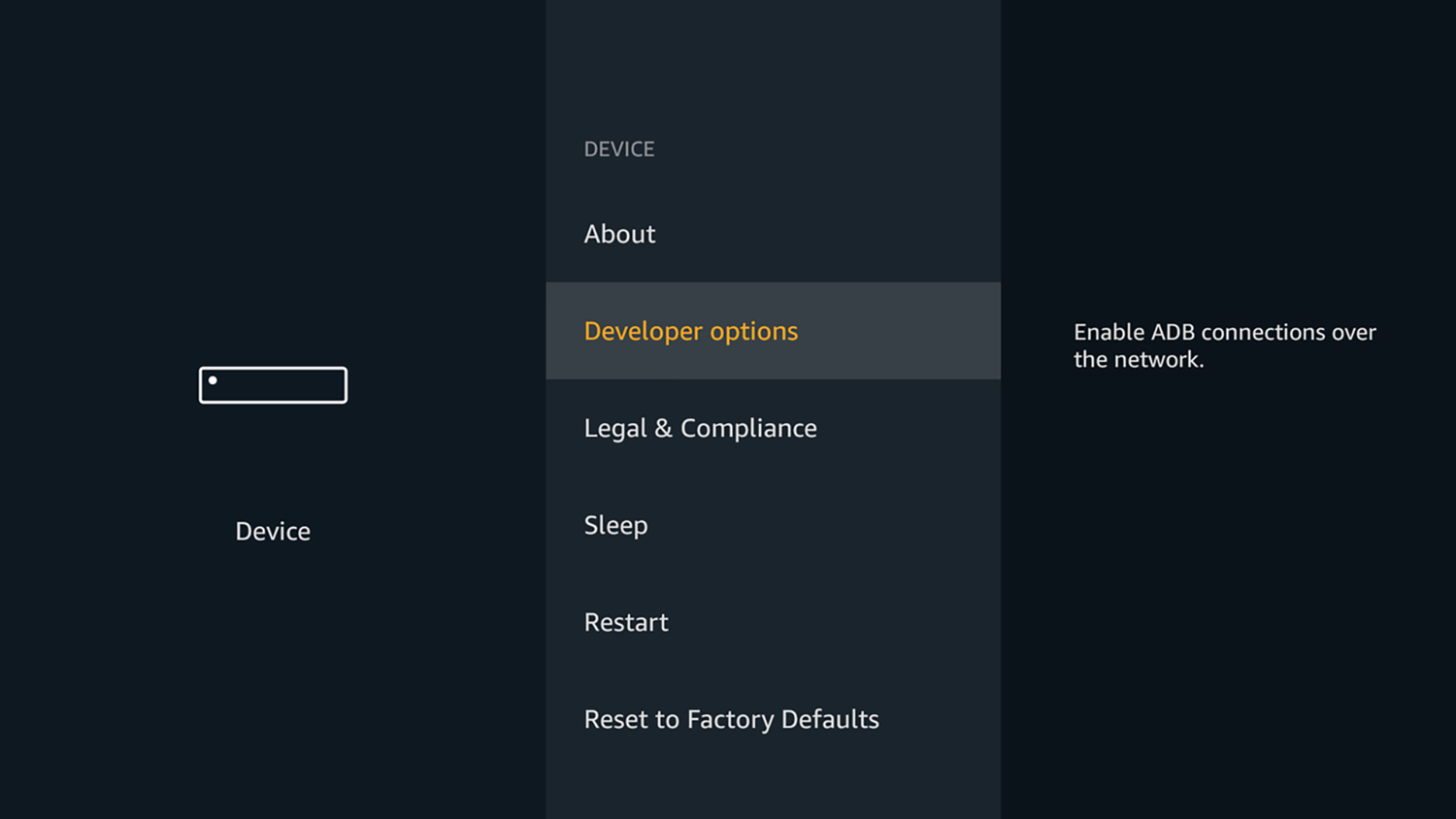
The above steps are the first ones in practically every guide to installing Kodi on an Amazon Fire TV device — including our own.
All-Device Botnet
These instructions have apparently led thousands of Amazon Fire TV owners to make their devices totally vulnerable to ADB.Miner, a botnet that is scanning the internet for Android devices with port 5555 open and infecting them with a program that "mines" the Monero cryptocurrency.
Kevin Beaumont, an English security researcher, wrote in a blog post Friday (June 8) that thousands of devices worldwide were vulnerable to ADB.Miner, according to a port scan using the Shodan search engine for internet-connected devices.
"Vendors have been shipping products with Android Debug Bridge enabled," Beaumont wrote. "We've found everything from tankers in the US to DVRs in Hong Kong to mobile telephones in South Korea. As an example, a specific Android TV device" — likely a low-end set-top box not available in North America — "was also found to ship in this condition."
Amazon, Prime Target
Beaumont was especially worried about cheap Android phones shipping with ADB enabled. We checked a dozen phones we had in the Tom's Guide lab, and not one had it turned on.
But then we checked the Shodan scan results online and noticed that a lot of the U.S.-based devices were identified as "AFTS," "AFTM" or "AFTT." Those are the identifying codes, respectively, for the second-generation Amazon Fire TV (internal name "Sloan"), first-generation Amazon Fire Stick (internal name "Montoya") and second-generation Fire Stick (internal name "Tank").
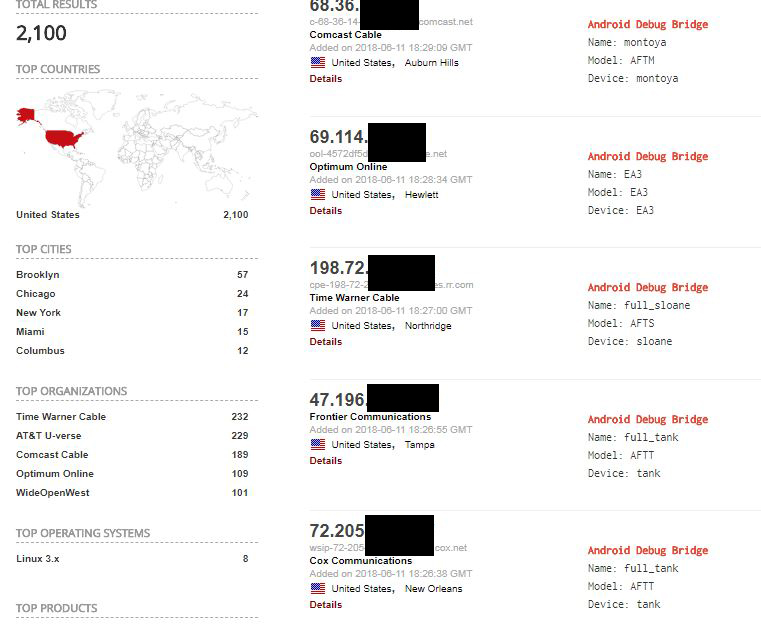
We filtered the Shodan results to just show U.S. hits, and it was almost all Fire Tv and Fire Stick devices. Of the first 100 results, only seven were non-Fire TV devices — presumably phones that had been rooted.
We could get moralistic and shake our fingers and scold users for disabling their Amazon Fire TV protections to install Kodi. But users are going to want to get free stuff. What really should happen is that Amazon makes it harder to access developer mode. Doing so might put a small dent in Amazon Fire TV sales, but it's not like Amazon doesn't have other sources of revenue.
UPDATE: AFTV News reported yesterday (June 11) that reports of infection by ADB.Miner have indeed been appearing in Fire TV forum chats for a couple of months. The malware appears as a simple app called "Test," but it doesn't appear in the regular list of apps — you have to install an alternate app manager called Total Commander to spot it.
AFTV has detailed instructions on how to remove or disable ADB.Miner, ranging from factory-resetting the Fire TV device to (and this is pretty clever) updating the malware itself to a version that is harmless but prevents re-infection. But all three methods recommend that you turn off the ADB function in the Settiings after you're done using it.
Image credits: Tom's Guide
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
michael.stringer.2.0 One big caveat - if you're behind a firewall/wifi-router, 5555 from the Internet is blocked. So, if you have an address like 192.168.x.x, or 10.x.x.x, you're fine - the Internet cannot regularly access your Fire Stick.Reply -
Paul Wagenseil Reply21050088 said:One big caveat - if you're behind a firewall/wifi-router, 5555 from the Internet is blocked. So, if you have an address like 192.168.x.x, or 10.x.x.x, you're fine - the Internet cannot regularly access your Fire Stick.
In theory, yes. But I'd bet almost all the devices showing up on Shodan are connected to home Wi-Fi routers. Unless there's some reason I don't know of, I can't imagine many people are plugging their Fire TV devices directly into cable or DSL modems without a router as intermediary.

