Wall of Sheep catches security pros at Black Hat
Las Vegas (NV) – The security pros at Black Hat got a little surprise this year with the appearance of the infamous Wall of Sheep.
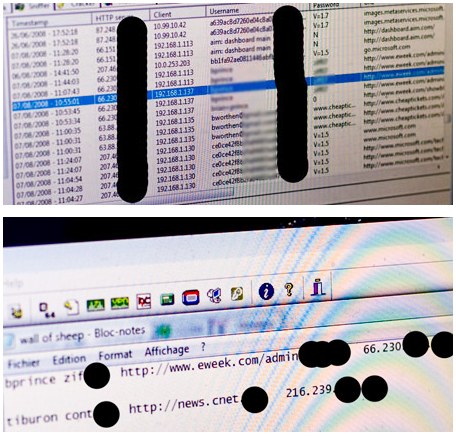
Using a batch of freely available scanning tools – including a brand new live CD distribution called
OSWA – the team examines traffic and then posts them on a projector for everyone to see. By Thursday afternoon (the second day of the conference), the Wall of Sheep displayed approximately 30 logins to various services like http, ICQ, IMAP, POP3 and FTP. IMAP email seemed to be the richest treasure trove of information as team members showed me logins and email folders. “Look, this folder is labeled CISSP,” said one guy.
The victims appeared to be from several countries including Japan, Taiwan, Germany and Czech Republic. One victim was even caught logging into their email account at a major Japanese financial institution. Some people were nabbed multiple times and one “highly credential person” (think lots of abbreviations behind the name) with a large company had four of her accounts briefly shown. The logins were removed after she talked to the Wall of Sheep team members.
Riverside, a security expert that helps run the Wall of Sheep, told us that anyone caught on the wall can request to have their information removed. He added that most people were humbled by getting caught and that the victim mentioned above has already started a company-wide review of security policies.
Mario De Tore, a first year Wall of Sheep volunteer, was finding user names and passwords with ease. He does IDS (intrusion detection system) monitoring for work and told us that he was surprised that so many people at Black Hat were insecure.
But it hasn’t been all fun and games for the Wall of Sheep team. Several equipment failures, like the failure of an 11 year-old Sony Vaio laptop and a blown power supply on a Compaq desktop, have slowed the scanning. Also people are actively trying to hack back at the Wall of Sheep, but the team has hardened their boxes to NIST and NSA standards. Packets are filtered through several intrusion detection systems and four to five firewalls and according to Riverside, all settings like ARP mappings are statically set.
Attendees are also purposely logging into services with a bogus username and password, just to have their traffic sniffed and placed on the Wall. But these aren’t because the team goes through the sniffed logins and verifies that they actually work.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
It’s still too early to tell if Black Hat attendees are any smarter about security than Defcon goer, but we’ve already seen some interesting trends. Riveside told us that he’s seeing multiple logins where people are using the same password for several services. “Work, personal, chat … their passwords are all the same,” he said. Riverside gave one example where a victim’s laptop automatically logged into their instant messenger and then used the same login info for the corporate VPN.
Riverside hopes the IT administrators and managers at Black Hat will start a top-down change in security thinking. “When people get hacked at Defcon, it’s their personal machine. Here [at Black Hat] it’s their corporate machines using corporate images. The hacking community has a better understanding about security, it’s the managers and higher-ups that don’t.”
Humphrey Cheung is a consulting systems engineer for Cisco Meraki who has also worked as a freelance videographer and reporter. He was previously a senior editor for Tom's Hardware and his work has also been featured on Tom's Guide, CNN, The New York Times, NBC, FOX, plus many other publications.
-
It is nice to see people claiming to be the best of the best of security falling for this obvious bit of retarded. Who goes to a security confrence and checks ANYTHING over a wireless connection or air card?Reply
That is proof those people don't belong in their positions.
If you can't handle situational awareness at a confrence how can you handle it when it matters?
