Internet
Explore Internet
Latest about Internet

Chrome extensions with 4 million installs are putting your privacy at risk — how to stay safe
By Anthony Spadafora published
Browser extensions let you customize and add new features to Google Chrome but these 35 unlisted ones require sensitive permissions that could put your privacy at risk.
Proton VPN review
By Olivia Powell last updated
VPN Proton VPN is a very capable VPN, and will appeal to those looking for a more techy experience. However, it can't quite match the best of the best.

The best China VPN: working services right now
By Mo Harber-Lamond last updated
VPN A China VPN is essential for anyone traveling to the country – but not every provider works. Here are the very best VPNs for China on the market.

Post-quantum VPNs – necessary now or a premature move?
By George Phillips published
Post-quantum encryption will become the new encryption standard, protecting us from quantum computers. But why haven't all leading VPNs implemented it yet?
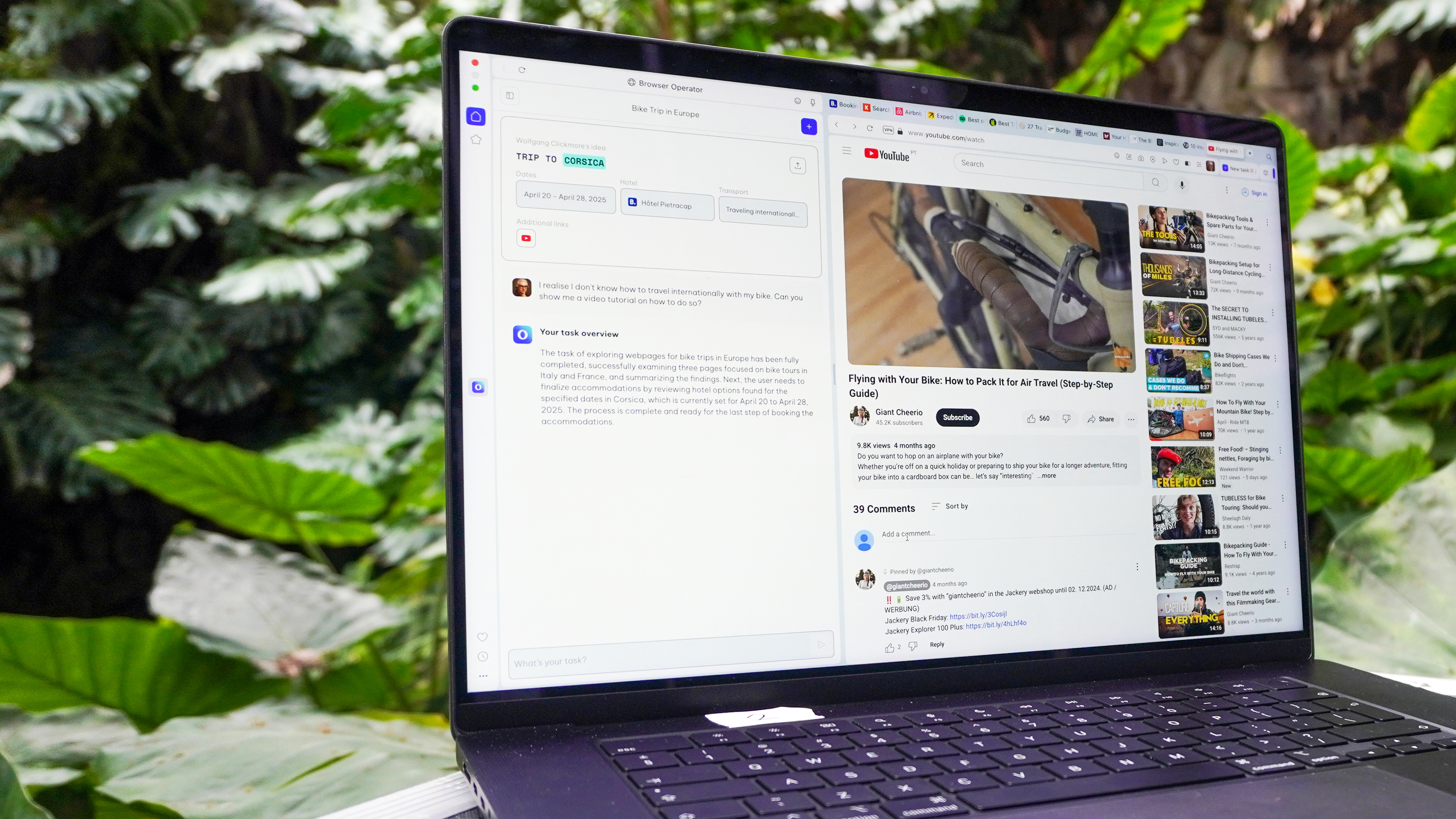
Exclusive: I just tested the world's first agentic AI web browser and it blows away ChatGPT
By Jason England last updated
I just got a world exclusive hands-on with Opera’s Browser Operator. Not only is it the fastest and smartest agentic AI I’ve seen, it’s a glimpse of the next generation web browser.

Hackers are using fake Google Play Store pages to infect Android phones with a dangerous trojan — how to stay safe
By Amber Bouman published
A new SpyNote malware campaign has been discovered online targeting Android users via fake Google Play Store pages.

Best Warzone VPN: how to get easy lobbies by avoiding SBMM
By Krishi Chowdhary last updated
VPN A VPN for Warzone is the perfect tool for bagging more kills and avoiding SBMM. Here the top 5 Warzone VPNs on the market today.

Windows PCs under threat from zero-day flaw used in ransomware attacks — update your computer right now
By Amber Bouman published
Microsoft has revealed that a recently patched Windows zero-day flaw was used to spread malware and launch ransomware attacks.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!


