These popular apps are being mimicked to spread malware — here's how to protect yourself
Skype, Adobe Acrobat and VLC top the list with Steam and Zoom mimics also found

A dichotomy exists in today's tech landscape, that while an awareness of malware and its dangers has perhaps never been greater, it becomes harder and harder to avoid as distribution techniques get ever more devious.
As if there weren't enough ploys around already, recent research by internet security analysis company VirusTotal shows that some of the biggest applications around are commonly mimicked for nefarious purposes.
Skype, Adobe Acrobat and VLC Media Player have been revealed by the company as the three apps most commonly imitated by attackers online. With other household names on the list, including 7Zip, Microsoft Teams, Steam, Zoom and WhatsApp. These apps are commonly being faked online, using imitations of their icons hosted on third party sites, which trick users into downloading illegitimate software and subsequently installing malware on their devices.
Simplistic social engineering
"One of the simplest social engineering tricks," as VirusTotal puts it, is for attackers to merely clone the icons of these popular and trusted applications, thereby convincing users to download and run malicious software, infecting their systems.
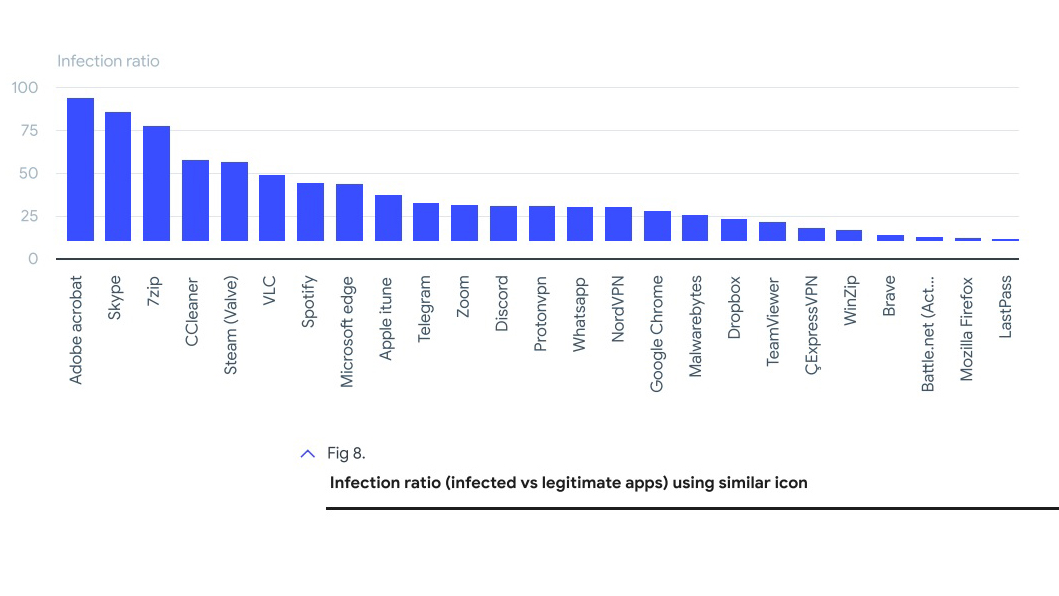
While VLC Media Player was third in terms of most commonly imitated, it was Adobe Acrobat, Skype and 7Zip which were found to have the highest infection ratio — that is, the highest number of decoys versus legitimate apps out there for download — making them, the report says, "the top three applications and icons to be aware of" when downloading software online.
This isn't the only confidence trick that the analysis company picked up on in their reports, however, and similar behaviour has been identified when it comes to imitating websites. Essentially, the company found a number of malicious websites masquerading themselves as legitimate by copying the favicon of the real site, i.e. the small logo that appears in browser tabs.
The most commonly cloned websites were found to be WhatsApp, Instagram, Facebook, iCloud and Discord, while the highest infection ratio was found with iCloud, WhatsApp and Skype.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The report also details cases of software certificates — for a long time a trusted way of verifying the legitimacy of programs — being stolen by malicious developers and used "to sign their malware, making them appear as though they came from legitimate software makers." A high profile case of this, the research notes, was Nvidia having their code signing certifications stolen by the ransomware group LAPSUS$.
Perhaps most scarily, VirusTotal also note a high prevalence of malware being bolted on to installation files within legitimate software packages. As the malware comes alongside legit software, the malicious code avoids raising suspicion and therefore detection. "These supply chain attacks work," the report asserts, "when attackers get access to the official distribution server, source code or certificates."
"Focusing in on the top legitimate installers executed by malware, we found installers that combined malware with installers for other popular software like Google Chrome, Malwarebytes, Windows Update, Zoom, Brave, Firefox, ProtonVPN, and Telegram amongst others," it continues.
How to protect yourself from malware

While these tricks may be cunning, there are some easy ways to keep yourself safe from malware. Here's how.
1. Ensure you are running one of the best antivirus software packages, such as Norton 360 Deluxe or Bitdefender Antivirus Plus, as these feature strong anti-malware protection which should also pick up on malware even if it possesses legitimate signed software certificates. Run system scans regularly and delete any threats.
2. Only download software from official company websites, and avoid downloading from third party sites whenever possible. Don't assume that because an application or website has a recognizable logo, that it is legitimate.
3. If you've already downloaded software from a third party site, or if you have to use a site to download less well-known software, scan any files downloaded for malware using antivirus software before executing them and run a system scan if you've already installed them.

Peter is Reviews Editor at Tom's Guide. As a writer, he covers topics including tech, photography, gaming, hardware, motoring and food & drink. Outside of work, he's an avid photographer, specialising in architectural and portrait photography. When he's not snapping away on his beloved Fujifilm camera, he can usually be found telling everyone about his greyhounds, riding his motorcycle, squeezing as many FPS as possible out of PC games, and perfecting his espresso shots.
