Safari bug could reveal your browsing history on Mac, iPhone or iPad
A bug in Safari 15 allows websites to reveal content of tabs and even deduce your identity

Update: Apple has released an update for iOS 15 to plug the security hole Safari.
A bug in Apple's Safari browser could reveal your recent web history and potentially your identity to any website you’re using. And while Mac users can simply switch to another browser, iPad and iPhone users are out of luck, because every alternative browser is also impacted.
In a blog post published on Friday, browser fingerprinting service FingerprintJS explained the root of the problem, which affects Safari 15 for Mac and all versions on iOS 15 and iPadOS 15.
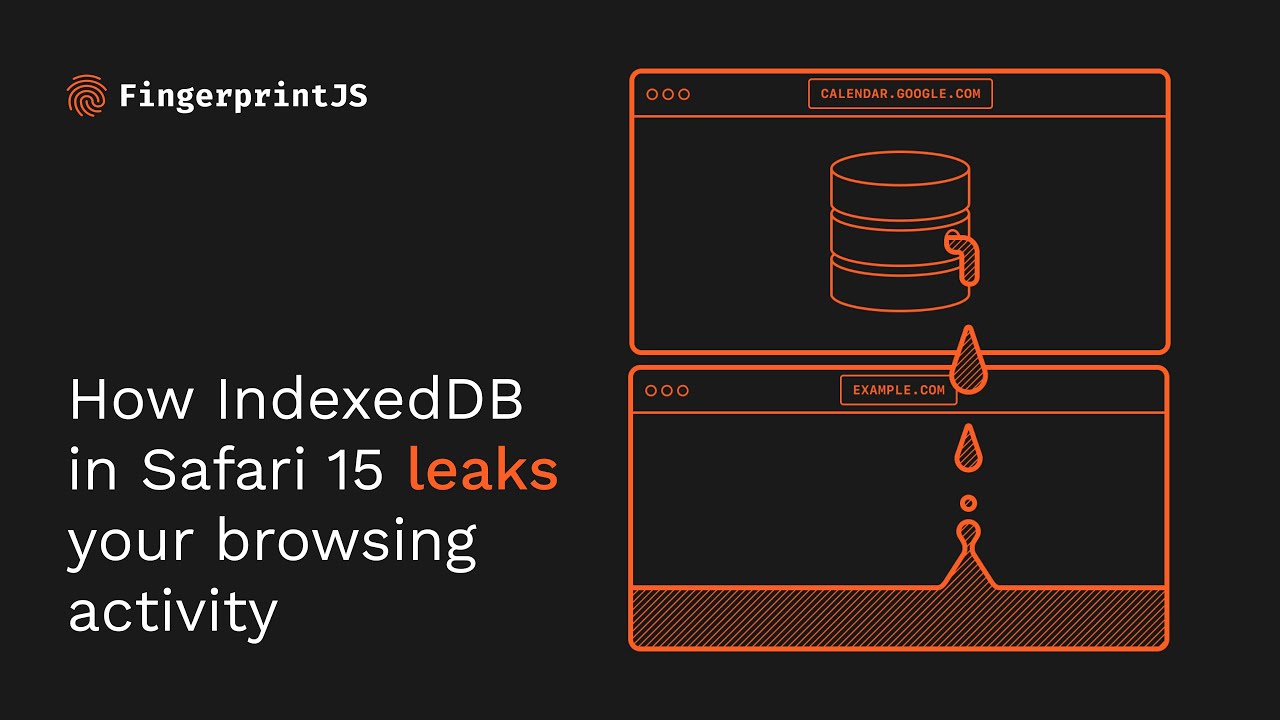
It's all related to the way WebKit implements a JavaScript API called IndexedDB. The bug, which was reported to WebKit on November 28, means that while a website should only be able to see IndexedDB databases it has created, it can actually see those generated by any websites during the user’s browser session.
As these entries are often unique to each website, that means that a site could figure out what other pages you’re visiting in different tabs or windows. "A tab or window that runs in the background and continually queries the IndexedDB API for available databases can learn what other websites a user visits in real-time," the post explains. "Alternatively, websites can open any website in an iframe or popup window in order to trigger an IndexedDB-based leak for that specific site."
As some websites also create user-specific identifiers in the IndexedDB database names, that also means that bad actors could use the exploit to figure out a seemingly anonymous browser’s identity.
In the video below, FingerprintJS uses YouTube as an example. Once logged in, the ID is changed to include a string that, with a little legwork, can be linked to a specific person:
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
IndexedDB databases can be accessed without any user input, the post adds, and enabling Private Browsing mode won’t close the loophole either.
An analysis of Alexa’s top 1,000 most visited pages found that over 30 “interact with indexed databases directly on their homepage, without any additional user interaction or the need to authenticate.”
That doesn’t sound too bad, but FingerprintJS believes that it’s worse than it sounds. “We suspect this number to be significantly higher in real-world scenarios as websites can interact with databases on subpages, after specific user actions, or on authenticated parts of the page,” the post continues.
Until a fix is issued, Mac users can simply switch to another browser, but a similar solution isn’t available for worried iPhone and iPad owners because Apple requires all browsers to use WebKit on its mobile platforms, meaning Chrome and Firefox are also affected.
“One option may be to block all JavaScript by default and only allow it on sites that are trusted,” the blog post explains, but it adds that this makes web browsing “inconvenient.”
“The only real protection is to update your browser or OS once the issue is resolved by Apple,” the post concludes. “In the meantime, we hope this article will raise awareness of this issue.”
Freelance contributor Alan has been writing about tech for over a decade, covering phones, drones and everything in between. Previously Deputy Editor of tech site Alphr, his words are found all over the web and in the occasional magazine too. When not weighing up the pros and cons of the latest smartwatch, you'll probably find him tackling his ever-growing games backlog. Or, more likely, playing Spelunky for the millionth time.