
As we mentioned in our previous piece, phishing is one of the most common vectors through which ransomware spreads. The distribution of malicious software is hardly phishing’s only directive, though. Just as often, it’s a tool through which criminals collect personal information from their victims.
A phishing scam has a simple goal: to trick its victim into taking a course of action that is ultimately harmful to them. Occasionally, this involves downloading malicious software, but it just as often has the victim share something. This could be a sensitive file, an account login, or even something like a social security number or bank number.
Phishing attacks may come through myriad paths, including instant messages, email, text messages, and, occasionally, even Voice over IP (VOIP). On occasion, phishing attempts may be highly-targeted, directed at specific individuals or companies — these are known as spear phishing, or when directed at high-profile targets, whaling. The former is particularly dangerous, as it involves a criminal leveraging personal data to enhance their attack.

The one thing all phishing attacks have in common is a reliance on a combination of social engineering and carelessness to work their magic. A criminal that executes a phishing attack hopes that their target will be either fooled or intimidated to playing along. The cleverest even excel at creating falsified copy and landing pages almost startlingly similar to the real thing.
The good news is that if you know what to look for, you can recognize even exceptionally-convincing phishing attacks. Even the best attacks tend to follow a set pattern, which you can eventually train yourself to identify. As such, a bit of mindfulness and due diligence goes a long way here.

Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Generally, every phishing message starts with a story. This story uses a particular emotion, usually either greed or fear, to trick a target into playing along. Some common tactics include:
The first thing to keep in mind here is that if something seems too good to be true, then it probably is. Very few things in this world are free, and you’re generally not going to receive unsolicited offers, especially from senders you don’t recognize. Similarly, if an email or message seems overly-urgent goes to great lengths to discuss the consequences of inaction, there’s a good chance someone is trying to scam you.
Beyond these obvious flags, there are a few things to look for that can help you quickly identify the lion’s share of phishing attempts.

Not surprisingly, savvy scammers tend to put a lot more effort into their attacks. Their messages are significantly more convincing and rarely contain the kind of errors found in your run-of-the-mill scam. They may compromise or clone an email in your address book in an attempt to fool you.
In some cases, they may even forego messaging altogether, hijacking legitimate web pages, masquerading as legitimate Facebook applications, or otherwise redirecting users to a near-identical forgery of a site’s login page.
In these cases, you need to use your best judgment. If you find a message from a friend or colleague to be even the least bit suspicious, follow up with them on another channel to ask if they sent it. And always take a step back and evaluate your digital surroundings before entering (or re-entering) login data.
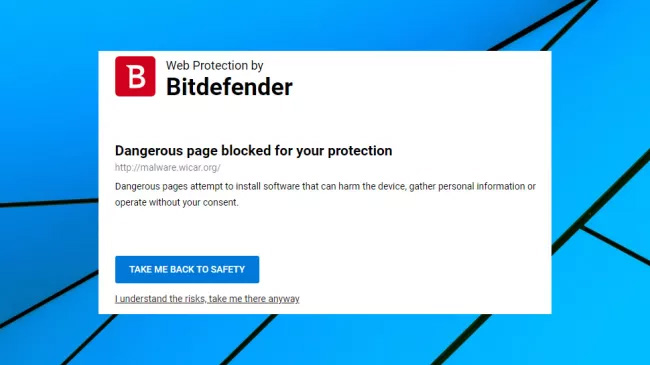
Of course, even the most cautious people occasionally make mistakes. And that’s where Bitdefender Total Security comes in. Recently awarded Product of the Year by independent security software testing agency AV-Comparatives, it offers anti-phishing functionality that intelligently identifies and blocks phishing pages and an anti-fraud system that warns you when you visit a potentially suspicious website.
This is in addition to a host of other features, including multi-layer ransomware protection, complete real-time data protection, and advanced network security. As a platform, it functionally provides everything you need to protect yourself against not just phishing sites, but virtually any threat you may face on the web. Moreover, if you purchase the Bitdefender Family Pack, you can keep your entire household safe, installing the solution on up to 15 devices.
Bitdefender is an incredibly-sophisticated security solution - but it needs to be. Malware is growing more advanced by the day, with new and sophisticated techniques and tactics surfacing on a regular basis. Understanding them is the first step to defending yourself from them.
But that’s a topic for next time.
