New Mimic ransomware can hold your files for hostage fast
This new ransomware strain uses search tool to supercharge

A new ransomware strain is making the rounds online that can encrypt your files even faster than most, as it uses a popular third-party Windows search tool to know exactly what to look for.
First discovered back in June of last year by Trend Micro, this new ransomware strain has been dubbed Mimic based on a string the company’s security researchers found in its binaries. According to a new report, the Mimic ransomware is so far primarily being used to target Russian- and English-speaking users.
Interestingly enough, BleepingComputer points out that some of the code found in Mimic shares similarities with the Conti ransomware. This is likely due to the fact that Conti’s source code was leaked back in March 2022 by a Ukrainian researcher after its creators sided with Russia.
The Mimic ransomware is currently being spread through executable files (.exe) that are sent to targeted victims via email. Once opened, the executable extracts its malicious payload along with tools that are used to disable Windows Defender on a victim’s computer.
Mimic has quite a few tricks up its sleeve to help speed up the process of encrypting a victim’s files .including using multiple processor threats and command line arguments to narrow file targeting.
Everything Windows search tool
What makes Mimic much faster and more efficient than previous ransomware strains is how it uses the “Everything” search tool to locate files to hold hostage. Developed by Voidtools, Everything is a filename search engine for Windows that is much more efficient and faster than Windows Search.
By using Everything on a targeted system, Mimic is able to locate files that can be encrypted, like documents, while avoiding system files that would prevent a computer from turning on in the first place if locked.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
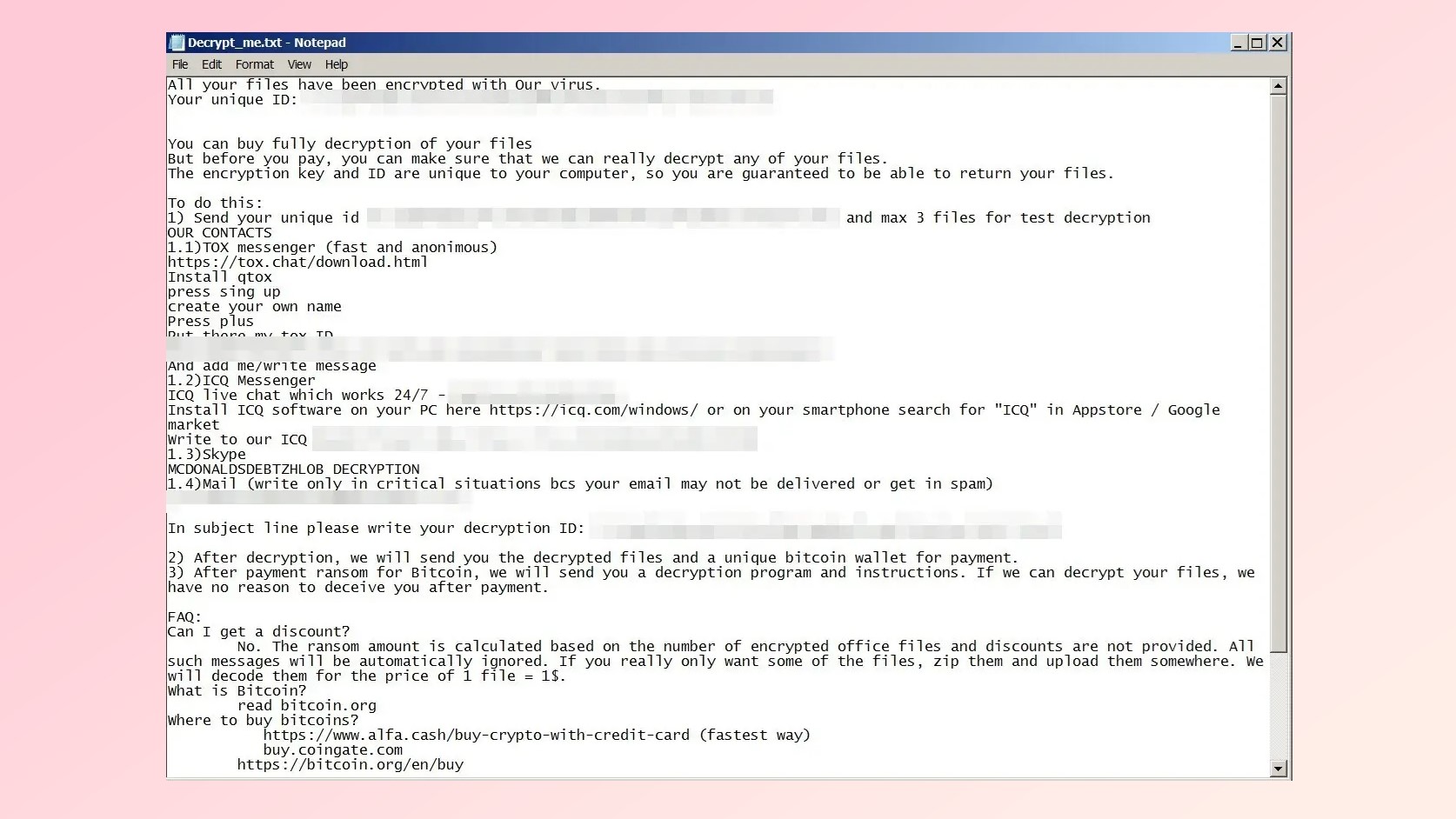
Files encrypted by the Mimic ransomware are given the “.QUIETPLACE” extension and a ransom note named “Decrypt_me.txt” is dropped somewhere on a user’s system. This ransom note explains that victims need to pay the attackers in Bitcoin to have their files unencrypted. However, it also says that the attackers can decrypt just some of a victim’s most important files for the price of “1 file = 1$”. This might be worth it for victims if they only need a few files from their locked system and were planning on upgrading to a new PC anyways.
This is the first time we’ve seen a ransomware strain use a popular third-party tool to speed up the encryption process. The Everything search tool doesn’t even need to be installed on a victim’s machine, as it’s included in the malicious executable used to infect a PC with Mimic in the first place.
How to stay safe from ransomware

Just like with malware and other viruses, you should avoid opening attachments in emails from unknown senders to stay safe from ransomware. Likewise, you shouldn’t download illegal software or download any file from sites without a proven reputation.
The best antivirus software can also detect many types of ransomware before your system is infected. However, antivirus software isn’t able to unlock your files once they’ve been locked by an attacker using ransomware. For this reason, it pays to use the best cloud storage to keep an extra copy of your most important files stored safely in the cloud and the best cloud backup services may be an even better choice as it backs up your files automatically.
If you do fall victim to ransomware, this step-by-step guide can walk you through the process of getting your files back. At the same time, Bitdefender and other cybersecurity firms often release ransomware decryption tools like it did for the Darkside ransomware. This way, even if you don’t have the money or don’t want to pay a ransom to cybercriminals, there’s still a chance you may be able to recover your files someday.
As for the Mimic ransomware, it’s a relatively new strain and we don’t know that much about how it’s being used in attacks or who’s behind it yet. Hopefully we find out more soon.

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
