Malicious Chrome extensions with 1 million downloads can hijack your browser — delete these now
These malicious extensions commit ad fraud and sell your search data

Just like when adding new apps to your smartphone, you need to be careful when adding the best Google Chrome extensions to your browser. Malicious extensions can be used for ad fraud or even to infect your PC or Mac with malware.
As reported by BleepingComputer, a new malvertising or malicious advertising campaign has been discovered by the cybersecurity firm Guardio Labs that uses Chrome extensions to hijack web searches and add affiliate links to any sites you visit.
This malvertising campaign has been dubbed “Dormant Colors” by the firm’s security researchers due to the fact that all of the malicious extensions in question offer color customization options for Chrome. However, the extensions themselves don’t include malicious code when installed, which is how they were able to bypass Google’s security checks and end up on the Chrome Web Store in the first place.
Dormant Colors Chrome extensions
Following its investigation into the matter, Guardio found 30 different versions of these malicious browser extensions on both the Chrome and Edge web stores with more than a million installs combined. As we mentioned before, they have been removed from both web stores but here is the full list just in case:
- Action Colors
- Power Colors
- Nino Colors
- More Styles
- Super Colors
- Mix Colors
- Mega Colors
- Get colors
- What color
- Single Color
- Colors scale
- Style flex
- Background Colors
- More styles
- Change Color
- Dood Colors
- Refresh color
- Imginfo
- WebPage Colors
- Hex colors
- Soft view
- Border colors
- Colors mode
- Xer Colors
How to manually remove Chrome extensions
While all of the malicious extensions listed below have since been removed, you may need to manually remove them from Chrome by clicking on the three dots menu at the top right of your browser. From here, click More and then head to More tools > Extensions. Here you’ll be able to disable the extensions and if you run into any problems, this support document can guide you through the entire process.
Hijacking your browser to earn revenue from clicks
In order to trick unsuspecting users into downloading their malicious extensions, the cybercriminals behind this campaign use advertisements or redirects when you visit sites that play videos or offer downloads.
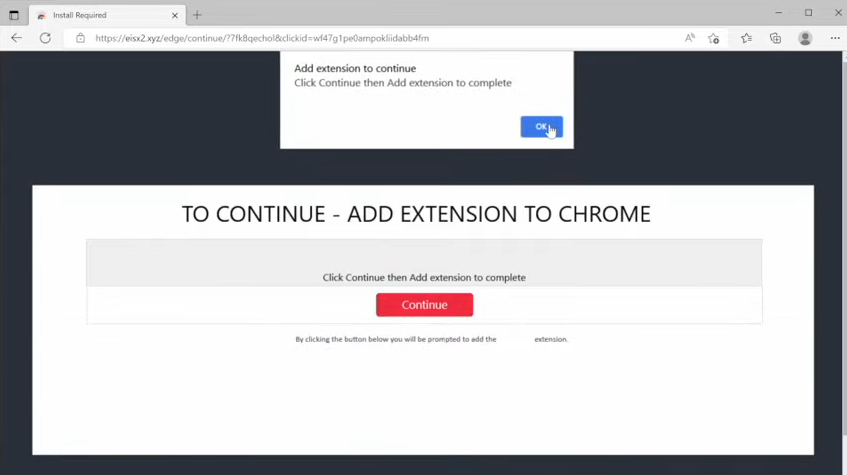
When you try to watch a video or download the program at these sites, you are redirected to another site that says you must add an extension to continue. If you click either ‘OK’ or the ‘Continue’ button, you are prompted to install a color-changing extension that looks harmless at first glance.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Once installed though, these extensions redirect users to pages that side-load malicious scripts that show the extensions how to perform search hijacking but they also tell the extension which sites affiliate links can be inserted on. This generates ad revenue for the creator of these malicious extensions but your search data is also sold for profit.
These Dormant Colors extensions also have a list of 10,000 sites that can be used to automatically redirect users to the same page but with affiliate links added to their URLs. Any purchase made on one of these sites will generate a commission for the extensions’ developers.
In a blog post explaining its findings, Guardio provided further insight on the potential of this malicious extension campaign to expand further, saying:
“This campaign is still up and running, shifting domains, generating new extensions, and re-inventing more color and style-changing functions you can for sure manage without. Adding to that, the code injection technique analyzed here is a vast infrastructure for mitigation and evasion and allows leveraging the campaign to even more malicious activities in the future.”
How to stay safe from malicious browser extensions

If you plan on adding any new extensions to your browser, you should probably have one of the best antivirus software solutions installed on your laptop or PC to protect you from becoming infected with malware or having your data stolen.
Apart from this, you should only use trusted sources like the Chrome Web Store or the Microsoft Edge Add-ons store to install new extensions. While bad extensions do slip through the cracks from time to time, you’re still safer installing browser extensions from an official store than from the web.
At the same time, you should always ask yourself whether or not you really need an extension before installing it. For instance, if an extension seems too good to be true, then it probably is and isn’t worth installing. You also want to periodically go through the list of extensions in your browser and delete any you no longer use while keeping a close eye out for new ones you don’t remember installing.
Browser extensions give you a whole new way of customizing your browser and adding new features to it. However, just like with apps, cybercriminals often create fake extensions for their own gain that are capable of committing ad fraud or even infecting your computer with a virus.

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
