iOS 13.4 flaw may expose user data: How to avoid it
iPhone doesn't send all traffic through VPN, blog post says

A bug in iOS 13.3.1 and later is preventing iPhone users from properly connecting to VPNs, provider ProtonVPN says. However, there's a chance that this may occur only for specific Apple traffic and may be perfectly benign.
The problem seems to arise when an iPhone user connects to a VPN server while already connected to internet services and websites, as most iPhones normally would.
- The best VPN services: Keep your internet connections private
- The best iPhones: Up your Apple game
- New: A wave of AirPods Pro killers is on the way — thanks to Apple's enemy
Even after the VPN service is switched on, ProtonVPN says, some existing connections do not switch to using the VPN, but instead keep using their previous routes.
The risks to the user are that the still-alive connections will let third-party observers see to which IP addresses the user's traffic is going. The VPN connection would normally mask that. Data on any unencrypted connections will also still be visible to network "sniffers," although as ProtonVPN admits, that's rare nowadays.
"Those at highest risk because of this security flaw are people in countries where surveillance and civil rights abuses are common," ProtonVPN says in a blog posting.
How to avoid this issue
The fix for this is easy. ProtonVPN suggests that to avoid this issue, iPhone users should go into Airplane Mode to kill all existing connections, then switch on their VPN service, then leave Airplane Mode to resume connectivity.
We've asked Apple for comment on this issue and will update our story when we receive a reply.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Not a bug, but an Apple feature by design?
However, there's a chance that this is a feature, not a bug. The WireShark screenshot meant to illustrate this phenomenon in the ProtonVPN blog posting shows the issue affecting only traffic to and from Apple servers, which use the entire 17.0.0.0 IP address range.
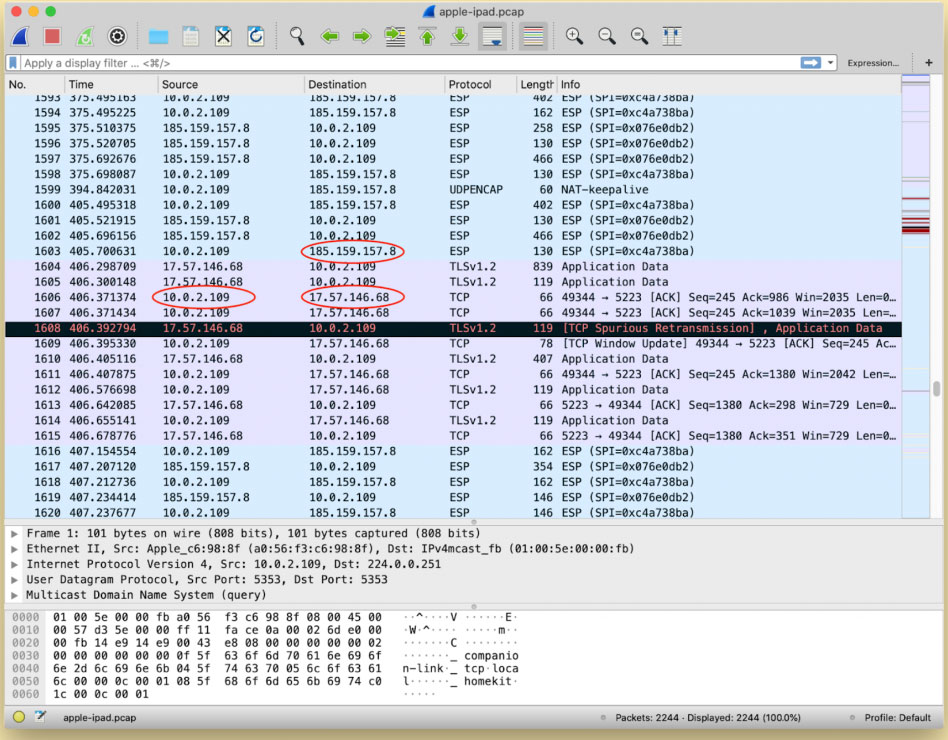
Will Strafach, a well-respected mobile-security expert and creator of the Guardian iOS privacy app, wondered on Twitter yesterday (March 26) whether this behavior might be connected to the Apple Push Notification Service (APNS).
has anyone corroborated this?I think @ProtonVPN may be incorrect in their conclusion. it is entirely possible that I am wrong on this, but my understanding is that connections to APNS do not go through VPN tunnels. https://t.co/cchZ9za9lCMarch 26, 2020
APNS is the Apple-specific protocol used for FaceTime and push notifications, and it does not behave the exactly the same way as regular internet traffic -- but it does use the Apple IP address range. It also appears that Apple goes out of its way to make sure that APNS traffic avoids going through VPNs and proxy services.
One person responding to Strafach's tweet cited an OpenVPN support FAQ that states: "Many Apple services such as Push Notifications and FaceTime are never routed through the VPN tunnel, as per Apple policy."
Another Tweeter pointed to an Apple document that says, "You need a direct, unproxied connection to the APNS servers" to use push notifications or FaceTime.
Nope, still an issue, ProtonVPN says
ProtonVPN said in its blog posting that even though this issue does occur with APNS traffic, "the problem could impact any app or service, such as instant messaging applications or web beacons."
The ProtonVPN Twitter account also replied to Strafach's Twitter query: "We looked into this hypothesis at the time and determined A) This bug isn't specific to APNS (though that is the most common and easiest to reproduce) B) Notifications are delivered through the VPN tunnel, provided the APNS connection is established once the VPN tunnel is set up."
We looked into this hypothesis at the time and determined A) This bug isn't specific to APNS (though that is the most common and easiest to reproduce)B) Notifications are delivered through the VPN tunnel, provided the APNS connection is established once the VPN tunnel is set upMarch 27, 2020
"There is an easy way to test this issue, which is to use the workaround proposed in our article," ProtonVPN added in a second tweet. "If you switch airplane mode on and then turn it back off -- thus killing the APNS long-lasting connection -- the re-established connection will be within the VPN tunnel."
We reponded to ProtonVPN's Twitter posts with a request for WireShark screenshots showing this issue happening with non-Apple servers. Again, we will update this story when we get a response.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
albatross83 First, airplane mode doesn't necessarily disable connections, especially if you're on WiFi. It may then be necessary to explicitly disable WiFi.Reply
Second, if all connections are indeed disabled, iOS won't actually let you connect to a VPN -- it will say "no internet connection." It's possible that enabling a VPN, disabling all connections, and then re-enabling connections would allow the VPN to catch any new (re)connections, but I doubt there's any guarantee in a multithreaded environment.
In short, this is hardly a simple workaround and the issue needs to be addressed by Apple directly ASAP.

