Millions of iPhones, TVs and other devices could go offline Thursday — here's why [updated]
Expiring security standard may cripple internet access

UPDATED to add that some devices were already starting to see connection issues on the evening of Sept. 29, and list of services with issues on Sept. 30.
Old Macs, iPhones, PlayStation 3 and Nintendo 3DS gaming consoles, an unknown number of smart TVs, set-top boxes and other "smart" devices, and even some PlayStation 4s may lose some internet connectivity this week.
That's because a widely used digital certificate used to verify secure internet connections expires on Sept. 30, and millions of older devices won't be able to update to install newer certificates.
- Windows 11: What it means for gamers
- The best Mac antivirus software you can get
- Plus: 10 million Android users hit by money-stealing malware — what to do
As a result, many activities that requires a secure internet connection — from watching Netflix to checking your email to reading regular websites — may not work on older devices.
If this sounds familiar, it's because we got a heads-up back in June 2020 when security researcher and consultant Scott Helme warned of it on his blog. Later in 2020, it was estimated that one-third of all Android phones could be knocked offline.
"You may or may not need to do anything about this," Helme wrote on his blog in an update last week, "but I'm betting a few things will probably break on that day [Sept. 30]."
What you can do to keep your older devices online
Fortunately for those older Android devices, a workaround has been devised to keep them up and running until September 2024 as long as they've got Android 2.3.6 Gingerbread or later. (After 2024, you'll need at least Nougat 7.1.1.)
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
But that doesn't help Macs running macOS 10.12.0 or earlier, iPhones and iPads running iOS 9 or earlier, PlayStation 4 consoles running firmware versions earlier than 5.00 and old PCs running Windows XP with Service Pack 2 or earlier. All are likely to be affected, according to this list of affected devices posted by the digital certificate authority Let's Encrypt.
If you have one of these devices and can upgrade the OS or firmware, do so this week. For example, any PC running Windows XP SP2 can be upgraded to XP SP3, which will fix the issue. Macs need only upgrade to 10.13 High Sierra, and any iPhone 5 or later can install iOS 10. PS4s are already up to version 9.00, released just a few days ago.
PlayStation 3 consoles may or may not be able to be upgraded. Sony released PS3 firmware update 4.88 for the PS3 in June 2021, nearly 15 years after the console was first made available. We don't know what's in the firmware update — Sony just said it brought "additional features, improved usability and enhanced security" — but it's possible it fixes this certificate issue. [Update: Our fully updated PS3 worked just fine on the afternoon of Sept. 30, after the certificate expiration passed.]
If you can't upgrade your Mac, PC or iPhone, then you can install the Firefox web browser to maintain some level of internet access, although standalone apps may not work. Unlike other browsers, Firefox isn't dependent on the device's OS for its security certificates — it brings its own.
As for smart TV, smart refrigerators, smart-home hubs, home Wi-Fi routers and so on, it's hard to tell. Odds are that many devices released before 2017 may be affected, especially if they've never received a firmware update.
So if you can, open up or download the instruction manuals that came with your devices and try to upgrade the firmware or operating system.
What the heck is going on here?
This is complicated, but all those billions of secure internet connections that take place worldwide every second depend on what's generally referred to as a "chain of trust."
When a server — say a website — connects with a client like your PC, each presents digital certificates affirming identity. Because of this, your browser knows that it's connecting to Chase Bank and not some hacker farm in Russia.
But how do you know these digital certificates are valid? Well, certificates depend on public-private key cryptography to prove there's no forgery taking place, but that's another issue. What also matters is that a higher authority affirms if that certificate was indeed issued to Chase Bank. And another authority vouches for that authority, and so on.
Eventually, you reach the end of the line and get to what's called a root certificate. These are the backbone of encrypted web connections. Root certificate issuers have no one higher to vouch for, because it's the ultimate trust authority, and root certificates can be valid for many years.
Okay, so....
But like all certificates, root certificates eventually expire. And one very important one, called DST Root CA X3, expires Sept. 30, 2021. This root certificate is doubly significant because it "cross-signs" or validates another root certificate that's even more widely used and called ISRG Root X1.
ISRG Root X1 is cross-signed because the authority issuing it, Let's Encrypt, was brand-new in 2015 and as such, wasn't widely trusted by browsers and devices. So it got the older, more widely accepted DST Root CA X3 to vouch for it and essentially tell devices that, "if you trust me, you can trust this one too."
Technically speaking, ISRG Root X1 was functioning as an "intermediate" certificate while DST Root CA X3 was acting as the root certificate. For more on all how this works, Let's Encrypt has a handy explainer, and here's a possibly baffling diagram.
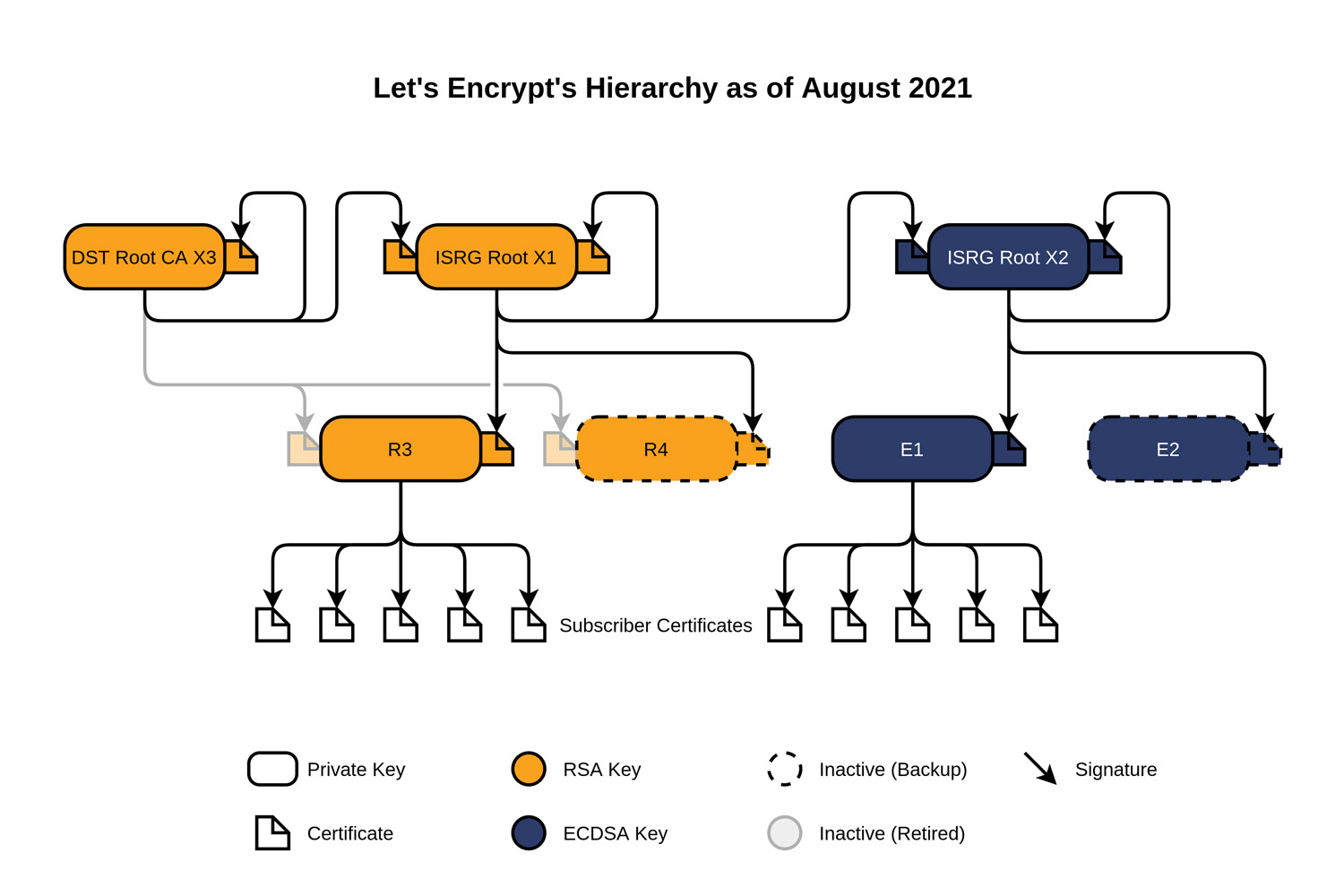
Since 2015, Let's Encrypt has rapidly grown to become the largest certificate authority in the world. One big reason is because it's free to use. Since 2015, most web connections have also become fully encrypted, and Let's Encypt is a big reason for that.
Hence, the very first root certificate Let's Encrypt issued, ISRG Root X1, is very widely used to vouch for thousands, perhaps millions, of shorter-term certificates used by websites and servers.
In fact, until the release of ISRG Root X2 in September 2020, it was the only root certificate Let's Encrypt had issued (and it even cross-signs the newer certificate). Many newer devices have received updates that let them trust the ISRG Root X1 root certificate by itself, which is good because it's valid until June 2035.
But a lot of older devices still rely on the cross-signing root certificate, DST Root CA X3, to vouch for ISRG Root X1. And that's a problem because when DST Root CA X3 expires Sept. 30, 2021, then those devices will no longer trust ISRG Root X1 or the jillions of downstream certificates that depend on it either.
Will I lose all internet connections?
It's hard to say what this will mean for devices that haven't been upgraded to trust ISRG Root X1. There are a couple of hundred valid root certificates in existence, and most devices and web browsers will support at least a few dozen.
So many older devices may still be able to make at least some web connections if those individual server certificates don't lead back to ISRG Root X1 or DST Root CA X3.
However, ISRG Root X1 also backs version 1.02 of OpenSSL, a widely used (because it's free) software library that establishes secure web connections. OpenSSL version 1.02 was issued in early 2015, and a lot of devices and operating systems released in 2015 and 2016 — such as iOS 9 and macOS 10.12 Sierra — rely on it.
Again, we won't really know what's going to happen until it starts to happen on Sept. 30. But Scott Helme thinks something definitely will.
"I don't know what's floating around out there on the web, and I don't know what depends on those things [each certificate] either," Helme wrote on his blog. "One thing that I do know, though, is that at least something, somewhere is going to break."
Update 1: Windows servers may also be affected
On Sept. 21, Helme updated his blog post to note that "I've added IIS to the 'unsure' list as some reports suggest manual intervention is required for a smooth transition."
IIS is Internet Information Services, MIcrosoft's widely used web-server software. Although IIS, which debuted in 1995, gets regular updates and upgrades, some of Helme's Twitter followers pointed out that Windows servers that have been running for many years will continue to use the same certificate "stores" even if they get software updates.
So I actually did a bunch of naive testing on Windows servers (to test if the expiry would be a problem) and found that the answer (for windows) was a resounding maybe. Moving the R3 issued by DST Root CA X3 into untrusted helps force windows to serve the R3 to ISRG X1 chain.September 21, 2021
So an IIS-based server that's been running since, say, 2010, might still have the same certificates it did then, even if it's been updated several times. If so, then it's going to have problems connecting to some client devices (such PCs and smartphones) on Sept. 30.
One poster helpfully posted instructions on GitHub on how to clear out the old certificates.
IIS needs special attention as it will serve the old chain unless you forcefully remove the intermediate R3 cert that’s about to expire as well. Here’s how to do it: https://t.co/Gb3D4qKLxXSeptember 21, 2021
None of this is information that should directly concern the average internet user, but if some of your favorite sites or online services go dark on Sept. 30, this might be why.
Update 2: Some outages occurring already
Helme tweeted on Wednesday evening UK time (Sept. 29) that some outages were already beginning to occur because an older Let's Encrypt intermediate certificate expired about 20 hours before the DST Root CA X3 root certificate that anchored it.
🚨🚨🚨 5 minutes until the Let's Encrypt R3 intermediate expires 🚨🚨🚨29 September 2021 19:21:40 UTCSeptember 29, 2021
Helme said he'd heard that some proxy services run by Blue Coat, Cisco and Palo Alto networks were having trouble connecting.
He had also apparently received "many reports of iOS and macOS versions newer than expected seeing issues on sites serving the expired R3 intermediate. I've seen errors on iOS 11, 13 and 14 along with several macOS version only a few minor releases behind current."
As a couple of other Twitter users predicted a few days ago, Windows servers were indeed having issues, as indicated in the most recent posts on this Let's Encrypt discussion thread.
This story was first posted Sept. 22.
Update 3: Behind-scenes outages
The DST Root CA X3 certificate expired at about 3 p.m. London time, 10 a.m. New York time, on Thursday.
Four hours later, most of the reports of problems are coming from website operators, networking providers and even e-commerce and email providers, including Cloudflare, OVH, Netflify and Fortinet, as chronicled by Helme in a series of threaded tweets.
Bad day for email too, not just the Web. https://t.co/6OoteS4W9zSeptember 30, 2021
Some other issues were reported on the Let's Encrypt discussion forum, especially from some Mac users. Even users of Big Sur reported problems.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
-
Sally G So nobody is able to renew that root certificate? Or corporations don’t want to do so, would rather everyone have to upgrade their devices and appliances?Reply -
PaulWagenseil None of these certificates are designed to last forever. There are three or four levels of certificates, and root certs are the longest-lasting. I believe the one that's expiring soon, DST Root CA X3, dates from 2001, so it's had a 20-year run. Likewise, ISRG Root X1, self-signed or not, was born in 2015 and is good until 2035.Reply -
CJ121 Is this verified information? I contacted Samsung about my 2015 smart tv when I found out my tv can't be updated. They told me this certificate expiration issue has not been verified by Samsung & not to worry about it.Reply -
PaulWagenseil Reply
I'm not sure what you mean by "verified." It's a real issue. The problem is that, as the story says, we don't know exactly which or how many devices will be affected.CJ121 said:Is this verified information? I contacted Samsung about my 2015 smart tv when I found out my tv can't be updated. They told me this certificate expiration issue has not been verified by Samsung & not to worry about it.

