Hackers could crash 5G networks and steal your data — what you need to know
Study finds weak spots in 5G network structure

New research into 5G network architecture has revealed some significant security vulnerabilities that could let attackers crash networks, steal data such as a user's location, and possibly even take over vital network functions.
The flaws are not in the 5G protocol itself, but in the way the 5g architecture distributes different functions to different network "slices" and how those slices interact with older 4G networks.
- The best camera phones right now
- The best Android antivirus apps to keep your phone clean
- PLUS: iPhones under attack via zero-day flaw — what to do now
"We outlined several ways, within the slicing model, how information might potentially be exposed, how services could be misused and how Denial of Service attacks could be executed against network elements," states a new report from Dublin-based AdaptiveMobile Security.
The flaws leave 5G vulnerable to denial-of-service (DoS) attacks and data access misuse between the many network slices that run on any given 5G network, leaving customers’ sensitive information exposed to cybercrime.
One slice for you, another slice for me
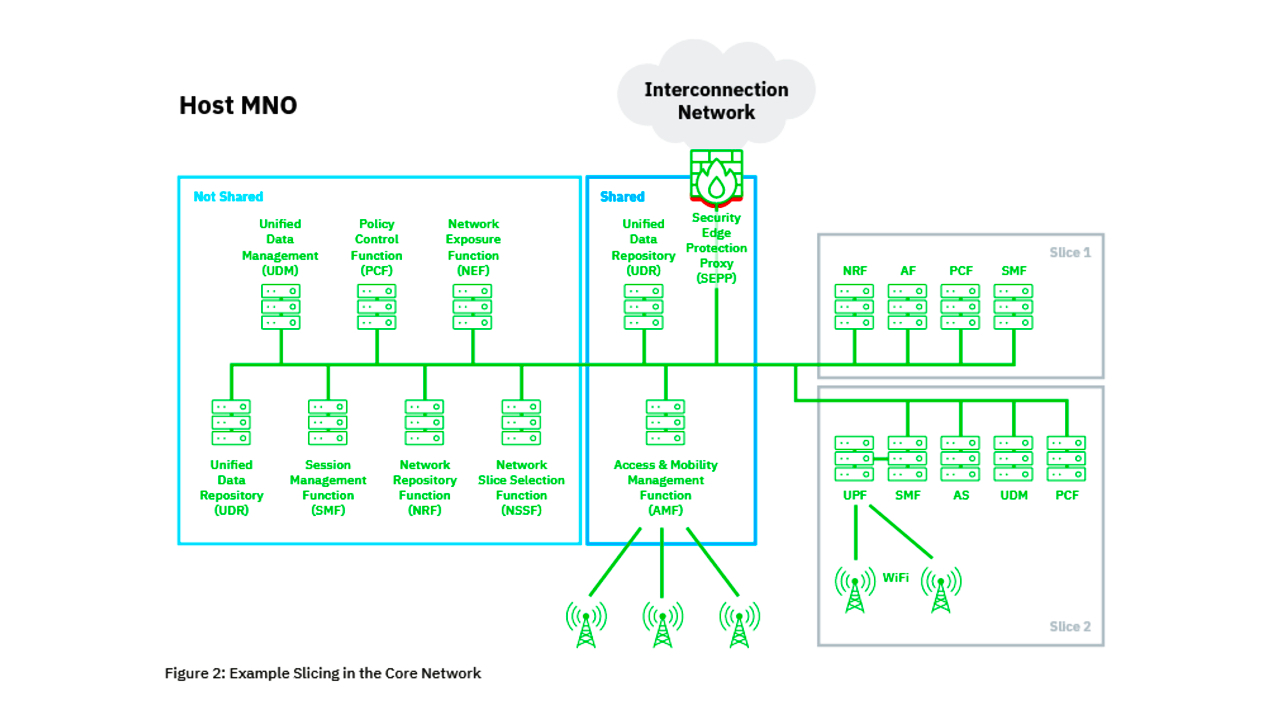
To maximize efficient use of speed, timeliness and bandwidth, core 5G mobile networks can be divided into "slices", separate virtual network blocks with differing characteristics.
Mobile operators can then effectively slice up their resources to provide separate pieces of their core 5G offering to different verticals.
For example, a slice devoted to video streaming could prioritize bandwidth over timeliness or speed; a slice devoted to automotive functions could prioritize timeliness over bandwidth or speed; and a slice devoted to gaming could prioritize all three.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Yet while 5G slicing is safe in theory, all these different slices have got to talk to each other securely. This is complicated by the fact is that many of these slices will be using some 4G technologies during the transition period to 5G, which is expected to last several years.
Network slicing looks set to balloon over the next few years, driving the growth of 5G by enabling the formation of private wireless networks. There’s a lot at stake: 5G network slicing is predicted to generate revenue of anywhere up to $20bn by 2026, according to a study from ABI Research.
Unfortunately, where there's an opportunity, crooks usually aren't too far behind. AdaptiveMobile lifted the hood on the threat to 5G network slicing last month (Feb. 4), sharing its findings with the GSM Association (GSMA).
Despite the threat to 5G remaining low at the moment because of the scarcity of mobile operators with several live network slices on their own networks, AdaptiveMobile has warned that the problem could spiral into significant security risks and wreck mobile operators’ efforts to open up fresh streams of 5G revenue if left unchecked and able to grow alongside the inevitable surge in 5G over the next few years.
The new research underscores 5G core networks that boast both dedicated and shared functions as being vulnerable.
The analysis claims that such "hybrid" traits that support several network slices could spur a disconnect between the application and transport layers’ identities. The resulting mapping failure leaves opportunities for cyber attackers to launch DoS attacks and grab data.
A large-scale threat
AdaptiveMobile Security rigorously tested whether existing 5G standards' security measures can stop an attack in its official whitepaper, uncovering three attack vectors based on the flaws. The answer is no, and the attack scenarios identified can't be prevented with current technology.
The attacks covered exploit the edge network function connected to the mobile operator's infrastructure: an attacker can exploit the mapping weaknesses to give themselves access to operators’ core networks, plus the network slices for different enterprises. To put it lightly, it's worryingly far-reaching.
What I've been up to lately. Having a very close look at the specifications on how network slicing deep down works in a scenario where part of the infra is shared. Using IT for telco is a steep learning curve for all. #5G https://t.co/PkkLFI9tS8March 24, 2021
Silke Holtmanns, AdaptiveMobile Security's head of 5G security research, laid bare the scale of the problem, explaining: “Currently, the impact on real-world applications of this network-slicing attack is only limited by the number of live slices in 5G networks globally".
But that threat will grow as the best 5G phones become cheaper. More affordability means greater adoption and, therefore, a larger set of attack avenues and slices.
Holtmanns is cognizant of this, adding: "We are glad to be working with the mobile network operators and standards communities to highlight these vulnerabilities and promote best practice going forward.”
It's a rather somber tone for such innovative 5G technology, but it's a stark reminder that new technology brings new opportunities to the industry — and with it — new avenues for crooks to prize open your sensitive data and skim away the benefits of these innovative network features before they have a chance to truly bed in.
More: Fleeceware apps bilking iOS and Android users out of millions — what to do
Luke is a Trainee News Writer at T3 and contributor to Tom's Guide, having graduated from the DMU/Channel 4 Journalism School with an MA in Investigative Journalism. Before switching careers, he worked for Mindshare WW. When not indoors messing around with gadgets, he's a disc golf enthusiast, keen jogger, and fond of all things outdoors.