Google kills fake antivirus Android apps caught stealing banking information

Update: A new nasty piece of Android malware called Octo has popped up. It allows hackers to take remote control of your phone and steal your banking information and more.
Six deceptive Android antivirus apps have been caught spreading malware that seeks out and steals banking information.
Cyber security experts Check Point Research found these apps on the on the Google Play Store and discovered that they were distributing malware called Sharkbot. When activated, this malware can steal the banking information and Android user credentials once the app it’s hiding in is installed on an unsuspecting phone.
It performs this pilfering by using fake forms to trick users into providing sensitive data that can then be sent back to a command and control server, where it's exploited at a later date by hackers and cyber criminals.
These apps are; "Antivirus, Super Cleaner," "Alpha Antivirus, Cleaner," "Atom Clean-Booster, Antivirus," "Center Security - Antivirus," and "Powerful Cleaner, Antivirus.”
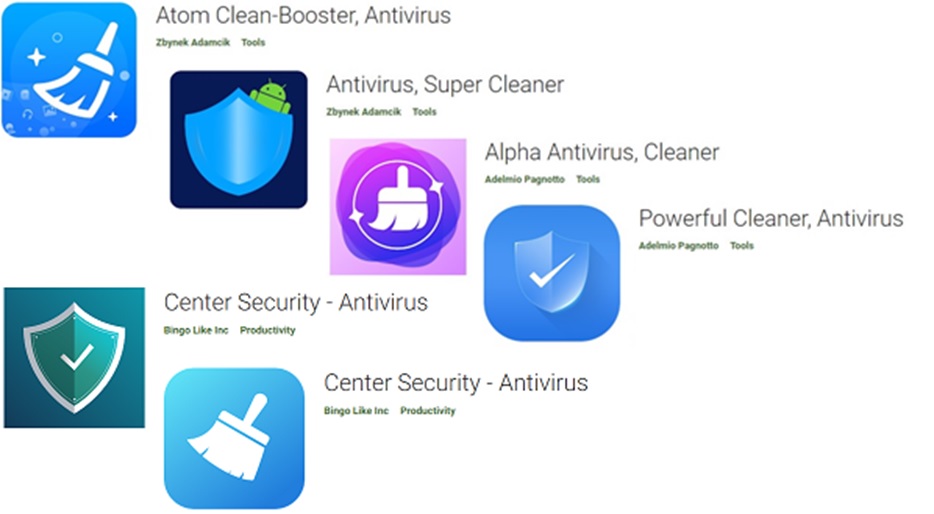
Check Point Research discovered that these deceptive apps have been downloaded and installed around 15,000 times. So this is malware that's been actively exploited.
Google was alerted to the malicious apps, and has since removed them from the Play Store, but it appears that the damage was already done.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
“Despite a fast response from Google, which removed applications linked to threat actor accounts, more attempts were made in Google Play with more droppers from different accounts. They were all subsequently removed as well, but the damage from 15,000 thousand installations was already done,” said Check Point researchers Alex Shamshur and Raman Ladutska.
Intriguingly, Check Point found a geofencing technique was being used in the malware dropper to prevent Sharkbot from targeting users in China, India, Romania, Russia, Ukraine or Belarus. The main targets of the malware spreading were reportedly devices in Italy and the United Kingdom. This approach may have been the reason the malware managed to infiltrate the Google Play Store.
Stay safe from hidden Android malware
Common cyber security advice is to make sure you have an antivirus tool on your smartphone to keep malware at bay. But it’s not always that easy, according to the researchers.
“If a new AV solution appears in Google Play today, there’s no way to guarantee it won’t turn out to be a malware spreading threat tomorrow. This is the exact case we observed with the Sharkbot malware,” said the researchers. “In this spreading scheme, the malware itself is not uploaded to Google Play but rather the intermediate link is, which masquerades as a legitimate software.”
So what can you do to protect yourself from such sneaky cyber attacks? Well Check Point advises that you “install applications only from trusted and verified publishers.” If an app from a new publisher intrigues you, try searching for comparable apps from a trusted developer. Check Point also advices users to report to Google on any suspicious applications they encounter.
And we’d suggest that if you have any reason to doubt the legitimacy of an Android app to avoid it entirely — especially if it requires a side-loading technique.
If you’re unsure about what antivirus tools to trust, then check out our guide on the best antivirus software, which includes both free and paid tools.

Roland Moore-Colyer a Managing Editor at Tom’s Guide with a focus on news, features and opinion articles. He often writes about gaming, phones, laptops and other bits of hardware; he’s also got an interest in cars. When not at his desk Roland can be found wandering around London, often with a look of curiosity on his face.
