Fake Chrome updates infecting PCs with malware — what you need to know
Here’s why you can ignore sites telling you that you need to update Chrome

Keeping your browser up to date can be difficult, especially now that Google updates Chrome every week. However, these more frequent updates also mean hackers have an easier time using fake browser updates to trick unsuspecting users.
According to a new blog post from Proofpoint, four different campaigns are currently using fake browser updates to spread malware. In fact, one hacker group named TA569 has been using them as a lure to deploy the SocGholish malware for the last five years.
Unlike with other malware campaigns which rely on phishing emails to infect users, these ones are carried out directly through your browser and can be initiated by clicking on a link in an email or message, on social media, through fake ads on a search engine or even just by accidentally ending up on a malicious website.
What makes these fake browser update campaigns so effective is their use of social engineering and how they abuse the trust users place in their browser as well as in their most frequently visited sites.
Whether you’re the kind of person that frequently updates your browser or someone who lets these updates lapse, you could easily fall victim to one of these campaigns as they’ve grown more convincing over time. Here’s everything you need to know about fake browser updates as well as how to spot them and what you should do instead.
Hacking websites to spread fake browser updates
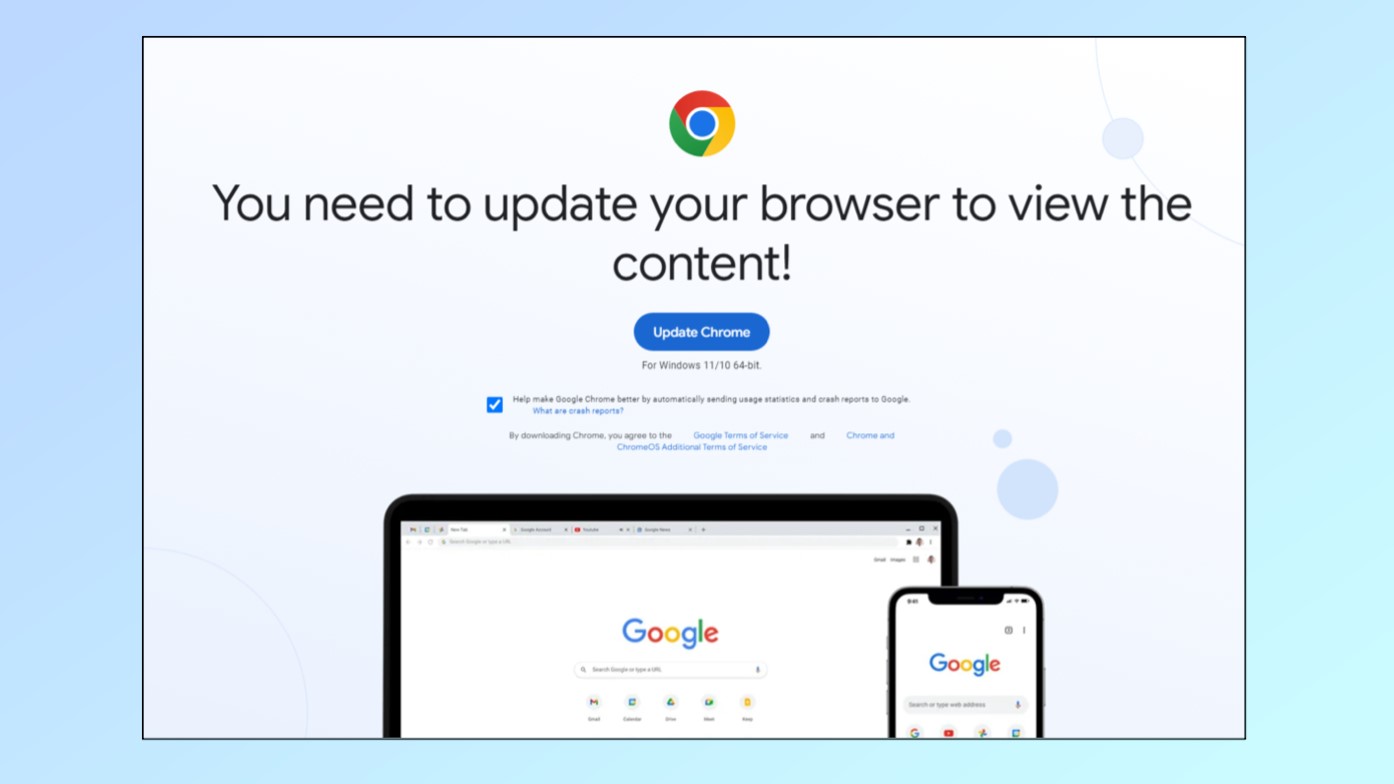
In order to deliver their fake browser updates containing malware, the hackers behind these campaigns first compromise legitimate websites. This way, to the end user, they appear as they normally would but are now actually malicious.
This is done by using JavaScript requests in the background to overwrite the existing site with a browser update lure. From here, when a user navigates to one of these hacked sites, they’ll see a pop-up like the example above telling them that they need to update Chrome since they’re using an old version of the browser.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
According to Proofpoint’s research, there are currently four different campaigns delivering these fake browser update lures to unsuspecting users. While TA569 is using them to deliver the SocGholish malware, there’s also Rogue Raticate (aka FakeSG) and SmartApeSG which deliver a NETSupport remote access trojan (RAT) and ClearFake that’s spreading several different info-stealing malware strains including Lumma, Redline and Raccoon v2.
Having your PC infected with any of these malware strains can lead to your personal data being stolen which can then be used to commit fraud or even to steal your identity. Unfortunately though, as fake browser update pages now look more convincing than ever before, loads of people continue to fall for these lures everyday.
How to stay safe from fake browser updates spreading malware

If you’re wondering what you can do to avoid being conned by one of these fake browser updates yourself, here’s the main thing you need to know. Whether you’re using Chrome, Edge or Firefox (all of the browsers targeted in these campaigns), none of them will show you a page saying your browser is out of date. Instead, you should head to your browser’s settings menu and check for updates manually if you’re worried you're not running the latest software.
Google Chrome also uses a color-coded update system to let you know when new browser updates are available. If you look in the upper right corner of your browser, a bubble will appear next to your profile picture that says “Update”. Green indicates that an update was released two days ago, orange shows it was released four days ago and red means that the update was released more than a week ago.
In a statement to Tom's Guide, a Google spokesperson provided further insight on how Chrome's update system works, saying:
"To make sure you’re protected by the latest security updates, Chrome regularly loads new versions in the background, and the browser updates when you close and reopen your computer's browser. But if you haven't closed your browser in a while, you might see an "update now" chip in the upper-right of Chrome. Users should make sure they are only updating Chrome via the official Chrome toolbar. As a security practice, users should ensure they keep Chrome updated. Google Safe Browsing also helps keep users safe by showing warnings when they attempt to navigate to dangerous sites or download dangerous files."
For additional protection from the kinds of malware delivered through fake browser updates like the ones described above, you should also be using the best antivirus software on your PC and the best Mac antivirus software on your Mac.
Now that most of our work is done via our web browsers, hackers will likely continue to use fake updates as a means of spreading malware, just like they do with malicious apps on our smartphones.
More from Tom's Guide

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
