Linksys, D-Link routers hacked to spread coronavirus malware: What to do now (UPDATED)
Check your router admin password now

UPDATED April 15 to note that Linksys has reset all passwords to its users' Smart Wi-Fi remote-access accounts. More below. This story was originally published March 27.
If you've got a Linksys or D-Link home Wi-Fi router, check right now to make sure its administrative password is strong and unique -- and that the router isn't still using the default admin password it shipped from the factory with.
That's because criminal hackers are "brute-forcing" router admin passwords over the internet so that they can change the router DNS settings to attack your devices with coronavirus-themed malware, according to researchers at Bitdefender and users of the Bleeping Computer forum.
- The best Wi-Fi routers: Keep your home network's signal strong
- The one router setting everyone should change (but no one does)
- New: Alexa can now screen you for coronavirus: How to use it
Your internet traffic will then be re-routed to scam coronavirus-related websites that will try to infect your Windows computer with information-stealing malware that will try to steal your passwords, credit-card numbers, session cookies and cryptocurrency.
- Setting up a virtual router is the perfect way to share your connections
How to protect yourself from this attack
To protect yourself, the first thing you need to do is to change your router's admin password to something unique and strong and then restart the router.
Check your router's DNS settings for manual entries "109.234.35.230" and "94.103.82.249". If those numbers (in fact, IP addresses) are present, clear them, restart the router and the restart any device at home that connects to the internet through the router.
Don't let your browser save credit-card numbers, or any important passwords -- it's too easy to hack. Use one of the best password managers instead.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
If you have one of the best antivirus programs installed, it will likely detect the Windows malware downloaded from this campaign. But antivirus software can't fix your router settings -- only you can do that.
- A router VPN is the best way to secure your Wi-Fi at home
How the attack works
DNS is sort of the internet's phone book -- it matches the website address (URL) you type into your computer, such as "www.foobar.com", to the REAL network Internet Protocol (IP) address, which is a series of numbers that might look something like "188.225.172.30". (I made that one up and it doesn't go anywhere.)
But if hackers corrupt your router, they can change the DNS settings so that "foobar.com" points to an entirely different IP address. When that happens, you might think you're going to the real "foobar.com" -- and the address bar in your browser will say so -- but you'll actually be on an entirely different website.
That's what's happening here. The hackers are redirecting traffic intended for Amazon, Disney, Cox, Reddit, the University of Washington, the University of Florida and half a dozen other websites, Bitdefender reports, to a website that immediately pops up a message window.
Bleeping Computer thinks the situation is even worse -- it has evidence that the corrupted DNS settings hijack a built-in Windows function that periodically checks internet connectivity, with the result that almost any website will pop up the hackers' message.
The message pretends to be from the World Health Organization and urging you to download and install an application that will give you "the latest information and instructions about coronavirus (COVID-19)".
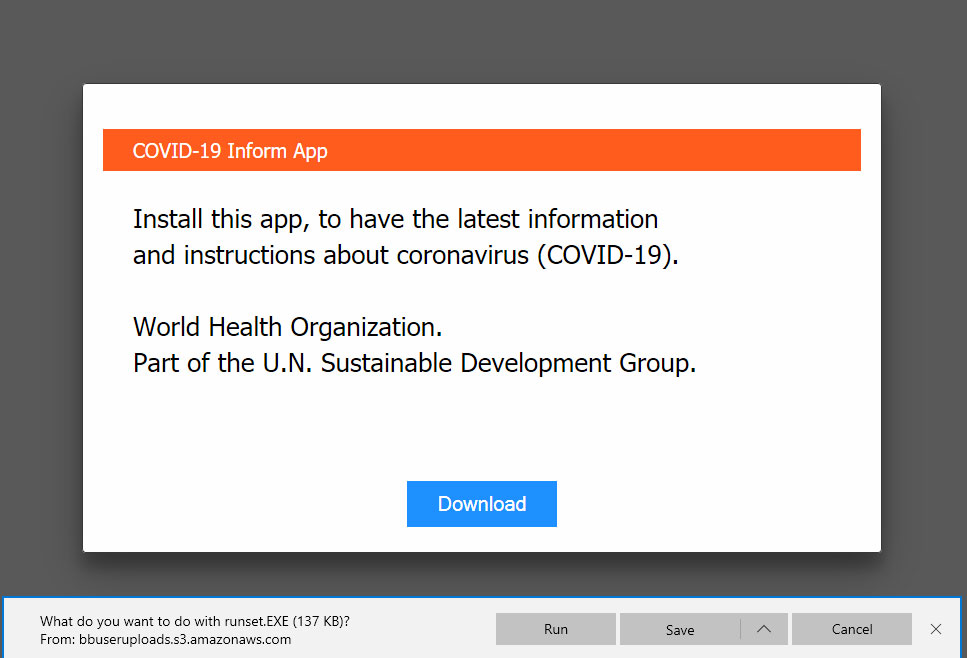
Don't do it. The application is actually the Oski information-stealing Trojan, a fairly new piece of information-stealing malware.
D-Link and Linksys routers seem to be targeted because many of those brands' home Wi-Fi routers ship with a remote-access function enabled by default. Turn that function off -- if it's left enabled, then the only thing protecting a router from remote attack is the strength of its admin password.
UPDATE: Linksys resets remote-account passwords
Linksys told The Register April 15 that it locked all Linksys Smart Wi-Fi accounts on April 2, then later forced a password reset on those accounts.
Linksys Smart Wi-Fi lets you "access your home network from anywhere, at any time, even from your mobile device."
Honestly, that's a really bad idea, and Linksys should have anticipated that thousands of its users would just use the same usernames and passwords for Smart Wi-Fi that they used for other accounts.
The unsurprising result: A wave of credential-stuffing attacks on Linksys routers based on credentials stolen in other companies' data breaches.
"The majority of authentication requests [in these attacks] contained usernames that have never registered on our system," Linksys spokeswoman Jen Wei Warren told The Register. ""Multiple attempts were made using the same username but different passwords, which would not be necessary if our own systems were compromised."
As we stated earlier, if you have remote access enabled on your D-Link or Linksys home Wi-Fi router, turn the access off. The risks it creates far outweigh the convenience.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

