This 'browser in browser' attack will steal your passwords — here's how to avoid it
Perfect-looking pop-up phishing scam

There's a new way to steal your passwords and other vital information, and it's so well done that most people would fall for it.
A pseudonymous hacker called "mr.d0x" last week put up a blog post detailing a very good "browser in the browser" attack in which an attacker creates a fake pop-up login window within a web page.
The "window" isn't really a pop-up, but instead part of the underlying web page. However, mr.d0x has rigged it so that you can actually "grab" the pop-up window and move it around by clicking the title bar with your mouse cursor.

That's pretty convincing, even though you might not be able to resize the fake window or scroll through it, and you definitely wouldn't be able to drag it past the edge of the underlying web page's window.
Nonetheless, most people will be fooled. The fake pop-up can mimic an Apple, Facebook, Google or Microsoft login page perfectly, right down to an icon in the title bar and a URL in the address bar.
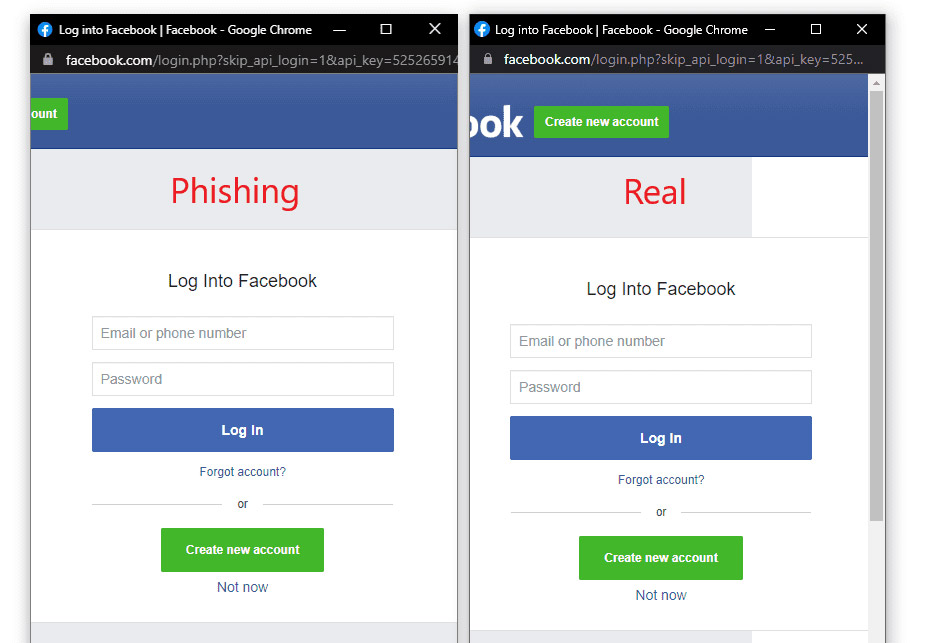
How to avoid being fooled by a fake pop-up window
To avoid falling for this new attack, your best defense is to use one of the best password managers, which won't be fooled by a fake website.
As mentioned above, if you're using a desktop browser, you can also try to resize or scroll the pop-up window, though it's possible that good JavaScript could replicate those actions.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
If so, try dragging the pop-up window past the edge of the main browser window. If the pop-up doesn't respond correctly, then it's fake. But that may be hard to do on a mobile browser.
Perfect pop-ups
Fake pop-up attacks have been tried before, but they've generally looked terrible — not so mr.d0x's. This new attack takes advantage of that fact that so many websites use "single sign on" (SSO) services, whereby you can log into a website with a third-party username and password instead of having to create yet another account and password.
Apple, Facebook, Google, Microsoft and others provide SSO services for thousands of consumer-facing websites. Many companies and other large organizations use internal SSO systems to log into business-related sites and services.
Using SSO logins greatly cuts down on the number of login pages you need to fake. It also makes the passwords that you capture much more valuable. If you're a criminal, you can do a lot more with someone's password for Facebook than you can with a password to the website for Billy Bob's Bar and Restaurant Supply.
"Replicating the entire window design using basic HTML/CSS is quite simple," wrote mr.d0x in last week's blog post. "Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and it's basically indistinguishable."
Anyone can do this — including the bad guys
To that end, mr.d0x has created easy-to-use templates that mimic SSO pages on Google Chrome on both Mac and Windows, and in both light and dark mode. If you'd like to try your hand at it, the templates are up on GitHub.
Now why, you may ask, would someone make such potent weapons freely available? According to the online bio provided, mr.d0x is a penetration tester, someone who is paid to test companies' security systems by breaking into them.
These "browser in the browser" templates are tremendously useful to pen testers, even if they may give website administrators conniptions.
Unfortunately for the rest of us, mr.d0x has just created a very effective way to phish someone's Apple, Facebook, Google or Microsoft passwords. (You should also watch for this password-stealing Android app.)
All a crook has to do is use the template and create a phishing page, both of which are easy to do, and then lure people in with malicious emails, text messages or social-media posts.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

