Critical Android flaw can be used to hack almost any phone: What to do
Strandhogg 2.0 vulnerability lets you spoof any legitimate app

If your Android phone can install Google's May security update, make sure you run the update.
A critical vulnerability called Strandhogg 2.0 revealed yesterday (May 26) can be used to "gain access to private SMS messages and photos, steal victims' login credentials, track GPS movements, make and/or record phone conversations and spy through a phone's camera and microphone," according to the flaw's finders at Norwegian app-security firm Promon.
- The best Android antivirus apps to keep your smartphone safe
- Best Android phones of this year so far
- Latest: OnePlus Z could soon battle Google Pixel 4a
Strandhogg 2.0 superficially resembles the earlier Strandhogg Android flaw that Promon disclosed in December 2019. Both Strandhoggs (the name comes from a Viking term for beach raids) let malware spoof legitimate Android apps and system screens.
As a result, you might type your Facebook username and password into a fake Facebook app rather than the real thing, handing control of your Facebook account over to attackers (unless you have two-factor authentication activated). Or you could give an attacking app permission to use your camera and microphone, letting it spy on you.
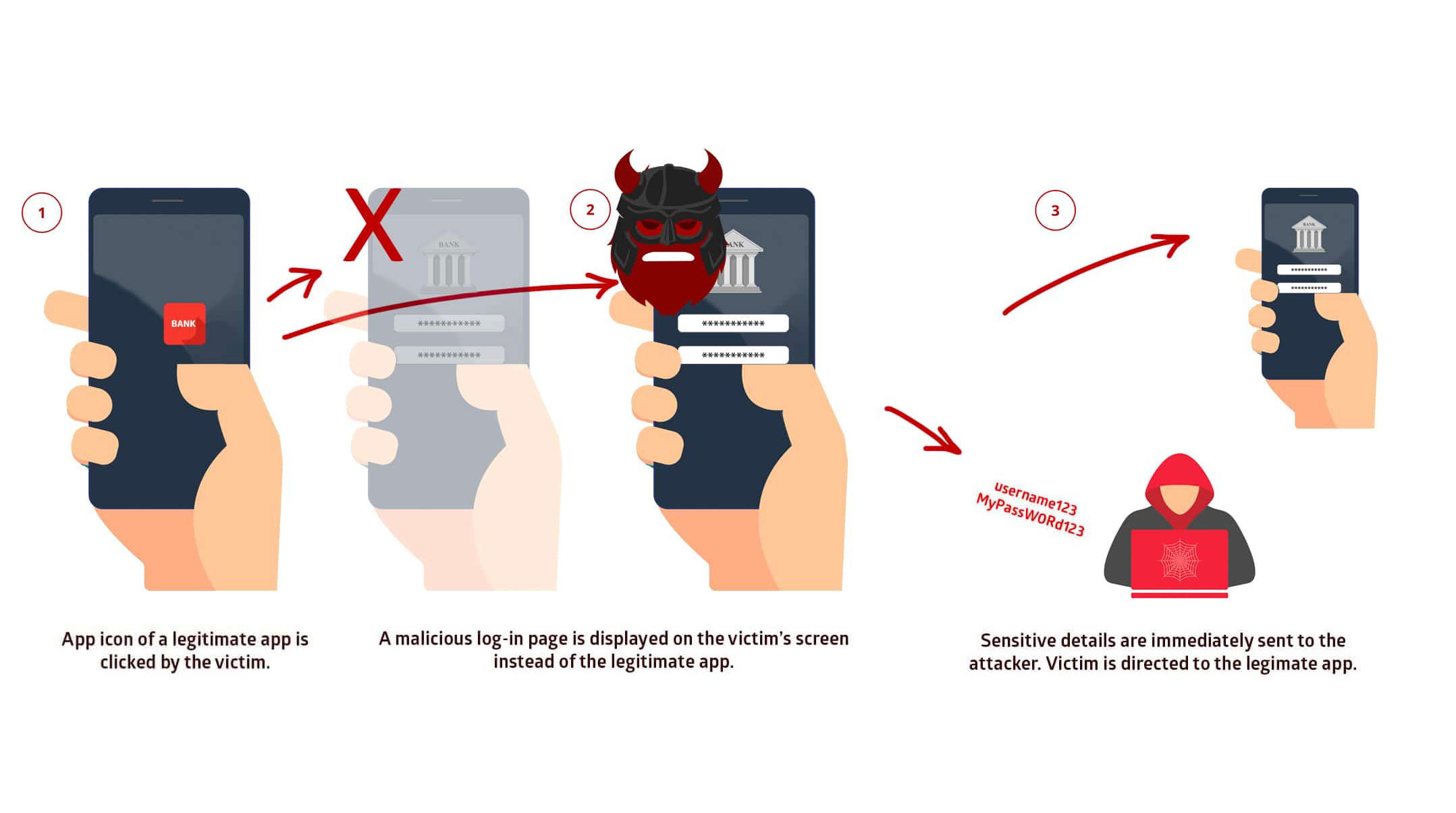
Who is (and isn't) vulnerable to Strandhogg 2.0
The good news is that Android 10 phones are immune from Strandhogg 2.0, and that Android 8.0 and 8.1 Oreo and Android 9 Pie were patched with security updates at the beginning of May. The flaw has also not yet been exploited in the wild, although that may change soon.
The bad news is that many phones that aren't Google Pixels or Samsung flagships will not get the May security patch for several months. Older phones running earlier versions of Android will probably never be patched.
Both versions of Strandhogg can be abused without taking any app permissions, so there would be very little to tip off the phone user that something might be amiss. However, the first Strandhogg is easy to detect using Google's own Play Protect software.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Not so with Strandhogg 2.0. Malware exploiting it might sail past even the best Android antivirus apps. Perfectly innocuous apps might later be updated to exploit Strandhogg 2.0, fooling Google Play.
Promon researchers notified Google of the Strandhogg 2.0 flaw on Dec. 4, 2019, and Google confirmed the severity of the flaw five days later. However, it took Google nearly five months to fix the vulnerability, and Promon cut Google a break by extending its 90-day disclosure deadline by an extra month twice.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.

