3 ways scammers are trying to trick you on social media
Social media is low-effort and high return for scammers

Social media platforms like Facebook, Instagram, TikTok and Twitter have made it much easier to interact with friends and co-workers but they’ve also made things much easier for scammers looking for their next target.
After analyzing data from a full year of attacks on social media, Norton Labs has released a new report highlighting the top phishing lures used to take over user accounts and steal funds from unsuspecting users.
Head of technology at NortonLifeLock, Darren Shou provided further details in a press release on why social media is frequently used by scammers to reach their victims, saying:
"Threat actors use social media for phishing attacks because it's a low-effort and high return way to target billions of people around the world. As social media is intertwined in our daily lives, it's key to know how to spot the signs of a scam, and keep a sharp eye on where requests for your information are coming from. Even better, consider strong, multi-layered security that can be on the lookout for you."
The most common tactic scammers use to steal your login details involves creating fake websites that have a similar name and appearance to official social media login pages. According to Norton Labs, this template is used to fool users into believing a page is legitimate and after entering their credentials, scammers can then access their profile to send spam or launch additional attacks.
Locked account and copyright violation notices
For heavy social media users, nothing can be worse than finding out they no longer have access to their accounts. This is why scammers often send out locked account notices to steal their credentials.
These kinds of phishing lures scare users into revealing their sensitive personal information to scammers by warning them about a fake unauthorized new login, outdated information that must be updated or the need to complete a security checklist to help keep their account secure.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.

Likewise, copyright violation notices are also used to trick people into handing over their usernames and passwords to scammers. These attacks begin with a warning saying that a user has posted copyrighted material and they are then told to log in to unlock their profile. However, they didn’t actually infringe on anyone’s copyright and now the scammers have full access to their account.
Verified badge scams and profile hacking services
Having a verified badge on your Twitter or other social media accounts is something that many users want as it shows their legitimacy on a particular platform. However, many phishing campaigns use the promise of getting a verified badge to lure users into providing their login details. In addition to not actually getting verified, victims could end up losing the social media accounts they value so much.
Although they are a more recent phishing attack variant, profile hacking services have become increasingly popular among social media users looking for information they normally wouldn't be able to access. Instead of stealing user credentials though, these attacks continuously redirect victims to other services like ads or surveys which the scammers use to make money.
Follower generator services and 2FA interception
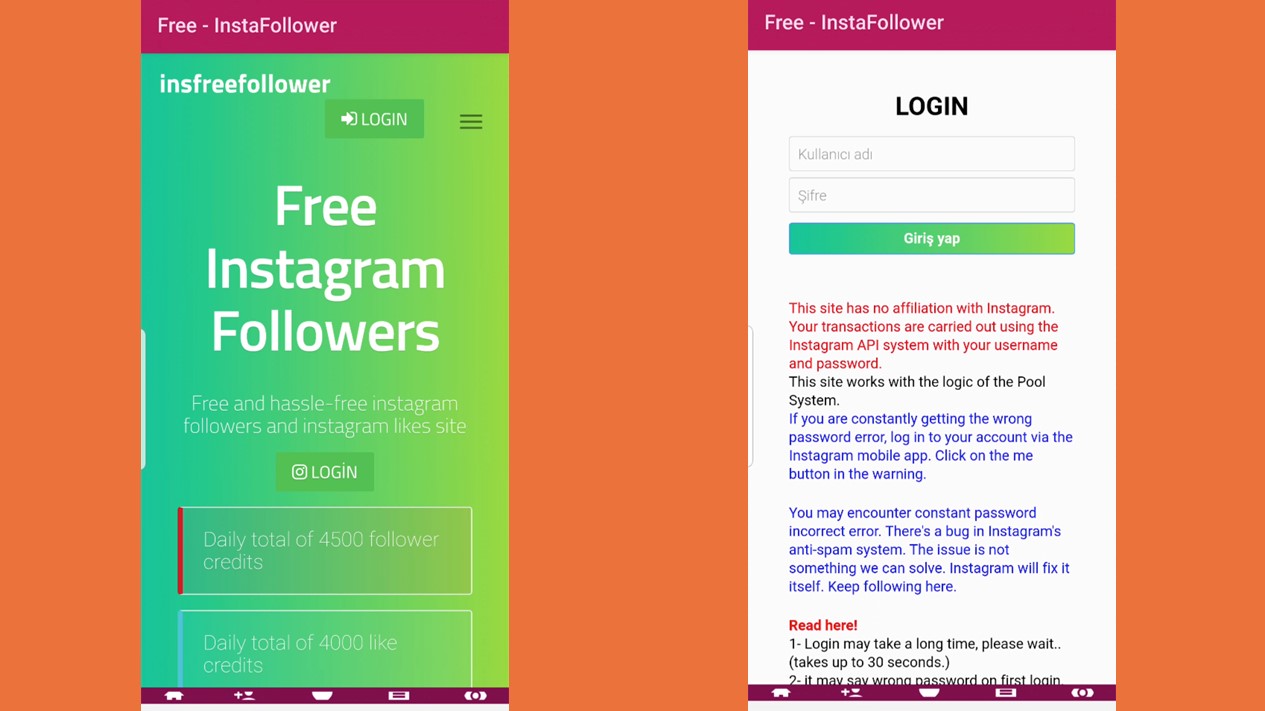
As having a high number of followers is coveted on social media, follow generator services prey on users that want to boost their social media presence.
Scammers often advertise or promote services that can boost a user’s followers at a low cost or for free. These attacks can generate income for scammers by redirecting victims to other attacker-controlled sites that show ads, lure users to reveal their login credentials or infect their devices with malware.
Due to the number of online scams on social media, many people have begun using two-factor authentication (2FA) to protect their accounts. However, scammers and cybercriminals have discovered how to intercept 2FA codes from apps or text messages and then use them to break into victim’s profiles.
How to spot a scam on social media

When it comes to online scams on social media, knowing is half the battle, which is why the FTC has put out a series of tips on how to spot them.
First off, scammers often pretend to be from an organization you know like the IRS or tech giants including Microsoft, Facebook, Google and others. In fact, according to a new blog post from the cybersecurity firm Vade, Microsoft was the most impersonated brand in phishing attacks during the first half of this year followed by Facebook, WhatsApp and PayPal.
In their phishing emails or messages, scammers often say there’s a problem that needs to be fixed or a prize you can claim. This creates a sense of urgency that could compel some users to respond even though deep down, they know it’s likely a scam.
Another thing to look out for is scammers telling you to pay in a specific way. For instance, they may insist you pay using gift cards or with a particular cryptocurrency.
These tips can certainly help but regardless of which social media platform you’re on, you should always avoid responding to messages from unknown senders, just like in your inbox.

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
