Post-quantum VPNs – necessary now or a premature move?
There's no doubt we need it, but when?

Protecting our data is what VPNs do best. They encrypt our internet traffic and personal information, hiding it from prying eyes, third-parties, and hackers.
But what happens when computers get so advanced they can break not just the encryption of the best VPNs, but the entire internet?
This has been dubbed "Q-Day," and marks the moment quantum computers will make all existing encryption methods obsolete.
Don't panic, we're not there yet – experts predict it could be at least another 10 years – but post-quantum encryption (PQE) is already being worked on and implemented.
Many leading VPNs are actively working on PQE and some have already rolled it out. Are they moving too early? Or should every VPN adopt PQE as soon as possible? It's certainly an interesting debate, and one that doesn't have a straightforward answer.
What we do know is that every VPN should use PQE – it's just a matter of when.
Standardization of Post-Quantum Encryption
In August 2024, the U.S. National Institute of Standards and Technology (NIST) released its first three finalized PQE standards. NIST is an agency of the U.S. Department of Commerce, and it has spent years testing different methods – with three industry standards emerging.
These are:
- Module-Lattice-Based Key-Encapsulation Mechanism Standard (ML-KEM)
- Module-Lattice-Based Digital Signature Standard (ML-DSA)
- Stateless Hash-Based Digital Signature Standard (SLH-DSA)
NIST Mathematician Dustin Moody called these the "main event." He warned "full integration will take time" but "there is no need to wait for future standards."

The U.S. National Security Agency (NSA) also released a set of cryptographic standards. In September 2022, it announced its Commercial National Security Algorithm Suite 2.0 (CNSA 2.0), sharing its first recommendations for PQE algorithms.
These recommendations include the two ML-based encryption algorithms as well as Secure Hash Algorithms (SHA), the Leighton-Micali Signature (LMS), and the Xtended Merkle Signature Scheme (XMSS).
The UK's National Cyber Security Centre cites the latter two as effective PQE algorithms but "can only be used in a subset of use cases" and are "not suitable for general purposes."
The issue around implementation
If PQE implementation is being encouraged, why are most VPN providers waiting? There's still some industry debate over the most effective form of PQE, but the issue for VPNs surrounds implementation.
Firstly, it isn't simple. Post-quantum cryptography is complex and because of what it protects against, requires careful attention. PQE has to run alongside existing VPN protocols or new ones have to be created.
However, WireGuard, the most popular VPN protocol, isn't fully quantum secure. WireGuard discloses this limitation and recommends running "a truly post-quantum handshake on top of WireGuard" to achieve full post-quantum security.
Some providers have the resources to invest in this task, but others don't. This could be why we're not seeing widespread adoption of PQE.

Secondly, PQE resistance can't be truly tested yet because quantum computers simply aren't readily available.
Whilst rigorous testing has already been done and there is a high level of confidence in PQE methods, they haven't been battle-hardened on the front line. We won't know with 100% certainty the effectiveness of PQE for perhaps a decade.
It's possible VPNs don't want to go all in on one solution only to find it is ultimately insecure. VPNs pride themselves on securing the privacy of their users and will want to guarantee this.
VPNs & Post-Quantum Encryption
Who has implemented PQE?
The number of VPNs implementing PQE is small, and the number of who have implemented it across the board is even smaller.
ExpressVPN and Mullvad are two VPNs who offer PQE across all apps. ExpressVPN integrated ML-KEM into its Lightway protocol back in January 2025.
Lightway is a unique protocol developed in-house by ExpressVPN, and this could explain how it has been able to implement PQE quicker than most other VPNs.
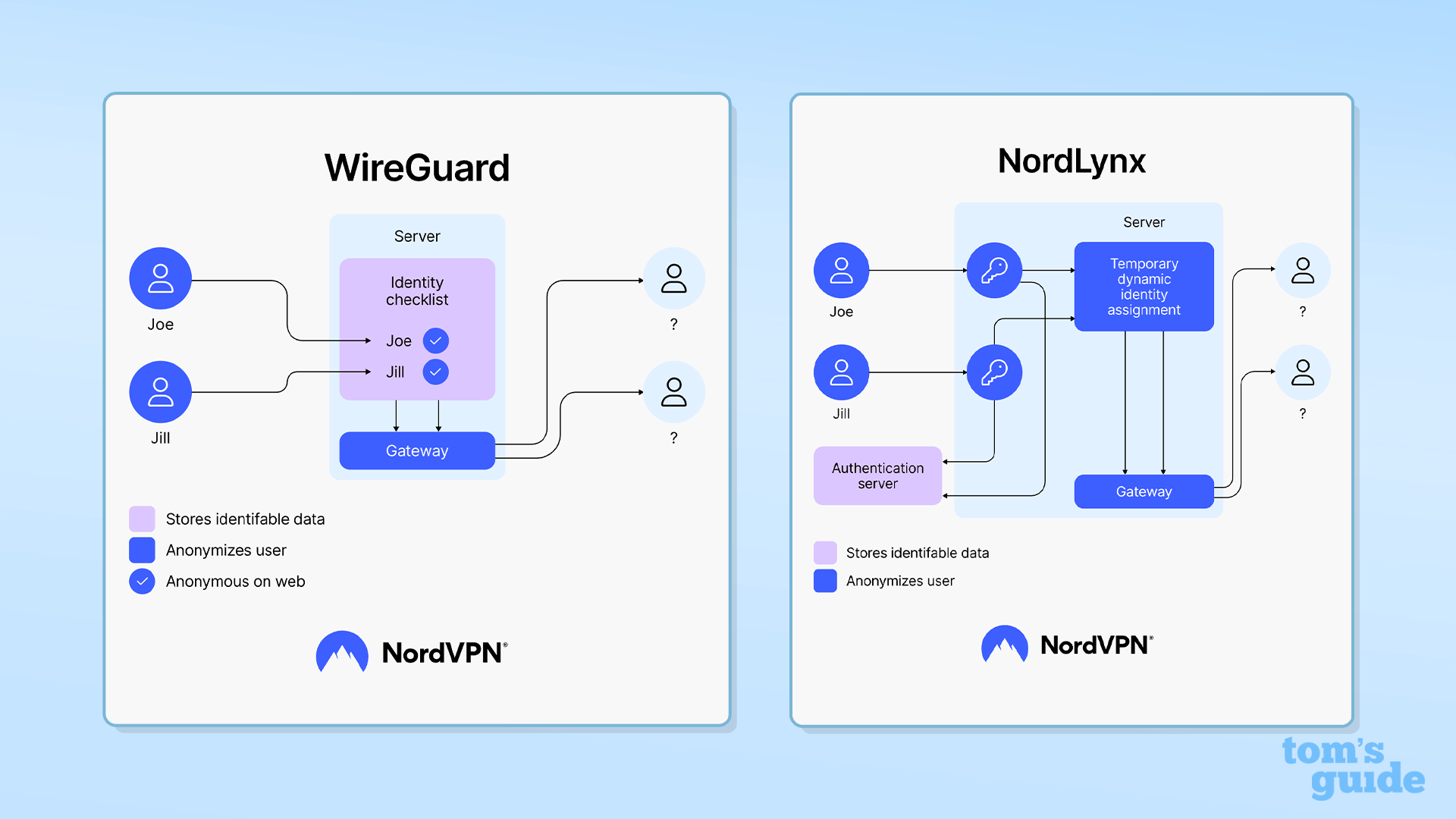
NordVPN has also introduced its own protocol, known as NordLynx. This protocol utilises the foundations and structure of WireGuard, but NordVPN has made changes to ensure it's quantum-secure.
The protocol is available on all desktop and mobile platforms, as well as tvOS, and Android TV.
Due to the technicality of PQE, NordLynx can't be used with NordVPN's Meshnet, Obfuscated servers, and Dedicated IP features or its OpenVPN protocol.
Mullvad began its PQE strategy back in 2017, implementing protections on Linux. iOS support was introduced in August 2024, marking the final app to receive PQE protection.
Mullvad also utilises ML-KEM in what it describes as "Quantum Resistant Tunnels." Its approach sees post-quantum secure key encapsulation mechanisms sharing a key with WireGuard through its pre-shared key option.
This compensates for WireGuard's post-quantum weaknesses and protects users from "harvest now, decrypt later" attacks – where hackers steal your data now, with the aim of decrypting it in the future.
PureVPN and Windscribe are two other providers who have implemented elements of PQE.

Who hasn't implemented PQE?
Surfshark and Proton VPN are two leading providers who are yet to implement PQE of any kind.
Surfshark said it is "actively implementing PQE now." Adding that its "priority is to take the necessary time to ensure everything is implemented flawlessly."
Similarly, David Peterson, General Manager of Proton VPN, said "we're preparing to protect users from these threats, but they are still some way off. Developing post-quantum encrypted technologies is a marathon, not a sprint, and we want to prepare properly so that these technologies only need to be deployed once across the whole Proton ecosystem. Importantly too, we need to battle-test these quantum-resistant algorithms, and to make sure they are standardised."
IPVanish is working on PQE implementation and is planning on a 2025 release, with methods currently being tested.
VPN newcomers Obscura VPN and NymVPN cited concerns with "conflicting guidance" and "disagreements" over algorithms and security levels. Both are working on implementing PQE, but will not rush it. However, NymVPN CEO Harry Halpin said it would be coming in 2025.
To PQE or not to PQE?
Clearly there are a number of differing views on implementing post-quantum encryption into VPNs, and a lot of unknowns to go with them.
This issue lies not with PQE itself but how it interacts with VPN technology. NIST has spent years analyzing PQE algorithms and wouldn't champion protections that were unsafe.
If a VPN provider has the resources and the confidence to adopt PQE straightaway, tackling the challenges that come with that, then that is commendable.
However, given the lack of first-hand testing and effort required to upgrade VPN infrastructure and protocols, we shouldn't view VPNs who haven't yet adopted PQE as negative.
PQE can become a buzzword and something everyone rushes to achieve. This could come at the expense of proper security and rigorous testing.
It will have to be adopted eventually – VPNs know that – and no reputable provider will shy away from that task.
But the most secure VPNs want to get it right. They want to ensure the most effective and secure protection possible and that is something that can't be rushed.
Disclaimer
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.

George is a Staff Writer at Tom's Guide, covering VPN, privacy, and cybersecurity news. He is especially interested in digital rights and censorship, and its interplay with politics. Outside of work, George is passionate about music, Star Wars, and Karate.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.