Watch out — this official-looking Google email is actually from scammers and can take over your account
This is phishing at its worst

Phishing scams are always trying to trick users into forking over their important information, and while many have telltale signs that give away that its from scammers, a new phishing email going around appears to be from Google itself.
Developer Nick Johnson (via X) was the target of a complex phishing attack that sees scammers send real-looking emails from Google, slipping past Gmail security and appearing to be a signed email from Google. As noted by Johnson, it even appears as a legitimate security alert.
The email was sent from "no-reply@accounts.google.com," the usual address of Google, and is also signed by "accounts.google.com." However, the email was actually sent from "privateemail.com," with the attackers leading users to an also-legitimate-looking support page under "sites.google.com."
The first thing to note is that this is a valid, signed email - it really was sent from no-reply@google.com. It passes the DKIM signature check, and GMail displays it without any warnings - it even puts it in the same conversation as other, legitimate security alerts. pic.twitter.com/GxlFR6ccLGApril 16, 2025
If users click on the link in the phishing email, they will be directed to a fake "Google Support" page that asks to either "upload additional documents" or "view case." According to Johnson, clicking either link leads to a fake sign-in page (also via sites.google.com), asking users to put in their account credentials.
From here, scammers are likely to steal login credentials and take over a user's account. Since the pages use sites.google.com and are made to look identical to official Google pages, it becomes easier for scammers to dupe potential victims into thinking these are real websites — as seeing the domain "google.com" can make it appear legitimate.
How did scammers fake a real Google email?
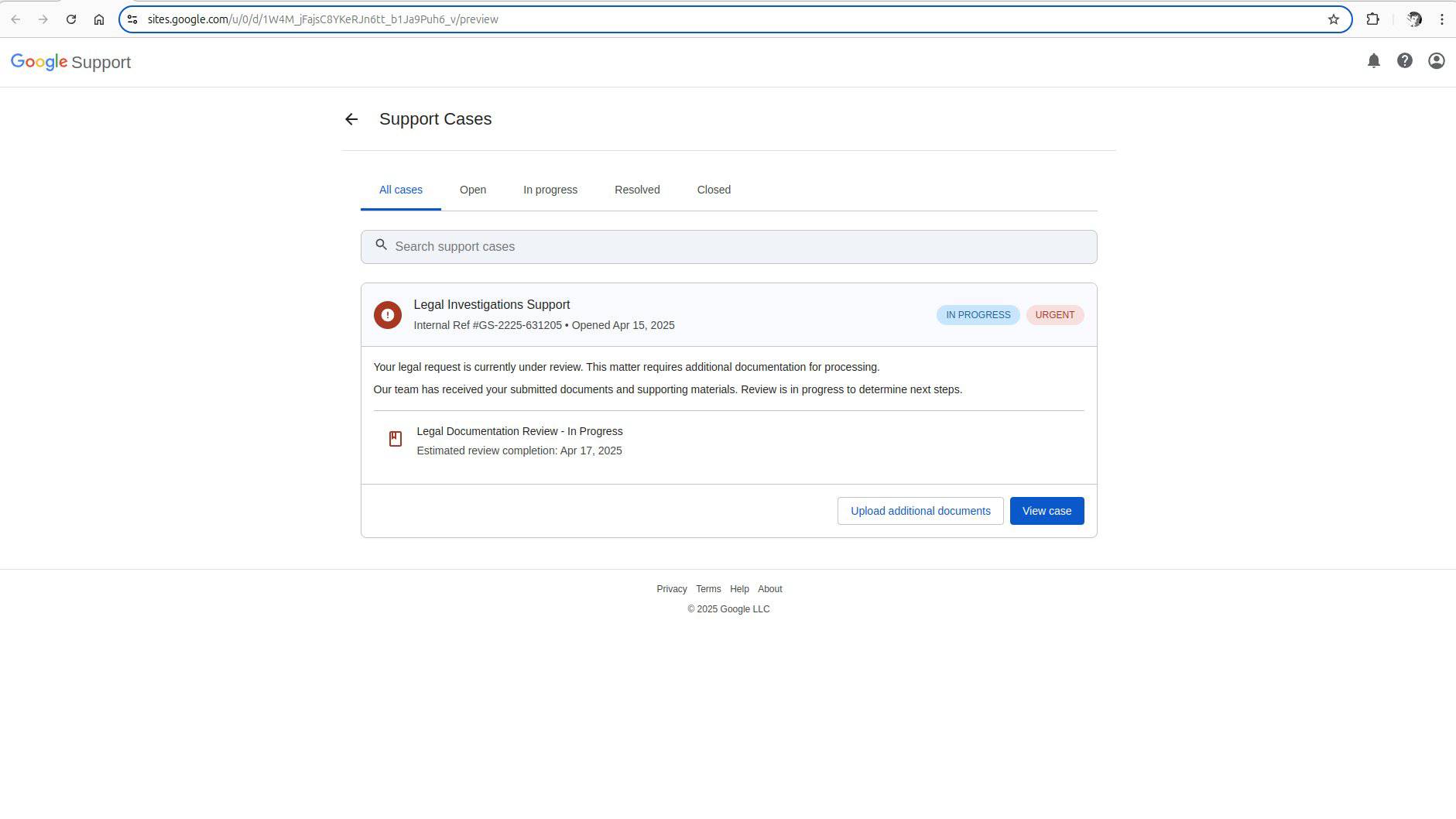
So, how was this phishing email able to get signed off by Google and use its official email? Johnson notes two vulnerabilities, with the first being Google allowing users to host a website with the "google.com" subdomain via "sites.google.com."
The developer states that Google should "disable scripts and arbitrary embeds in Sites," and it is "too powerful a phishing vector."
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Another outlier is the email from the sender, which was signed by "accounts.google.com." To get it signed, the attackers appeared to have registered a domain and linked a Google account to it, then made a Google OAuth app and entered the "entire text of the phishing message."
The attackers then grant the OAuth app access to the Google account, which is signed by Google itself. From there, the phishing message is forwarded to victims, tricking anyone into thinking it's really from Google.
After sending a report to Google (which it initially claimed was intended behaviour), Google is working on a fix for the vulnerability that allows the attackers to form an authenticated phishing email, according to Johnson.
How to avoid phishing emails

Attackers are constantly finding new ways to trick users into falling for phishing scams, and this latest phishing attempt shows that fake emails can be harder to spot. However, there are always methods to avoid malicious emails.
First and foremost, if a company contacts you about an urgent matter, it's best to avoid clicking any links within the email. Check the company's website for any recent alerts, and login to websites by typing in the URL yourself rather than clicking on any links.
Another sign is spotting any misspellings of names in email addresses or website links. In this particular case, this can be harder to spot since the attackers matched the Google's domain names. However, something was slightly off seeing as the "mailed-by" field was forwarded by "privateemail.com."
If an email seems suspicious, always look for inconsistencies. Of course, some can be hard to find, but using the best antivirus software programs can help stop any malicious activity from slipping through the cracks, and it's always best to use two-factor authentication as an extra safeguard.
So, if you see a real-looking email from Google with similar qualities, it's best to avoid it at all costs. If you're wondering how to keep on top of your PC security, check out these 12 computer mistakes you should stop making.
More from Tom's Guide

Darragh is Tom’s Guide’s Computing Editor and is fascinated by all things bizarre in tech. His work can be seen in Laptop Mag, Mashable, Android Police, Shortlist Dubai, Proton, theBit.nz, ReviewsFire and more. When he's not checking out the latest devices and all things computing, he can be found going for dreaded long runs, watching terrible shark movies and trying to find time to game
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
