Chrome extensions with 4 million installs are putting your privacy at risk — how to stay safe
Almost all of these sketchy extensions aren’t even listed on the Chrome Web Store

As the most popular browser by far, there are tons of extensions that let you customize and tweak Google Chrome to your heart’s content. However, a security researcher has discovered dozens of unlisted extensions on the Chrome Web Store with over 4 million installs which raise some serious suspicions.
In a new blog post, Secure Annex’s John Tuckner explains that he first discovered these 35 unlisted Chrome extensions when trying to help an organization cut down on the number of browser extensions it uses overall which is always a good idea and something you too should do from time to time.
What’s surprising about these extensions — besides the fact that they’re unlisted — is that they require the same set of sensitive system permissions. For instance, as Ars Technica points out, they include the ability to interact with web traffic on every site you visit but they can also access a Chrome user’s cookies, manage their tabs and execute scripts.
As we’ve seen in the past, unchecked browser extensions can seriously put both your privacy and security at risk which is why Tuckner’s discovery is so concerning.
Here’s everything you need to know about these sketchy extensions, why you should remove them from Chrome immediately and some tips and tricks on how to protect yourself and your devices from malicious browser extensions that are up to no good.
Delete these extensions right now
Below you’ll find the full list of these suspicious extensions put together by Ars Technica. However, it’s worth noting that this might not be the complete list as there could be other unlisted extensions that follow the same playbook.
- Choose Your Chrome Tools
- Fire Shield Chrome Safety
- Safe Search for Chrome
- Fire Shield Extension Protection
- Browser Checkup for Chrome by Doctor
- Protecto for Chrome
- Unbiased Search by Protecto
- Securify Your Browser
- Web Privacy Assistant
- Securify Kid Protection
- Bing Search by Securify
- Browse Securely for Chrome
- Better Browse by SecurySearch
- Check My Permissions for Chrome
- Website Safety for Chrome
- MultiSearch for Chrome
- Global search for Chrome
- Map Search for Chrome
- Watch Tower Overview
- Incognito Shield for Chrome
- In Site Search for Chrome
- Privacy Guard for Chrome
- Yahoo Search by Ghost
- Private Search for Chrome
- Total Safety for Chrome
- Data Shield for Chrome
- Browser WatchDog for Chrome
- Incognito Search for Chrome
- Web Results for Chrome
- Cuponomia - Coupon and Cashback
- Securify for Chrome
- Securify Advanced Web Protection
- News Search for Chrome
- SecuryBrowse for Chrome
- Browse Securely for Chrome
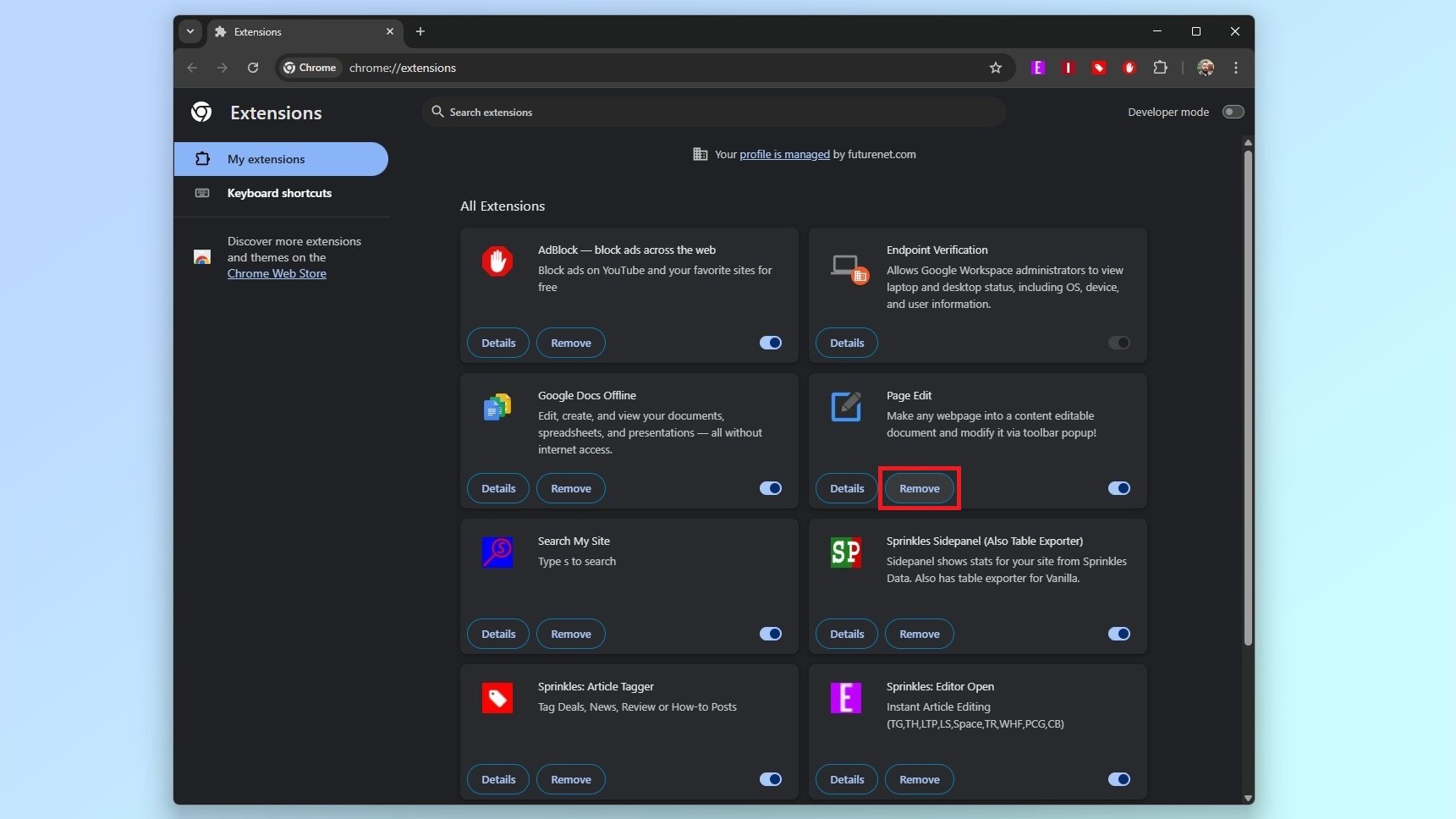
To remove the extensions above from Chrome, click on the browser’s three dot menu in the upper right corner. About halfway through the menu that appears, you’ll find Extensions. Click on it and then head to Manage Extensions to see a full list of the browser extensions you have installed.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
While you can search through them manually, there’s also a search box at the top if you know the name of the extensions you want to remove.
When you find an extension you no longer want or use, click the Remove button at the bottom of its name and a pop-up menu will appear where you’ll click Remove again. This will remove the extension from your browser across all of your devices.
Requesting sensitive permissions

All of the extensions listed above raised a big red flag for Tuckner based on the permissions they requested upon installation. These permissions include Tabs, Cookies, WebRequest, Storage, Scripting, Alarms and Management API.
Tabs allows an extension to manage and interact with browser windows in Chrome while Cookies lets an extension set and access stored browser cookies. WebRequest gives these extensions the ability to intercept and modify any web requests your browser makes and Storage gives an extension the ability to store small amounts of data inside your browser persistently.
The two most alarming permissions requested by the extensions in question are Scripting and Management API. While Scripting allows these extensions to inject new JavaScript into webpages, the Management API works with other permissions like webRequest and allows for an extension to interact with all of your browsing activity.
If you’ve read my stories on how hackers and other cybercriminals often weaponize browser extensions in their attacks, then you’ll know just how serious giving an extension access to all of these sensitive permissions can be.
During his investigation though, Tuckner found some other red flags in these unlisted extensions. For instance, much of their code is highly obfuscated or hidden, which makes them harder to analyze.
ikewise, all but one of them are unlisted on the Chrome Web Store and in order to download them, you need to know their exact URLs. It’s also worth noting that 10 of these extensions have been given a “Featured” designation by Google which is typically only used for verified developers.
Tuckner tried his best to analyze exactly what these extensions did but it ran into difficulties thanks to their obfuscated code and other steps taken by their developers to hide their behavior.
It’s worth noting that he didn’t find any proof that these extensions are malicious but he came across enough red flags to assume that they may include some kind of spyware or infostealer.
How to stay safe from malicious browser extensions

Just like with the apps on your phone, the easiest way to stay safe from malicious browser extensions is to limit the number of extensions you have installed. This is exactly what Tuckner was trying to do for the organization he was working for when he discovered these unlisted extensions.
Before installing any extension, you first want to ask yourself if you really need the extra features and functionality it promises. You might be able to find a web app or another service that can do the exact same thing without putting your browser, data and devices at risk.
If you do really need a particular extension, you want to take a close look at its ratings and reviews before installing it. However, since these can be faked, it’s always a good idea to look for external reviews too.
As good extensions can go bad when injected with malicious code after being taken over by hackers, you also want to routinely audit all of the extensions you have installed. If you haven’t used one in a while, it’s best to remove it from your browser.
As for protecting your devices from malicious extensions, you want to make sure you’re using the best antivirus software on your PC and the best Mac antivirus software on your Apple computer. If a bad extension is spreading malware, your antivirus software will catch the infection before it can harm your computer or steal your data.
In the same way that malicious apps can give hackers a foothold into your phone, so too can browser extensions with your computer. This is why it’s up to you to carefully evaluate each extension you install and to take the time to go through your installed extensions periodically to remove the ones you no longer use.
More from Tom's Guide
- Scammers are impersonating QuickBooks in last-minute tax phishing scam and it's stealing financial data
- Security spring cleaning — 7 things you should do now to avoid getting hacked
- Hackers are using fake Google Play Store pages to infect Android phones with a dangerous trojan — how to stay safe

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
 Club Benefits
Club Benefits





