Apple Find My hack turns any Bluetooth device into a secret AirTag — what we know
Well this is absolutely terrifying
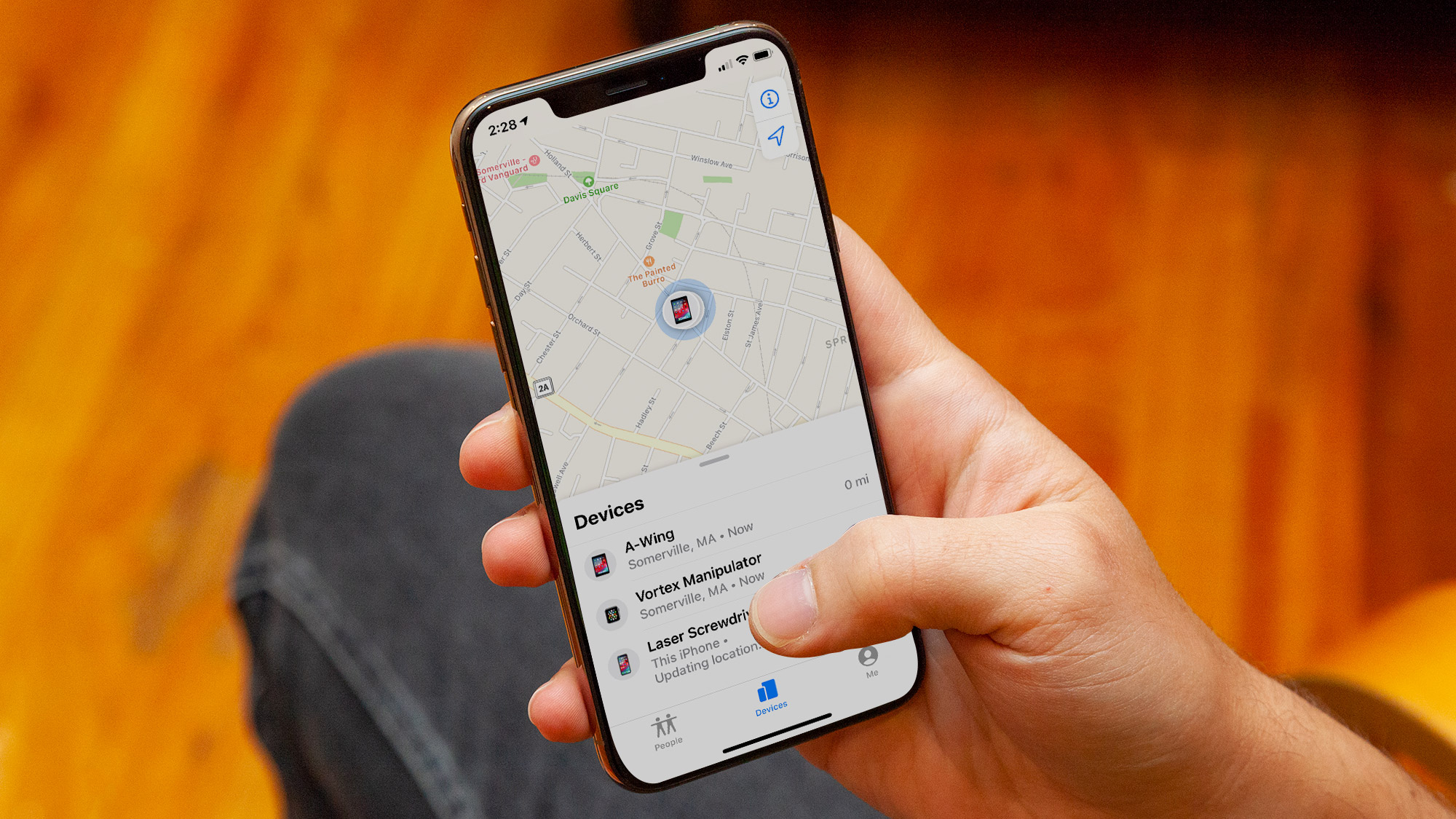
Apple’s Find My network is an incredibly useful bit of software, giving users a way to track down their missing devices and accessories — including AirTags, iPhones and even certain kinds of headphones.
Unfortunately, it may not have been quite as secure as Apple had hoped, thanks to a serious exploit that was uncovered by researchers at George Mason University.
According to researchers this exploit would have allowed hackers to turn any Bluetooth device into an AirTag "without the opener ever realizing it." This would essentially let hackers track users through the Find My network without them realizing, and without the usual protections Apple has in place against AirTag stalking.
How this exploit works

Normally AirTags are designed to change their Bluetooth address based on a specific cryptographic key. Unfortunately researchers were able to develop a system that could find keys for those Bluetooth addresses, aided by “hundreds” of GPUs that could calculate a key match.
Dubbed “nRootTag,” this exploit had a frighteningly high success rate of 90% and was able to track down devices “within minutes.”
One experiment even saw researchers track the location of a computer within 10 feet, and they were later able to trace a moving e-bike as it was ridden on city streets. Another experiment let them recreate the path of a person’s flight by tracking a games console.
Proximity wasn’t a factor either, with hackers able to do all this from thousands of miles away.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
As terrifying as it is that hackers could track your location so easily (or sell access to others), researchers pointed out that it could go much further than that. “While it is scary if your smart lock is hacked, it becomes far more horrifying if the attacker also knows its location. With the attack method we introduced, the attacker can achieve this.”
What happens next?

The George Mason team informed Apple of this exploit last July. Apple acknowledged the work of the team in the iOS 18.2 release notes, and told Tom's Guide it has "hardened" the Find My network to resist "inappropriate use" like this. That update was released on December 11 2024.
Apple also emphasized that the issue is not a vulnerability with Apple products. The exploit was used to track the location of Linux, Windows and Android systems through the Find My network without proper authorization, but not Apple.
It's unclear whether this exploit has been utilized by bad actors right now. However, researchers noted that a true fix to the problem could take years to develop, since updates can't be forced on at-risk customers. Researchers advise that users should stay cautious about granting apps Bluetooth permissions to try and avoid this kind of thing happening to them.
They should also keep software up to date and “consider privacy-focused operating systems for better protection against prying eyes.”
More from Tom's Guide

Tom is the Tom's Guide's UK Phones Editor, tackling the latest smartphone news and vocally expressing his opinions about upcoming features or changes. It's long way from his days as editor of Gizmodo UK, when pretty much everything was on the table. He’s usually found trying to squeeze another giant Lego set onto the shelf, draining very large cups of coffee, or complaining about how terrible his Smart TV is.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
