This dangerous new Windows malware hides from your antivirus while impersonating a popular PC brand
The CoffeeLoader malware is posing as a popular Asus utility online

A new malware family is targeting Windows users by impersonating an ASUS utility to deliver malicious code – but perhaps most concerningly, it uses multiple techniques to hide itself from the best antivirus software and other security tools.
As reported by Cybernews, the CoffeeLoader malware, identified by researchers from the cybersecurity firm Zscaler, mimics Asus' Armoury Crate. This utility is used to set up and manage the best gaming laptops from Asus as well as the company's other peripherals.
The researchers say CoffeeLoader originated around September 2024 and has several similarities to the SmokeLoader malware.
Once the malware has infected a system, it delivers several infostealers – among them the well known Rhadamanthys Infostealer. From there, it uses a number of tricks to stay undetected by antivirus programs and other security tools.
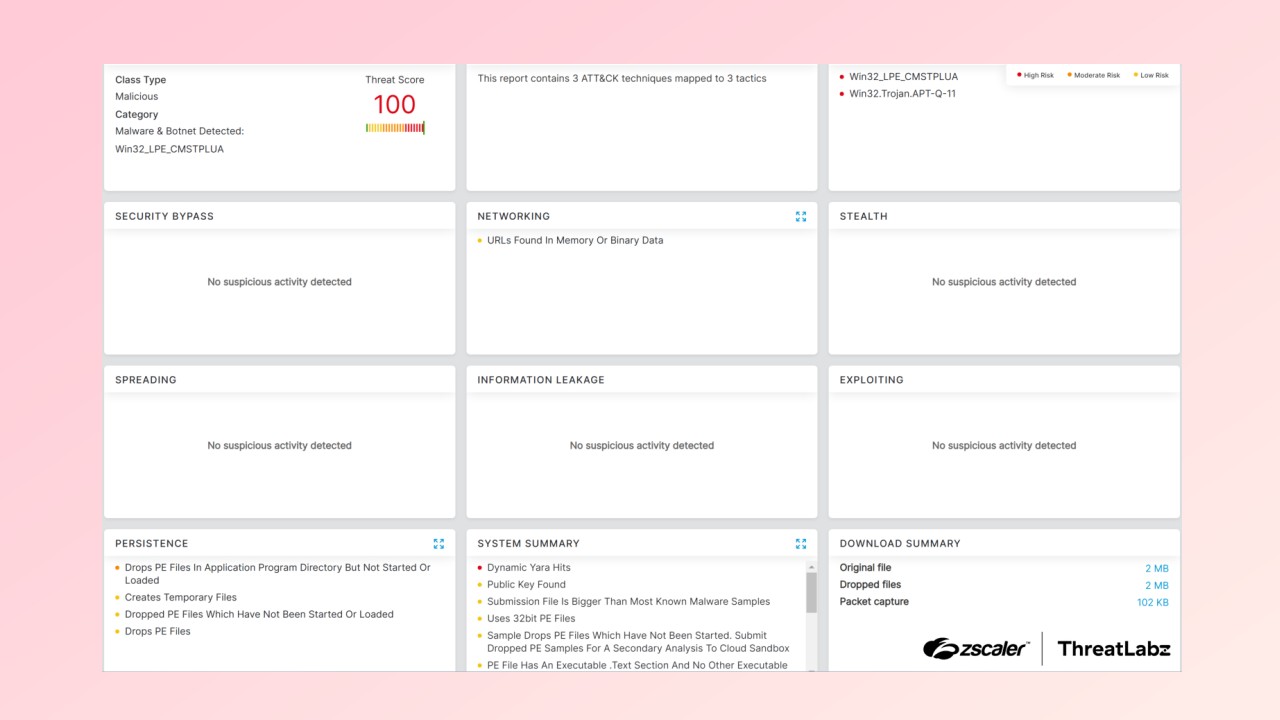
For example, it will run code on the infected systems GPU instead of on the computer’s CPU. Since most security programs and antivirus scanners don’t check the GPU, the malware stays hidden.
Another way it covers its tracks is by using a technique called Call Stack Spoofing. While most programs leave behind a trail of function calls, the CoffeeLoader malware can change its own trail in order to make it appear harmless. This keeps it from being recognized as suspicious or harmful by any security software or antivirus programs.
It can also “play dead” or use a technique called Sleep Obfuscation. Basically, when it’s not active, it will “lock” itself up into an encrypted form in the computer's memory; if an antivirus tool scans the memory it won’t find anything readable.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
The CoffeeLoader malware also accesses unusual pathways, for example, Windows Fibers, in order to evade detection. Windows Fibers are a way in which programs handle multitasking which allows a program to switch between tasks on its own instead of relying on Windows. The CoffeeLoader can then use these fibers to evade detection since security tools may not monitor them.
How to stay safe

In order to keep your data and your Asus gear safe from the CoffeeLoader malware, you want to ensure that you're downloading Armoury Crate from the company's official site and you can find the download page here.
Hackers often impersonate popular brands and their software as a means to infect unsuspecting users with malware. This is why you always want to go directly to a company's site instead of trusting download links that appear online in forums or even as ads in search results.
Just like anyone else, hackers can easily purchase ad space online and then by crafting a convincing lookalike page, they can trick unsuspecting users into downloading malware onto their PCs through their malicious ads.
Now that we've seen CoffeeLoader impersonate Asus, it's likely that the hackers behind this campaign will try to pose as other popular utilities to recreate this attack. This is why you need to practice good cyber hygiene and remain vigilant online, especially when downloading new software.
More from Tom's Guide

Amber Bouman is the senior security editor at Tom's Guide where she writes about antivirus software, home security, identity theft and more. She has long had an interest in personal security, both online and off, and also has an appreciation for martial arts and edged weapons. With over two decades of experience working in tech journalism, Amber has written for a number of publications including PC World, Maximum PC, Tech Hive, and Engadget covering everything from smartphones to smart breast pumps.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
