This Android malware can steal all your photos and texts without being opened — how to stay safe
The XLoader malware just got a big upgrade that makes it even more dangerous

Just when you thought the state of Android malware couldn’t get any worse, a new version of XLoader has been discovered that can automatically launch on infected smartphones.
As reported by BleepingComputer, XLoader is a malware strain that has been used to target owners of the best Android phones in the U.S., U.K., Germany, France, Japan, South Korea and Taiwan in the past. Now though, security researchers at McAfee have discovered a new XLoader variant that can launch immediately after it’s installed.
Normally with Android malware spread through malicious apps or suspicious downloads, a potential victim first needs to open the app or the file containing it before it can run on their phone. This isn’t the case with XLoader anymore as it can now run in the background while extracting all sorts of sensitive data including photos, text messages, contact lists, hardware details and more from compromised devices.
Since it first appeared in 2015, XLoader has gone through a number of different revisions that have boosted its capabilities and have even allowed the malware to target Macs. Here’s what you need to know about this new Android threat and the steps you need to take to protect yourself from it.
Impersonating Google Chrome
So how does the XLoader malware end up on your Android smartphone? According to McAfee’s report, it’s usually distributed via malicious links sent via text messages. These links are shortened to help avoid detection and if you get a text from an unknown number — or even from a friend — with a shortened link like this, it’s best to avoid opening it.
These suspicious links lead to Android APK files which are used to sideload apps instead of installing them directly from the Google Play Store. Though convenient, sideloading apps is another thing to avoid if you don’t want to end up with a nasty malware infection.
If a potential victim clicks on the link, downloads the APK and decides to install it, this variant of the XLoader malware can launch on its own without any interaction from you whatsoever. However, if they do decide to launch this mysterious app sent to them by a stranger, XLoader has another clever trick up its sleeve to avoid detection while gaining further access to their smartphone.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
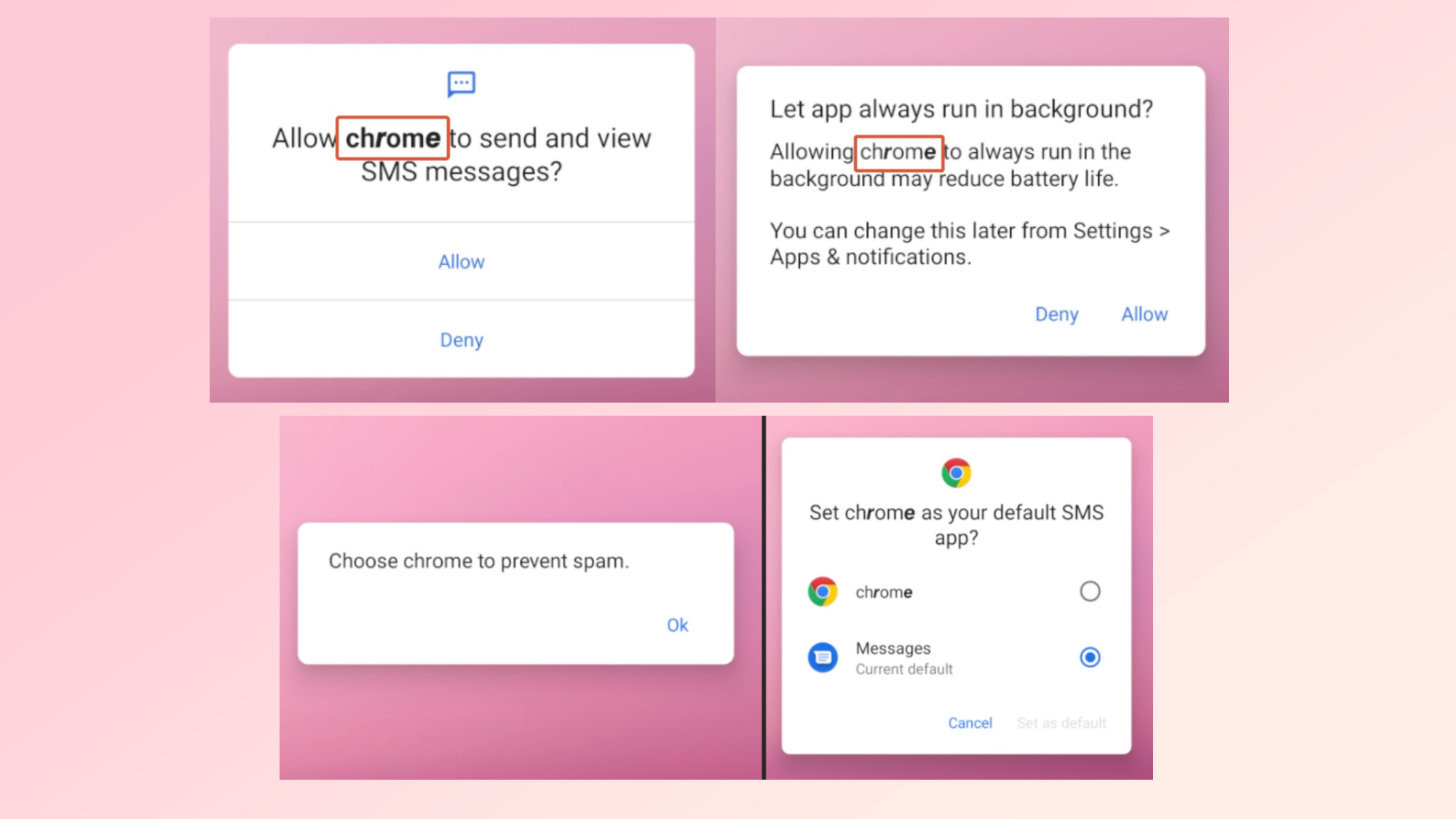
The malware impersonates Google Chrome in order to trick victims into enabling risky permissions such as sending and viewing text messages or being able to run in the background. It goes a step further by asking users if they want to set it as the default SMS app under the guise that it will help prevent spam.
During this process, pop-up messages in English, Korean, French, Japanese, German and Hindi are displayed on a victim’s smartphone to make the app appear more credible, despite what their native language may be.
If you thought XLoader was done being clever, you’d be wrong. The malware is also able to extract phishing messages and malicious URLs from Pinterest profiles which are then sent to your infected smartphone. Once again, this to avoid detection by the best antivirus software and other security checks. If for some reason the malware is unable to access Pinterest, it uses hardcoded phishing messages that inform potential victims that there is something wrong with their bank account and that they need to take action immediately.
How to stay safe from Android malware

Avoiding Android malware like XLoader is easy enough to do but not having your smartphone infected requires that you be a bit more careful online.
Besides not sideloading apps or opening shortened URLs in text messages or any message for that matter, you also want to be very cautious when granting permissions to the apps you install. Does that ruler app really need to access your text messages and internal storage? I didn’t think so.
Limiting the number of apps you have installed on your Android phone can also help as even good apps can go bad when injected with malicious code. Also, you’re better off sticking to apps from reputable developers instead of just installing any new app you find online. Hackers and other cybercriminals are great at exploiting trends and what’s popular, which is one of the ways they trick potential victims into falling for their attacks.
Regardless of which Android smartphone you pick up, there’s a very high chance that it will come with Google Play Protect pre-installed. You want to make sure that this app is enabled though as it can scan all of your existing apps and any new ones you download for malware. Likewise, for additional protection, you may also want to consider installing one of the best Android antivirus apps to run alongside it.
XLoader has been constantly evolving since it was first released in 2015 and it’s highly likely we’ll see new variants of this malware strain in the future with improved capabilities to better help it avoid detection. As such, it’s up to you to be careful when downloading new apps and opening links sent in messages and emails.
More from Tom's Guide

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
