Macs under threat from info-stealing malware — don’t fall for this Microsoft Teams scam
New malvertising campaign uses Teams to spread the Atomic Stealer malware

When looking for new software online, you never want to click on the first search result as you could be dealing with fake ads spreading dangerous malware.
As we saw with the Arc browser in a recent Poseidon campaign, hackers are once again using fake ads to direct unsuspecting Mac users to malicious sites hosting malware. This time though, they’re spreading the Atomic Stealer malware which can steal passwords from web browsers and even Apple Keychain as well as cryptocurrency through fake Microsoft Teams downloads.
Here’s everything you need to know about this new campaign along with some tips on how you can keep your Mac virus free.
Hiding in plain sight
While cybercriminals and other hackers have traditionally used communication tools like Zoom, Webex or Slack as a lure, this time around, they’re using Microsoft Teams as the software giant’s workplace chat app has become quite popular.
In a new report, security researchers at Malwarebytes explain how a search for “Microsoft Teams for Mac” led to a fake ad being displayed at the top of Google Search. They believe this ad was paid for by a compromised Google ad account.
Even though the ad itself shows microsoft[.]com as the URL at the top, clicking on it doesn’t take you to Microsoft’s official site. Instead, doing so takes you to a fake landing page with the URL teambusiness[.]org that impersonates the actual Microsoft Teams site.
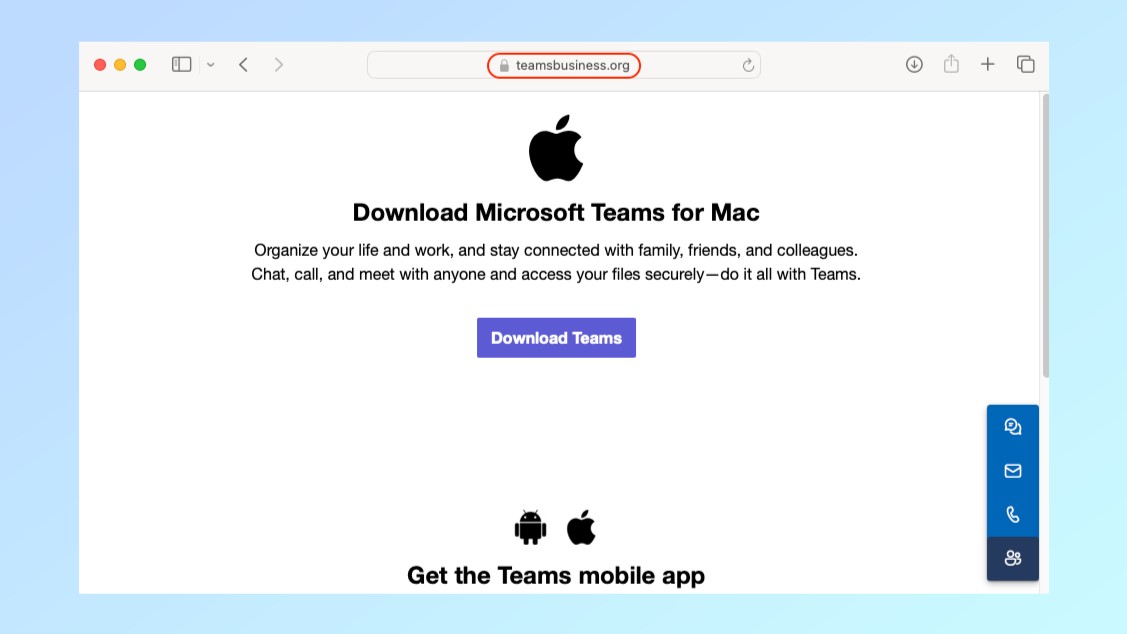
This incredibly simple site has Apple’s logo at the top with a brief description of the app and what it does. Underneath is a “Download Teams” button that when clicked, downloads a malicious Mac app.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
If you frequently use one of the best MacBooks, you might immediately be able to tell that something is off as the downloaded file (MicrosoftTeams_v.(xx).dmg) instructs potential victims to open it with a right click. This is a big red flag as any app that asks you to install it in this manner is actually trying to bypass Apple’s built-in protection mechanism for unsigned installers.
From here, the malicious app requests that the user enters their password and grants access to the file system. However, doing so allows the Atomic Stealer malware to grab Apple Keychain passwords and other important files on the now compromised Mac. If you let things get this far, the malware then proceeds to extract sensitive data from your Apple computer and then send it back to the hackers behind this campaign.
How to stay safe from Mac malware

As I mentioned before, the first and most important thing you can do to stay safe from fake ads spreading malware is actually to scroll further down the page when searching for new software online. Just like you or I, hackers too can easily buy ad space but for much more nefarious purposes.
Taking the extra second or so to scroll down to a company’s actual website could save you from falling victim to a nasty malware infection and perhaps even having your identity stolen by hackers.
Although your Mac does come with built-in antivirus software in the form of XProtect, you might also want to consider using one of the best Mac antivirus software solutions alongside it. Paid antivirus software is updated more regularly plus, you often get extras like a VPN or password manager to help you stay safe online.
Over the past few years, we’ve seen hackers routinely use fake ads in their malware campaigns due to how successful this tactic can be. Fortunately, if you scroll down past the ads, you can avoid falling victim to this and other similar campaigns designed to infect your Mac with password-stealing malware.
More from Tom's Guide
- Apple issues urgent spyware warning for iPhone users in 98 countries
- The FBI now recommends using an ad blocker — here’s why
- Hackers are using Facebook ads to infect Windows PCs with malware

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
