Chrome security alert — clicking this error will open the malware floodgates on your PC
So-called “fixes” for this fake error actually install dangerous malware

Hackers love to trick their victims into doing things they wouldn’t do otherwise, and a new malware campaign currently making the rounds online is the perfect example of this.
As reported by BleepingComputer, hackers are using fake Google Chrome and Microsoft Word errors to trick potential victims into running malicious PowerShell “fixes” that actually install malware.
This particular campaign is so effective that multiple hacker groups (including the ones behind ClearFake, a new group called ClickFix and the group TA571) are using it in their attacks.
Here’s everything you need to know about this new malware campaign, and how you can avoid falling victim to the social engineering it uses to get you to infect your own Windows PC with malware.
From fix to fail
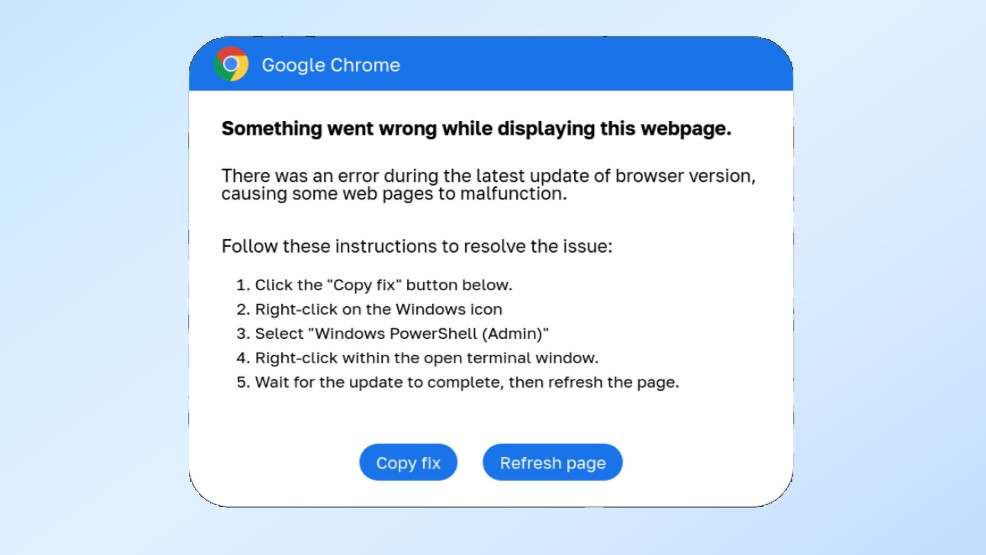
Just like with previous ClearFake campaigns, this new one uses overlays to display fake Chrome and Word errors. Potential victims are then prompted to click a copy button which contains a "fix" for these fake errors. This copied code then needs to be pasted into either a Windows Run dialog or a Powershell prompt.
In a new report highlighting all of the different attack chains used in this campaign, Proofpoint explains that compromised websites which load a malicious script hosted on the blockchain using Binance’s Smart Chain contracts are also used to infect vulnerable Windows PCs with malware.
This script performs several checks before displaying a fake Google Chrome warning that says there’s a problem displaying the webpage in question. From here, a dialog prompts visitors to install a "root certificate" by copying a PowerShell script and then running it in a Windows PowerShell (Admin) console.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
When executed, this PowerShell script performs more checks to make sure that the device in question is a valid target before it downloads additional payloads, including an info-stealing malware.
Finally, there’s also an email-based infection chain that uses HTML attachments which resemble Word documents. They prompt potential victims to install a “Word Online” extension to view a document but like the other attack chains used in this campaign, a “fix” involving a PowerShell command also has to be copied and then pasted into PowerShell.
In this attack chain, the PowerShell command downloads and executes either an MSI file or a VBS script which infects the target PC with either the Matanbuchus or DarkGate malware.
How to stay safe from Windows malware

All three of the different attack chains used in this campaign rely on the fact that most Windows users aren’t aware of the dangers associated with running unknown PowerShell commands on their PCs. This is why you should never copy and execute code unless you absolutely know what you’re doing.
Likewise, you also want to ensure that Windows Defender is enabled and running on your PC as it can catch the malware dropped by these malicious PowerShell scripts. If you want even more protection though, you should also consider using one of the best antivirus software suites alongside Microsoft’s built-in security tools, especially as they often come with extras like a VPN or password manager.
As for campaigns like this one that use overlays to trick potential victims, you want to stop and take a minute to think things over before doing anything online. Hackers often try to instill a sense of urgency in their attacks to get you to act without thinking. Instead, you should read over any messages carefully and try to look them up online to see whether or not they’re genuine. Even if you don’t find any info online, the best course of action is to do nothing in most cases.
Overlay attacks are very effective as they often appear as if they’re coming from the software you’re currently using. However, by learning how they work and knowing what to look out for, you can keep your devices and your data safe.
More from Tom's Guide
- Urgent Windows security flaw lets hackers infect your PC over Wi-Fi
- Hackers are now using emoji to speed up their cyberattacks
- Scammers are impersonating this government agency to steal your cash

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
