Dangerous new Android banking trojan uses fake Google Play updates to take over your phone — how to stay safe
This versatile new banking trojan can give hackers complete control over your phone

Keeping your mobile devices and their apps updated is one of the most important things you can do to stay safe from the latest cyber threats. However, as hackers are aware of this too, they often use fake updates as a means to infect your devices with malware, as is the case with a new Android banking trojan currently making the rounds online.
According to a blog post from the cybersecurity firm Cyble, its researchers have discovered a new Android banking Trojan called Antidot, not to be confused with the Brokewell malware the team discovered last month.
Once installed on one of the best Android phones, the Antidot malware can collect contacts and text messages, harvest credentials, lock and unlock the device, forward calls and more which is why this new banking trojan is so dangerous.
Here’s everything you need to know about the Antidot banking trojan along with some steps you can take to keep your own Android phone safe from this and other malware strains.
Impersonating Google Play
Google Play is one of the most important apps on your Android phone, as it’s where you download new apps from as well as updates for your existing apps. It’s the kind of app you definitely want to keep up to date, which is why the hackers behind this campaign have decided to impersonate it.
Like with other malware campaigns, this one uses phishing messages to trick users into installing it. Unsuspecting users may receive an email — or more likely a text message — that appears to come from Google telling them they need to update Google Play. The message also contains a malicious link that leads them to the malware itself which needs to be sideloaded as an APK file.
What’s particularly interesting about this campaign is that the fake Google Play update pages it uses have been crafted in several different languages including English, German, French, Spanish, Russian, Portuguese and Romanian. This lets the hackers behind the Antidot banking trojan target a wide range of Android users from multiple countries at the same time without having to tweak the campaign itself for each country.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
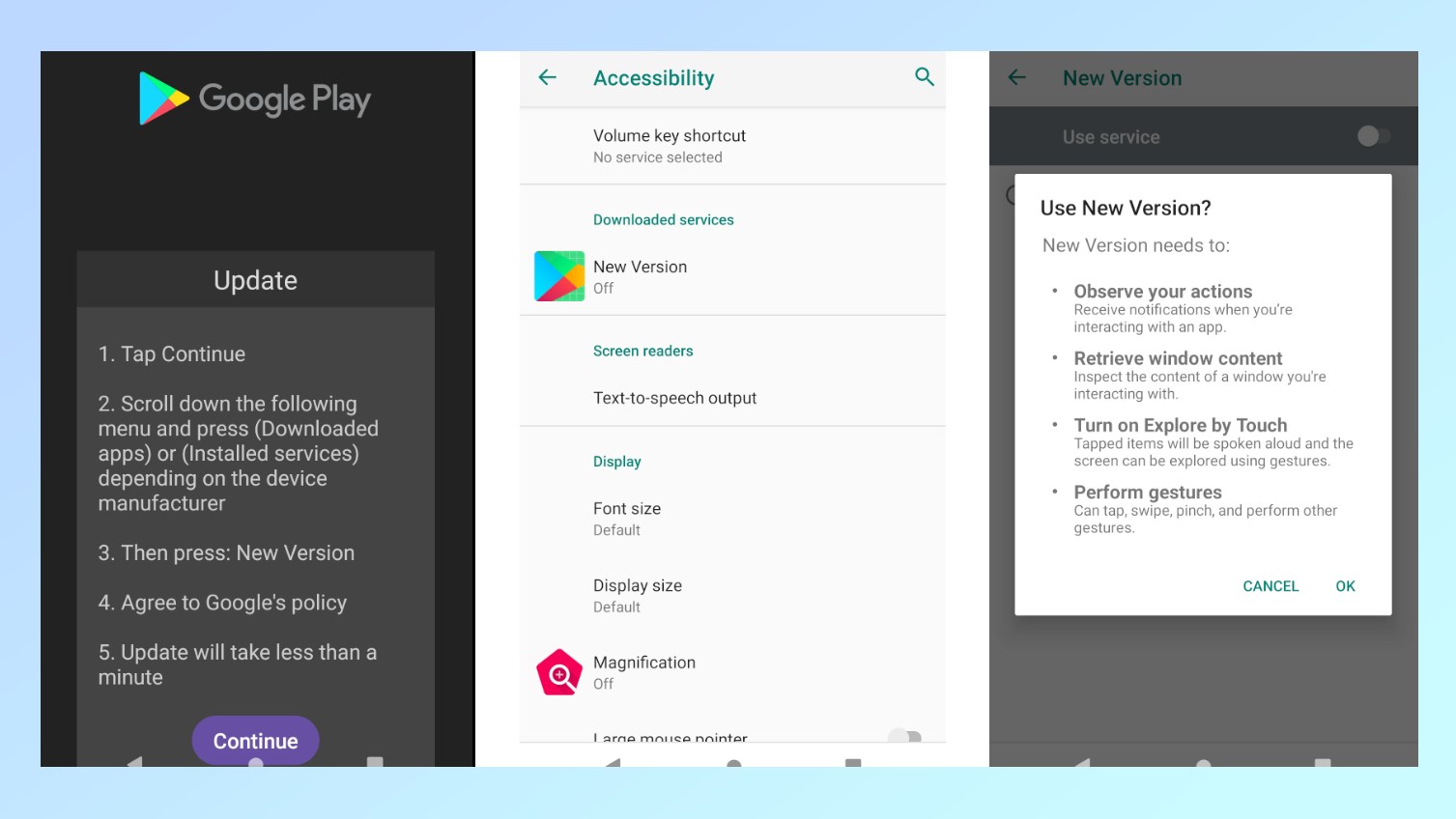
Once installed, the malware displays another fake update page that’s used to trick victims into giving it access to Android’s Accessibility Settings. Getting access to these services is what allows Antidot to gain complete control over a vulnerable Android smartphone as they can be abused to see what’s on a victim’s screen as well as to interact with their apps and other data.
From overlay attacks to keylogging

The Antidot malware and other banking trojans make use of a hacker-controlled Command and Control (C&C) server to carry out their malicious actions. This server lets the hackers communicate directly with an infected device and tell the malware what to do.
From here, the Antidot malware has a total of 35 different commands it can perform from unlocking an infected device to making calls, collecting and sending text messages, sending out push notifications, locking the device and more. This banking trojan can also copy text from an infected phone’s clipboard.
In order to steal passwords and other credentials though, Antidot uses overlay attacks in a similar way to other popular banking trojans like Ermac, Chameleon and Brokewell. For those unfamiliar with overlay attacks, here’s how they work. When you open a banking app on your phone, the malware loads an HTML phishing page that’s designed to look just like that particular app and this page is overlaid on top. Then when you enter your credentials to log in, they are captured by hackers who can then drain your bank account, commit fraud or even steal your identity with enough info.
If there are banking or other financial apps that the malware doesn’t have an overlay ready for, keylogging is used to capture everything a victim types on an infected Android smartphone including their passwords.
How to stay safe from Android malware

Android malware like Antidot can be very dangerous since so much personal and financial information is now stored on our phones. However, by taking the right steps and implementing certain safeguards, you can avoid falling victim to it.
For starters, you only want to install new apps from the Google Play Store or other official app stores like the Amazon Appstore or the Samsung Galaxy Store. While convenient and fast, sideloading apps puts you and your devices at risk, so it’s best to avoid this altogether.
At the same time, you want to avoid clicking on any links in emails or text messages sent from unknown senders to your smartphone. Hackers will often send messages that try to instill a sense of urgency with a link for you to click at the bottom. If you read through the message and get worked up about what it says, like how you need to update Google Play immediately in this case, you’re more likely to click on the link and do exactly what the hackers want you to. Also keep in mind that hackers can pose as your friends and family to trick you as well, like we saw with the recent ‘Look who died’ scam on social media.
To stay safe from Android malware, you should make sure that Google Play Protect is enabled on your smartphone. This free antivirus app from Google scans all of your existing apps and any new ones you download for malware. However, for additional protection and access to some useful extras like a VPN or password manager, you should also consider downloading one of the best Android antivirus apps.
Due to how much data and money they can bring in for hackers, banking trojans aren’t going anywhere anytime soon. This is why it’s up to you to carefully examine the messages you receive and practice good cyber hygiene.
More from Tom's Guide

Anthony Spadafora is the managing editor for security and home office furniture at Tom’s Guide where he covers everything from data breaches to password managers and the best way to cover your whole home or business with Wi-Fi. He also reviews standing desks, office chairs and other home office accessories with a penchant for building desk setups. Before joining the team, Anthony wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
-
D8Mach "If you purchase a product or register for an account through a link on our site, we may receive compensation"Reply
Assuming those links are real. Eh?
